-
GRE TRAINING FOR EXCELLENT SCORES
 GRE exam aims to measure verbal reasoning, quantitative reasoning, analytical writing, and critical thinking skills that have been acquired over a long period of time and that are not related to any specific field of study. Read more
GRE exam aims to measure verbal reasoning, quantitative reasoning, analytical writing, and critical thinking skills that have been acquired over a long period of time and that are not related to any specific field of study. Read more
-
IELTS (International English Language Testing System)
 IELTS is a course designed to assess the English language ability of people who intend to study or work where English is the language of communication. Candidates are tested in LISTENING, READING, WRITING and SPEAKING. . Read more
IELTS is a course designed to assess the English language ability of people who intend to study or work where English is the language of communication. Candidates are tested in LISTENING, READING, WRITING and SPEAKING. . Read more
-
TOEFL CLASSES FOR BEST SCORES
 ITest of English as a Foreign Language (TOEFL, /?to?f?l/, toh-f?l) is a standardized test to measure the English language ability of non-native speakers wishing to enroll in American universities. . Read more
ITest of English as a Foreign Language (TOEFL, /?to?f?l/, toh-f?l) is a standardized test to measure the English language ability of non-native speakers wishing to enroll in American universities. . Read more
-
SAT COMPLETE PREPARATION GUIDE
 The SAT is a standardized test widely used for college admissions in the United States. It was first introduced in 1926, and its name and scoring have changed several times, being originally called the Scholastic Aptitude Test, then the Scholastic Assessment Test, then the SAT I: Reasoning Test, then the SAT Reasoning Test, and now simply the SAT. Read more
The SAT is a standardized test widely used for college admissions in the United States. It was first introduced in 1926, and its name and scoring have changed several times, being originally called the Scholastic Aptitude Test, then the Scholastic Assessment Test, then the SAT I: Reasoning Test, then the SAT Reasoning Test, and now simply the SAT. Read more
-
GMAT Complete Course
 GMAT is a registered trademark of the Graduate Management Admission Council. More than 5,900 programs offered by more than 2,100 universities and institutions use the GMAT exam as part of the selection criteria for their programs. Business schools use the test as a criterion for admission into a wide range of graduate management programs, including MBA, Master of Accountancy.. Read more
GMAT is a registered trademark of the Graduate Management Admission Council. More than 5,900 programs offered by more than 2,100 universities and institutions use the GMAT exam as part of the selection criteria for their programs. Business schools use the test as a criterion for admission into a wide range of graduate management programs, including MBA, Master of Accountancy.. Read more
-
PTE Complete Course
 The Pearson Test of English Academic (PTE Academic) is an English language test designed to assess the readiness of non-native English speakers to participate in a university-level English language instruction program. Pearson created PTE Academic in response to demand from institutions, government and other organizations for a more accurate way of testing non - native English language students who enter the English-speaking academia world Read more
The Pearson Test of English Academic (PTE Academic) is an English language test designed to assess the readiness of non-native English speakers to participate in a university-level English language instruction program. Pearson created PTE Academic in response to demand from institutions, government and other organizations for a more accurate way of testing non - native English language students who enter the English-speaking academia world Read more
-
LANGUAGE AND SOFT SKILLS TRAINING
 Soft skills is a term often associated with a person's "EQ" (Emotional Intelligence Quotient), the cluster of personality traits, social graces, communication, language, personal habits, interpersonal skills, managing people, leadership, etc. that characterize relationships with other people. Soft skills contrast to hard skills, which are generally easily quantifiable and measurable (e.g. software knowledge, basic plumbing skills). . Read more
Soft skills is a term often associated with a person's "EQ" (Emotional Intelligence Quotient), the cluster of personality traits, social graces, communication, language, personal habits, interpersonal skills, managing people, leadership, etc. that characterize relationships with other people. Soft skills contrast to hard skills, which are generally easily quantifiable and measurable (e.g. software knowledge, basic plumbing skills). . Read more
-
Cardiac Catheterization
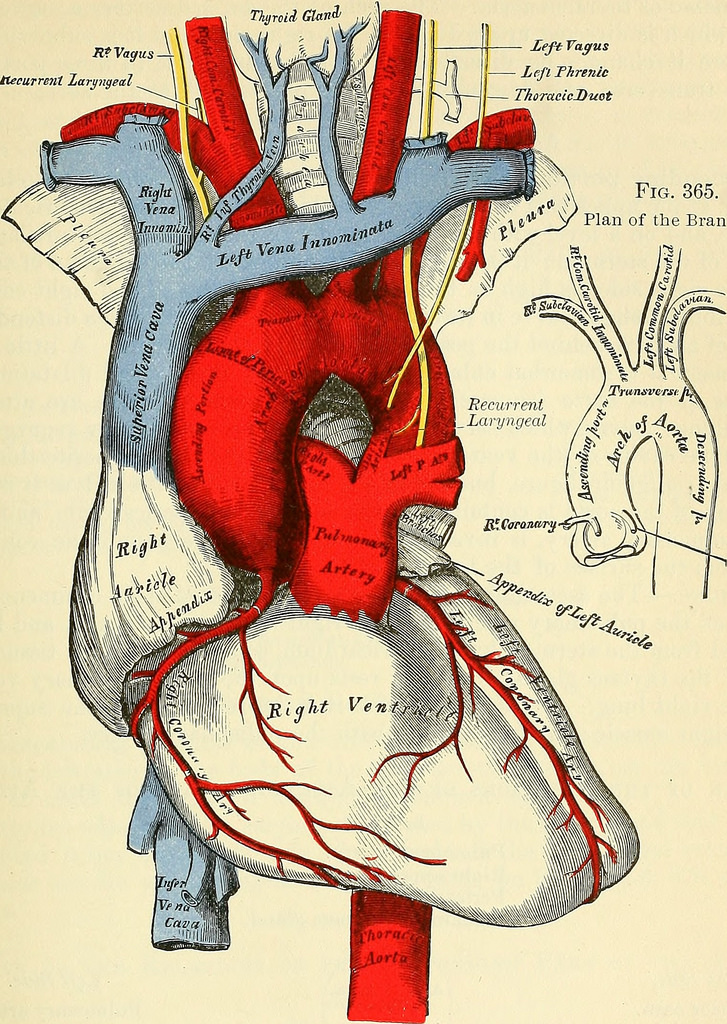 The cardiac catheter is an important tool, whose use over the latter half of the twentieth century has provided unprecedented improvements in the clinical care of patients with heart disease while extending our understanding of circulatory physiology and vascular pathobiology. In the process, it has defined two new areas of special expertise within our broader parent specialty: invasive and interventional cardiology. Read more
The cardiac catheter is an important tool, whose use over the latter half of the twentieth century has provided unprecedented improvements in the clinical care of patients with heart disease while extending our understanding of circulatory physiology and vascular pathobiology. In the process, it has defined two new areas of special expertise within our broader parent specialty: invasive and interventional cardiology. Read more
-
Certified Ethical Hacker Study Guide
 Certified Ethical Hacker Study Guide. This book is part of a family of premium-quality Sybex books, all of which are written by outstanding authors who combine practical experience with a gift for teaching.
Sybex was founded in 1976. More than 30 years later, we’re still committed to producing consistently exceptional books. With each of our titles, we’re working hard to set a new standard for the industry. From the paper we print on, to the authors we work with, our goal is to bring you the best books available.
I hope you see all that reflected in these pages. I’d be very interested to hear your comments and get your feedback on how we’re doing. Feel free to let me know what you think about this or any other Sybex book by sending me an email at nedde@wiley.com. If you think you’ve found a technical error in this book, please visit http://sybex.custhelp.com. Customer feedback is critical to our efforts at Sybex.
Read more
Certified Ethical Hacker Study Guide. This book is part of a family of premium-quality Sybex books, all of which are written by outstanding authors who combine practical experience with a gift for teaching.
Sybex was founded in 1976. More than 30 years later, we’re still committed to producing consistently exceptional books. With each of our titles, we’re working hard to set a new standard for the industry. From the paper we print on, to the authors we work with, our goal is to bring you the best books available.
I hope you see all that reflected in these pages. I’d be very interested to hear your comments and get your feedback on how we’re doing. Feel free to let me know what you think about this or any other Sybex book by sending me an email at nedde@wiley.com. If you think you’ve found a technical error in this book, please visit http://sybex.custhelp.com. Customer feedback is critical to our efforts at Sybex.
Read more
-
Clinical Hypertension
 This book represents the distillation of a tremendous volume of literature, filtered through the receptive and, I trust, discriminating awareness of a single author. When I wrote the first edition in 1973, the task was challenging, mainly because few had tried a synthesis of what was then known. But—as most who read this book are well aware—in the ensuing 30 years, the task has become much more difficult, mainly because the literature on hypertension has grown so that it is almost beyond the grasp of any one person. I continue to be a single author (with the important exception of the chapter on children) for these two reasons:
First, a single-authored text offers more cohesion and completeness, and, at the same time, brevity and lack of repetition, compared to most multiauthored but rarely edited megabooks. Second, I have the time, energy, and interest to keep up with the literature, and this book has become the major focus of my professional life. The success of the previous editions and the many compliments received from both clinicians in the field and investigators from the research bench have prompted me to do it again. Read more
This book represents the distillation of a tremendous volume of literature, filtered through the receptive and, I trust, discriminating awareness of a single author. When I wrote the first edition in 1973, the task was challenging, mainly because few had tried a synthesis of what was then known. But—as most who read this book are well aware—in the ensuing 30 years, the task has become much more difficult, mainly because the literature on hypertension has grown so that it is almost beyond the grasp of any one person. I continue to be a single author (with the important exception of the chapter on children) for these two reasons:
First, a single-authored text offers more cohesion and completeness, and, at the same time, brevity and lack of repetition, compared to most multiauthored but rarely edited megabooks. Second, I have the time, energy, and interest to keep up with the literature, and this book has become the major focus of my professional life. The success of the previous editions and the many compliments received from both clinicians in the field and investigators from the research bench have prompted me to do it again. Read more
-
Clinical Virology
 n this pocket-sized handbook we have attempted to meet the need for condensed and readily accessible information about viruses as agents of human disease. We hope that this book will provide useful information for all healthcare professionals, in particular practising physicians, medical and nursing students, interns and residents. We have included some new chapters on hepatitis and herpes viruses to this new edition, whereas the arboviruses chapter has been taken out. The cartoons will hopefully entertain as well as provide a helpful visual image of some salient points. The gestation period for this new edition was very long. Hopefully the offspring will please.
Read more
n this pocket-sized handbook we have attempted to meet the need for condensed and readily accessible information about viruses as agents of human disease. We hope that this book will provide useful information for all healthcare professionals, in particular practising physicians, medical and nursing students, interns and residents. We have included some new chapters on hepatitis and herpes viruses to this new edition, whereas the arboviruses chapter has been taken out. The cartoons will hopefully entertain as well as provide a helpful visual image of some salient points. The gestation period for this new edition was very long. Hopefully the offspring will please.
Read more
-
Forest Protection
 Forest protection is the preservation or improvement of a forest threatened or affected by natural or man made causes
This forest protection also has a legal status and rather than protection from only people damaging the forests is seen to be broader and include forest pathology too. Thus due to this the different emphases around the world paradoxically suggest different things for forest protection.
In German speaking countries forest protection would focus on the biotic and abiotic factors that are non-crime related. A protected forest is not the same as a protection forest. These terms can lead to some confusion in English, although they are clearer in other languages. As a result, reading English literature can be problematic for non-experts due to localization and conflation of meanings. Read more
Forest protection is the preservation or improvement of a forest threatened or affected by natural or man made causes
This forest protection also has a legal status and rather than protection from only people damaging the forests is seen to be broader and include forest pathology too. Thus due to this the different emphases around the world paradoxically suggest different things for forest protection.
In German speaking countries forest protection would focus on the biotic and abiotic factors that are non-crime related. A protected forest is not the same as a protection forest. These terms can lead to some confusion in English, although they are clearer in other languages. As a result, reading English literature can be problematic for non-experts due to localization and conflation of meanings. Read more
-
Geometry
 Geometry (from the Ancient Greek: ?????????; geo- "earth", -metron "measurement") is a branch of mathematics concerned with questions of shape, size, relative position of figures, and the properties of space. A mathematician who works in the field of geometry is called a geometer.
Geometry arose independently in a number of early cultures as a practical way for dealing with lengths, areas, and volumes. Geometry began to see elements of formal mathematical science emerging in the West as early as the 6th century BC.[1] By the 3rd century BC, geometry was put into an axiomatic form by Euclid, whose treatment, Euclid's Elements, set a standard for many centuries to follow.[2] Geometry arose independently in India, with texts providing rules for geometric constructions appearing as early as the 3rd century BC.[3] Islamic scientists preserved Greek ideas and expanded on them during the Middle Ages.[4] By the early 17th century, geometry had been put on a solid analytic footing by mathematicians such as René Descartes and Pierre de Fermat. Since then, and into modern times, geometry has expanded into non-Euclidean geometry and manifolds, describing spaces that lie beyond the normal range of human experience.[5] Read more
Geometry (from the Ancient Greek: ?????????; geo- "earth", -metron "measurement") is a branch of mathematics concerned with questions of shape, size, relative position of figures, and the properties of space. A mathematician who works in the field of geometry is called a geometer.
Geometry arose independently in a number of early cultures as a practical way for dealing with lengths, areas, and volumes. Geometry began to see elements of formal mathematical science emerging in the West as early as the 6th century BC.[1] By the 3rd century BC, geometry was put into an axiomatic form by Euclid, whose treatment, Euclid's Elements, set a standard for many centuries to follow.[2] Geometry arose independently in India, with texts providing rules for geometric constructions appearing as early as the 3rd century BC.[3] Islamic scientists preserved Greek ideas and expanded on them during the Middle Ages.[4] By the early 17th century, geometry had been put on a solid analytic footing by mathematicians such as René Descartes and Pierre de Fermat. Since then, and into modern times, geometry has expanded into non-Euclidean geometry and manifolds, describing spaces that lie beyond the normal range of human experience.[5] Read more
-
HTML with CSS & XHTML
 This book has humor, and charm, but most importantly, it has heart. I know that sounds ridiculous to say about a technical book, but I really sense that at its core, this book (or at least its authors) really care that the reader learn the material. This comes across in the style, the language, and the techniques. Learning – real understanding and comprehension – on the part of the reader is clearly top most in the minds of the Freemans. And thank you, thank you, thank you, for the book’s strong, and sensible advocacy of standards compliance. It’s great to see an entry level book, that I think will be widely read and studied, campaign so eloquently and persuasively on behalf of the value of standards compliance in web page code. I even found in here a few great arguments I had not thought of – ones I can remember and use when I am asked – as I still am – ‘what’s the deal with compliance and why should we care?’ I’ll have more ammo now! I also liked that the book sprinkles in some basics about the mechanics of actually getting a web page live - FTP, web server basics, file structures, etc.”
Read more
This book has humor, and charm, but most importantly, it has heart. I know that sounds ridiculous to say about a technical book, but I really sense that at its core, this book (or at least its authors) really care that the reader learn the material. This comes across in the style, the language, and the techniques. Learning – real understanding and comprehension – on the part of the reader is clearly top most in the minds of the Freemans. And thank you, thank you, thank you, for the book’s strong, and sensible advocacy of standards compliance. It’s great to see an entry level book, that I think will be widely read and studied, campaign so eloquently and persuasively on behalf of the value of standards compliance in web page code. I even found in here a few great arguments I had not thought of – ones I can remember and use when I am asked – as I still am – ‘what’s the deal with compliance and why should we care?’ I’ll have more ammo now! I also liked that the book sprinkles in some basics about the mechanics of actually getting a web page live - FTP, web server basics, file structures, etc.”
Read more
-
Intensive Care Medicine
 Intensive Care Medicine. The first four editions have established this text as a leading source of information in the rapidly changing and complex field of critical care. The editorial challenge for the fifth edition was to ensure that the textbook continued to evolve, improve, and change to meet the rigorous demands placed on it by clinicians in all specialties practicing in the adult intensive care environment without losing the fundamental strengths that have made it so useful and popular. A particular challenge was to update the text and incorporate new material while judiciously discarding older information. We hope and believe that the fifth edition of Irwin and Rippe's Intensive Care Medicine has risen to the multiple challenges that we as editors have faced. Read more
Intensive Care Medicine. The first four editions have established this text as a leading source of information in the rapidly changing and complex field of critical care. The editorial challenge for the fifth edition was to ensure that the textbook continued to evolve, improve, and change to meet the rigorous demands placed on it by clinicians in all specialties practicing in the adult intensive care environment without losing the fundamental strengths that have made it so useful and popular. A particular challenge was to update the text and incorporate new material while judiciously discarding older information. We hope and believe that the fifth edition of Irwin and Rippe's Intensive Care Medicine has risen to the multiple challenges that we as editors have faced. Read more
-
J2EE Deployment and Administration
 Like most web application servers, Oracle 10g AS is available in a number of different editions, ranging from a small development-only J2EE server, to the full-fledged Enterprise installation. All of these include the basic J2EE containers (called Oracle 10g AS Containers for J2EE or OC4J), which provide support for Servlets, JavaServer Pages (JSPs), Enterprise JavaBeans (EJBs) and other standard J2EE technologies. Other, larger and more expensive versions include additional non-J2EE features such as Oracle's modified Apache web server, longtime Oracle products such as Portal, Forms, Reports, and Discoverer, Oracle's Identity Management products such as Oracle Internet Directory and SSO, and advanced features for high-performance and highavailability sites such as Web Cache and Clustering. There's no one size fits all so it's important to tailor the edition to the needs of your application.
Read more
Like most web application servers, Oracle 10g AS is available in a number of different editions, ranging from a small development-only J2EE server, to the full-fledged Enterprise installation. All of these include the basic J2EE containers (called Oracle 10g AS Containers for J2EE or OC4J), which provide support for Servlets, JavaServer Pages (JSPs), Enterprise JavaBeans (EJBs) and other standard J2EE technologies. Other, larger and more expensive versions include additional non-J2EE features such as Oracle's modified Apache web server, longtime Oracle products such as Portal, Forms, Reports, and Discoverer, Oracle's Identity Management products such as Oracle Internet Directory and SSO, and advanced features for high-performance and highavailability sites such as Web Cache and Clustering. There's no one size fits all so it's important to tailor the edition to the needs of your application.
Read more
-
Java Development with the Spring Framework
 The Spring Framework is a major open source application development framework that makes Java/J2EE development easier and more productive. This book shows you not only what spring can do but why, explaining its functionality and motivation to help you use all parts of the framework to develop successful applications.
You will be guided through all the Spring features and see how they form a coherent whole. In turn, this will help you understand the rationale for Spring’s approach, when to use Spring, and how to follow best practices. All this is illustrated with a complete sample application. When you finish the book, you will be well equipped to use Spring effectively in everything from simple Web applications to complex enterprise applications.
What you will learn from this book
The core Inversion of Control container and the concept of Dependency Injection
Spring’s Aspect Oriented Programming (AOP) framework and why AOP is important in J2EE development Read more
The Spring Framework is a major open source application development framework that makes Java/J2EE development easier and more productive. This book shows you not only what spring can do but why, explaining its functionality and motivation to help you use all parts of the framework to develop successful applications.
You will be guided through all the Spring features and see how they form a coherent whole. In turn, this will help you understand the rationale for Spring’s approach, when to use Spring, and how to follow best practices. All this is illustrated with a complete sample application. When you finish the book, you will be well equipped to use Spring effectively in everything from simple Web applications to complex enterprise applications.
What you will learn from this book
The core Inversion of Control container and the concept of Dependency Injection
Spring’s Aspect Oriented Programming (AOP) framework and why AOP is important in J2EE development Read more
-
Theory of Machines
 A machine is a tool containing one or more parts that transforms energy. Machines are usually powered by chemical, thermal, or electrical means, and are often motorized. Historically, a power tool also required moving parts to classify as a machine. However, the advent of electronics has led to the development of power tools without moving parts that are considered machines.[1]
A simple machine is a device that simply transforms the direction or magnitude of a force, but a large number of more complex machines exist. Examples include vehicles, electronic systems, molecular machines, computers, television, and radio Read more
A machine is a tool containing one or more parts that transforms energy. Machines are usually powered by chemical, thermal, or electrical means, and are often motorized. Historically, a power tool also required moving parts to classify as a machine. However, the advent of electronics has led to the development of power tools without moving parts that are considered machines.[1]
A simple machine is a device that simply transforms the direction or magnitude of a force, but a large number of more complex machines exist. Examples include vehicles, electronic systems, molecular machines, computers, television, and radio Read more
-
Urologic Surgery
 Urologists are—first and foremost—surgeons.” The second edition expressed the hope that the volume “constitute the basis for further advances and that it be rendered obsolete by progress in urology.” In the third edition, it was acknowledged that progress in urology was paralleled by “advances in anesthesia, antibiosis, medical techniques, and diagnostic capability.” The fourth edition reaffirmed that “although many textbooks of urology and a number of excellent atlases dealt with surgical procedures, no single volume combined the virtues of text and illustrations that amplify the fundamental considerations and technical aspects” of urologic surgery. Read more
Urologists are—first and foremost—surgeons.” The second edition expressed the hope that the volume “constitute the basis for further advances and that it be rendered obsolete by progress in urology.” In the third edition, it was acknowledged that progress in urology was paralleled by “advances in anesthesia, antibiosis, medical techniques, and diagnostic capability.” The fourth edition reaffirmed that “although many textbooks of urology and a number of excellent atlases dealt with surgical procedures, no single volume combined the virtues of text and illustrations that amplify the fundamental considerations and technical aspects” of urologic surgery. Read more
-
Accountancy and Auditing
 An account (in book-keeping) refers to assets, liabilities, income, expenses, and equity, as represented by individual ledger pages, to which changes in value are chronologically recorded with debit and credit entries. These entries, referred to as postings, become part of a book of final entry or ledger. Examples of common financial accounts are sales, accounts receivable, mortgages, loans, PP&E, common stock, sales, services, wages and payroll.
A chart of accounts provides a listing of all financial accounts used by particular business, organization, or government agency. Read more
An account (in book-keeping) refers to assets, liabilities, income, expenses, and equity, as represented by individual ledger pages, to which changes in value are chronologically recorded with debit and credit entries. These entries, referred to as postings, become part of a book of final entry or ledger. Examples of common financial accounts are sales, accounts receivable, mortgages, loans, PP&E, common stock, sales, services, wages and payroll.
A chart of accounts provides a listing of all financial accounts used by particular business, organization, or government agency. Read more
-
AJCC Cancer Staging Handbook
 The AJCC Cancer Staging Handbook is an excerpt from the AJCC Cancer Staging Manual, Sixth Edition, published by Springer-Verlag New York, Inc. It includes the text from that manual only and not the staging forms. Because the text was taken verbatim from the manual, some references to the forms still remain. The forms are available in the manual and from a CD-ROM packaged with each manual. It is hoped that providing the text of the manual in a practical format will facilitate its use and serve to further the uniform description of the neoplastic diseases in different parts, systems or organs.
The handbook brings together all currently available information on staging of cancer at various anatomic sites as developed by the American Joint Committee on Cancer (AJCC) with support from the American Cancer Society, American College of Surgeons, the American Society of Clinical Oncology, and the International Union Against Cancer. All of the schemes included here are uniform between the AJCC and the International Union Against Cancer. Read more
The AJCC Cancer Staging Handbook is an excerpt from the AJCC Cancer Staging Manual, Sixth Edition, published by Springer-Verlag New York, Inc. It includes the text from that manual only and not the staging forms. Because the text was taken verbatim from the manual, some references to the forms still remain. The forms are available in the manual and from a CD-ROM packaged with each manual. It is hoped that providing the text of the manual in a practical format will facilitate its use and serve to further the uniform description of the neoplastic diseases in different parts, systems or organs.
The handbook brings together all currently available information on staging of cancer at various anatomic sites as developed by the American Joint Committee on Cancer (AJCC) with support from the American Cancer Society, American College of Surgeons, the American Society of Clinical Oncology, and the International Union Against Cancer. All of the schemes included here are uniform between the AJCC and the International Union Against Cancer. Read more
-
Algebra
 Algebra (from Arabic "al-jabr" meaning "reunion of broken parts"[1]) is one of the broad parts of mathematics, together with number theory, geometry and analysis. In its most general form, algebra is the study of mathematical symbols and the rules for manipulating these symbols;[2] it is a unifying thread of almost all of mathematics.[3] As such, it includes everything from elementary equation solving to the study of abstractions such as groups, rings, and fields. The more basic parts of algebra are called elementary algebra; the more abstract parts are called abstract algebra or modern algebra. Elementary algebra is generally considered to be essential for any study of mathematics, science, or engineering, as well as such applications as medicine and economics. Abstract algebra is a major area in advanced mathematics, studied primarily by professional mathematicians Read more
Algebra (from Arabic "al-jabr" meaning "reunion of broken parts"[1]) is one of the broad parts of mathematics, together with number theory, geometry and analysis. In its most general form, algebra is the study of mathematical symbols and the rules for manipulating these symbols;[2] it is a unifying thread of almost all of mathematics.[3] As such, it includes everything from elementary equation solving to the study of abstractions such as groups, rings, and fields. The more basic parts of algebra are called elementary algebra; the more abstract parts are called abstract algebra or modern algebra. Elementary algebra is generally considered to be essential for any study of mathematics, science, or engineering, as well as such applications as medicine and economics. Abstract algebra is a major area in advanced mathematics, studied primarily by professional mathematicians Read more
-
Ant: The Definitive Guide
 Ant is the premier build-management tool for Java environments. Ant is part of Jakarta, the Apache Software Foundation's open source Java project repository. Ant is written entirely in Java, and is platform independent. Using XML, a Java developer describes the modules involved in a build, and the dependencies between those modules. Ant then does the rest, compiling components as necessary in order to build the application.
Read more
Ant is the premier build-management tool for Java environments. Ant is part of Jakarta, the Apache Software Foundation's open source Java project repository. Ant is written entirely in Java, and is platform independent. Using XML, a Java developer describes the modules involved in a build, and the dependencies between those modules. Ant then does the rest, compiling components as necessary in order to build the application.
Read more
-
ANTHROPOLOGY003.p
 he object of study for cyborg anthropology is the cyborg. Originally coined in a 1960 paper about space exploration, the term is short for cybernetic organism.[7] A cyborg is traditionally defined as a system with both organic and inorganic parts. In the narrowest sense of the word, cyborgs are people with machinated body parts. These cyborg parts may be restorative technologies that help a body function where the organic system has failed, like pacemakers, insulin pumps, and bionic limbs, or enhanced technologies that improve the human body beyond its natural state.[8] In the broadest sense, all human interactions with technology could qualify as a cyborg. Most cyborg anthropologists lean towards the latter view of the cyborg; some, like Amber Case, even claim that humans are already cyborgs because people's daily life and sense of self is so intertwined with technology.[5] Haraway's "Cyborg Manifesto" suggests that technology like virtual avatars, artificial insemination, sexual reassignment surgery, and artificial intelligence might make dichotomies of sex and gender irrelevant, even nonexistent. She goes on to say that other human distinctions (like life and death, human and machine, virtual and real) may similarly disappear in the wake of the cyborg Read more
he object of study for cyborg anthropology is the cyborg. Originally coined in a 1960 paper about space exploration, the term is short for cybernetic organism.[7] A cyborg is traditionally defined as a system with both organic and inorganic parts. In the narrowest sense of the word, cyborgs are people with machinated body parts. These cyborg parts may be restorative technologies that help a body function where the organic system has failed, like pacemakers, insulin pumps, and bionic limbs, or enhanced technologies that improve the human body beyond its natural state.[8] In the broadest sense, all human interactions with technology could qualify as a cyborg. Most cyborg anthropologists lean towards the latter view of the cyborg; some, like Amber Case, even claim that humans are already cyborgs because people's daily life and sense of self is so intertwined with technology.[5] Haraway's "Cyborg Manifesto" suggests that technology like virtual avatars, artificial insemination, sexual reassignment surgery, and artificial intelligence might make dichotomies of sex and gender irrelevant, even nonexistent. She goes on to say that other human distinctions (like life and death, human and machine, virtual and real) may similarly disappear in the wake of the cyborg Read more
-
Apoptosis in Neurobiology: Concepts and Methods
 This book contains information obtained from authentic and highly regarded sources. Reprinted material is quoted with permission, and sources are indicated. A wide variety of references are listed. Reasonable efforts have been made to publish reliable data and information, but the author and the publisher cannot assume responsibility for the validity of all materials or for the consequences of their use. Neither this book nor any part may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, micro?lming, and recording, or by any information storage or retrieval system, without prior permission in writing from the publisher. All rights reserved. Authorization to photocopy items for internal or personal use, or the personal or internal use of speci?c clients, may be granted by CRC Press LLC, provided that $.50 per page photocopied is paid directly to Copyright Clearance Center, 27 Congress Street, Salem, MA 01970 USA. The fee code for users of the Transactional Reporting Service is ISBN 0-8493-3352-0/99/$0.00+$.50. The fee is subject to change without notice. For organizations that have been granted a photocopy license by the CCC, a separate system of payment has been arranged
Read more
This book contains information obtained from authentic and highly regarded sources. Reprinted material is quoted with permission, and sources are indicated. A wide variety of references are listed. Reasonable efforts have been made to publish reliable data and information, but the author and the publisher cannot assume responsibility for the validity of all materials or for the consequences of their use. Neither this book nor any part may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, micro?lming, and recording, or by any information storage or retrieval system, without prior permission in writing from the publisher. All rights reserved. Authorization to photocopy items for internal or personal use, or the personal or internal use of speci?c clients, may be granted by CRC Press LLC, provided that $.50 per page photocopied is paid directly to Copyright Clearance Center, 27 Congress Street, Salem, MA 01970 USA. The fee code for users of the Transactional Reporting Service is ISBN 0-8493-3352-0/99/$0.00+$.50. The fee is subject to change without notice. For organizations that have been granted a photocopy license by the CCC, a separate system of payment has been arranged
Read more
-
Applied Mathamatics
 Applied mathematics is a branch of mathematics that deals with mathematical methods that find use in science, engineering, business, computer science, and industry. Thus, applied mathematics is a combination of mathematical science and specialized knowledge. The term "applied mathematics" also describes the professional specialty in which mathematicians work on practical problems by formulating and studying mathematical models. In the past, practical applications have motivated the development of mathematical theories, which then became the subject of study in pure mathematics where abstract concepts are studied for their own sake. The activity of applied mathematics is thus intimately connected with research in pure mathematics Read more
Applied mathematics is a branch of mathematics that deals with mathematical methods that find use in science, engineering, business, computer science, and industry. Thus, applied mathematics is a combination of mathematical science and specialized knowledge. The term "applied mathematics" also describes the professional specialty in which mathematicians work on practical problems by formulating and studying mathematical models. In the past, practical applications have motivated the development of mathematical theories, which then became the subject of study in pure mathematics where abstract concepts are studied for their own sake. The activity of applied mathematics is thus intimately connected with research in pure mathematics Read more
-
Architecting RouteOne CAS Using Java
 JavaOne is an annual conference organized by Oracle Corporation to discuss Java technologies, primarily among Java developers. JavaOne is held in San Francisco, Californiatypically running from a Monday to Thursday in September or October. Technical sessions on a variety of topics are held during the day. In the evening, Birds of a Feather (BOF) sessions are held, which allow people to focus on a particular aspect of Java technology.
Access to the technical sessions, keynote presentations, exhibits and BOF sessions requires a conference pass, which costs US$2,050.[1]
The conference was first organized in 1996 by Sun Microsystems, which was purchased in 2010 by Oracle Corporation. After the acquisition, the conference has been held concurrently with Oracle OpenWorld. The conference was moved from Moscone Center to hotels on nearby Mason Street. In some years, one block of Mason was closed and covered with a tent, which formed part of the conference venue. Read more
JavaOne is an annual conference organized by Oracle Corporation to discuss Java technologies, primarily among Java developers. JavaOne is held in San Francisco, Californiatypically running from a Monday to Thursday in September or October. Technical sessions on a variety of topics are held during the day. In the evening, Birds of a Feather (BOF) sessions are held, which allow people to focus on a particular aspect of Java technology.
Access to the technical sessions, keynote presentations, exhibits and BOF sessions requires a conference pass, which costs US$2,050.[1]
The conference was first organized in 1996 by Sun Microsystems, which was purchased in 2010 by Oracle Corporation. After the acquisition, the conference has been held concurrently with Oracle OpenWorld. The conference was moved from Moscone Center to hotels on nearby Mason Street. In some years, one block of Mason was closed and covered with a tent, which formed part of the conference venue. Read more
-
Assuring Security by Penetration Testing
 BackTrack is a penetration testing and security auditing platform with advanced tools to identify, detect, and exploit any vulnerabilities uncovered in the target network environment. Applying appropriate testing methodology with defined business objectives and a scheduled test plan will result in robust penetration testing of your network. BackTrack 4: Assuring Security by Penetration Testing is a fully focused, structured book providing guidance on developing practical penetration testing skills by demonstrating the cutting-edge hacker tools and techniques in a coherent step-by-step strategy. It offers all the essential lab preparation and testing procedures to reflect real-world attack scenarios from your business perspective in today's digital age. The authors' experience and expertise enables them to reveal the industry's best approach for logical and systematic penetration testing. The first and so far only book on BackTrack OS starts with lab preparation and testing procedures, explaining the basic installation and configuration set up, discussing types of penetration testing (black box and white box), uncovering open security testing methodologies, and proposing the BackTrack specific testing process. The authors discuss a number of security assessment tools necessary to conduct penetration testing in their respective categories (target scoping, information gathering, discovery, enumeration, vulnerability mapping, social engineering, exploitation, privilege escalation, maintaining access, and reporting), following the formal testing methodology. Each of these tools is illustrated with real-world examples to highlight their practical usage and proven configuration techniques. The authors also provide extra weaponry treasures and cite key resources that may be crucial to any professional penetration tester.
Read more
BackTrack is a penetration testing and security auditing platform with advanced tools to identify, detect, and exploit any vulnerabilities uncovered in the target network environment. Applying appropriate testing methodology with defined business objectives and a scheduled test plan will result in robust penetration testing of your network. BackTrack 4: Assuring Security by Penetration Testing is a fully focused, structured book providing guidance on developing practical penetration testing skills by demonstrating the cutting-edge hacker tools and techniques in a coherent step-by-step strategy. It offers all the essential lab preparation and testing procedures to reflect real-world attack scenarios from your business perspective in today's digital age. The authors' experience and expertise enables them to reveal the industry's best approach for logical and systematic penetration testing. The first and so far only book on BackTrack OS starts with lab preparation and testing procedures, explaining the basic installation and configuration set up, discussing types of penetration testing (black box and white box), uncovering open security testing methodologies, and proposing the BackTrack specific testing process. The authors discuss a number of security assessment tools necessary to conduct penetration testing in their respective categories (target scoping, information gathering, discovery, enumeration, vulnerability mapping, social engineering, exploitation, privilege escalation, maintaining access, and reporting), following the formal testing methodology. Each of these tools is illustrated with real-world examples to highlight their practical usage and proven configuration techniques. The authors also provide extra weaponry treasures and cite key resources that may be crucial to any professional penetration tester.
Read more
-
Banking Awareness Lecture
 A bank is an institution where customers can save or borrow money. Banks also invest money to build up their reserve of money. What they do is regulated by laws. Those laws differ in different countries. The people who run a bank are called bankers. Certain banks deal directly with the public and they are the only ones which an ordinary person will deal with. Other banks deal with investments and international currency trading.
Customers' money may be placed in the bank for safe keeping. Banks may give loans to customers under an agreement to pay the bank back at a later time, with interest. An example is getting a mortgage to buy a house or apartment. Banks also can use the money they have from deposit accounts to invest in businesses in order to make more money. Read more
A bank is an institution where customers can save or borrow money. Banks also invest money to build up their reserve of money. What they do is regulated by laws. Those laws differ in different countries. The people who run a bank are called bankers. Certain banks deal directly with the public and they are the only ones which an ordinary person will deal with. Other banks deal with investments and international currency trading.
Customers' money may be placed in the bank for safe keeping. Banks may give loans to customers under an agreement to pay the bank back at a later time, with interest. An example is getting a mortgage to buy a house or apartment. Banks also can use the money they have from deposit accounts to invest in businesses in order to make more money. Read more
-
Beginning Hibernate
 This book assumes a good understanding of Java fundamentals and some familiarity with database programming using the Java Database Connectivity (JDBC) API. We don’t expect you to knowanything about Hibernate—but if you buy this book, it will probably be because you have some exposure to the painful process of building a large database-based system. All of our examples use open source software—primarily the Hibernate API itself—so you will not need to purchase any software to get started with Hibernate development. This book is not an academic text. Our focus is instead on providing extensive examples and taking a pragmatic approach to the technology that it covers. Totrue newcomers to the Hibernate API, we recommend that you read at least the first three chapters in order beforediving into the juicy subjects of later chapters.Very experienced developers or those with experience with tools similar to Hibernate will want to skim through the latter half of the book for interesting chapters.Readers familiar with Hibernate will want to turnto the appendixes for discussion of morearcane topics. Read more
This book assumes a good understanding of Java fundamentals and some familiarity with database programming using the Java Database Connectivity (JDBC) API. We don’t expect you to knowanything about Hibernate—but if you buy this book, it will probably be because you have some exposure to the painful process of building a large database-based system. All of our examples use open source software—primarily the Hibernate API itself—so you will not need to purchase any software to get started with Hibernate development. This book is not an academic text. Our focus is instead on providing extensive examples and taking a pragmatic approach to the technology that it covers. Totrue newcomers to the Hibernate API, we recommend that you read at least the first three chapters in order beforediving into the juicy subjects of later chapters.Very experienced developers or those with experience with tools similar to Hibernate will want to skim through the latter half of the book for interesting chapters.Readers familiar with Hibernate will want to turnto the appendixes for discussion of morearcane topics. Read more
-
Beginning J2ME
 This book describes how to program mobile telephones, pagers, PDAs, and other small devices using Java technology. It is about the Mobile Information Device Profile (MIDP), which is part of the Java 2 Platform, Micro Edition (J2ME). It is concise and complete, describing all of MIDP as well as moving into several exciting advanced concepts such as 3D graphics and cryptography. This third edition covers MIDP 2.0, and has been updated to track the Java Technology for the Wireless Industry (JTWI 1.0) de facto standard. Every chapter has been revised and meticulously updated, and four completely new chapters have been added. Read more
This book describes how to program mobile telephones, pagers, PDAs, and other small devices using Java technology. It is about the Mobile Information Device Profile (MIDP), which is part of the Java 2 Platform, Micro Edition (J2ME). It is concise and complete, describing all of MIDP as well as moving into several exciting advanced concepts such as 3D graphics and cryptography. This third edition covers MIDP 2.0, and has been updated to track the Java Technology for the Wireless Industry (JTWI 1.0) de facto standard. Every chapter has been revised and meticulously updated, and four completely new chapters have been added. Read more
-
Beginning JSF
 JavaServer Faces (JSF) is a Java specification for building component-based user interfaces for web applications[1] and was formalized as a standard through the Java Community Process being part of the Java Platform, Enterprise Edition. It is also a MVC web framework that simplifies to construct user interfaces (UI) for server-based applications by using reusable UI components in a page.[2]
JSF 2 uses Facelets as its default templating system. Other view technologies such as XUL or plain Java[3] can also be employed. In contrast, JSF 1.x uses JavaServer Pages (JSP) as its default templating system. Read more
JavaServer Faces (JSF) is a Java specification for building component-based user interfaces for web applications[1] and was formalized as a standard through the Java Community Process being part of the Java Platform, Enterprise Edition. It is also a MVC web framework that simplifies to construct user interfaces (UI) for server-based applications by using reusable UI components in a page.[2]
JSF 2 uses Facelets as its default templating system. Other view technologies such as XUL or plain Java[3] can also be employed. In contrast, JSF 1.x uses JavaServer Pages (JSP) as its default templating system. Read more
-
Beginning JSP
 Let Beginning JSP 2 be your guide as you begin using JSP. This comprehensive guide starts by steering you through your first JSP application. It reviews HTML, and provides you with a useful overview of JSP. You’ll then be ready to start learning one of the core techniques in JSP: pulling data from a database and working with that data.
When you’ve mastered this technique, you’ll be ready to branch out powerfully into other JSP topics: variables, scope, flow control, and code reuse for productive time management. Finally, the book shows you how you can use JSP with XML and gives you a taste of some advanced topics, including using Struts and the Model View Controller. Read more
Let Beginning JSP 2 be your guide as you begin using JSP. This comprehensive guide starts by steering you through your first JSP application. It reviews HTML, and provides you with a useful overview of JSP. You’ll then be ready to start learning one of the core techniques in JSP: pulling data from a database and working with that data.
When you’ve mastered this technique, you’ll be ready to branch out powerfully into other JSP topics: variables, scope, flow control, and code reuse for productive time management. Finally, the book shows you how you can use JSP with XML and gives you a taste of some advanced topics, including using Struts and the Model View Controller. Read more
-
Beginning Linux Programming Third Edition
 In this book we aim to give you an introduction to a wide variety of topics important to you as a developer using Linux. The word beginning in the title refers more to the content than to your skill level. We’ve structured the book to help you learn more about what Linux has to offer, however much experience you have already. Linux programming is a large field and we aim to cover enough about a wide range of topics to give you a good “beginning” in each subject
Read more
In this book we aim to give you an introduction to a wide variety of topics important to you as a developer using Linux. The word beginning in the title refers more to the content than to your skill level. We’ve structured the book to help you learn more about what Linux has to offer, however much experience you have already. Linux programming is a large field and we aim to cover enough about a wide range of topics to give you a good “beginning” in each subject
Read more
-
Beginning Ubuntu LTS Server Administration
 Beginning Ubuntu LTS Server Administration, Second Edition is the touchstone companion book for anyone implementing Ubuntu LTS Server. Author Sander van Vugt introduces the most recent server edition of Ubuntu Linux, the most popular Linux distribution, to power users, system administrators, and programmers and demonstrates the power and flexibility that the Hardy–Heron Ubuntu Server Long Term Support Edition offers for small networks and corporate systems alike.
This book covers:
Installing and configuring Ubuntu to ensure secure installations
Virtual Ubuntu
Full network and web services management
Read more
Beginning Ubuntu LTS Server Administration, Second Edition is the touchstone companion book for anyone implementing Ubuntu LTS Server. Author Sander van Vugt introduces the most recent server edition of Ubuntu Linux, the most popular Linux distribution, to power users, system administrators, and programmers and demonstrates the power and flexibility that the Hardy–Heron Ubuntu Server Long Term Support Edition offers for small networks and corporate systems alike.
This book covers:
Installing and configuring Ubuntu to ensure secure installations
Virtual Ubuntu
Full network and web services management
Read more
-
Botony
 Botany, also called plant science(s), plant biology or phytology, is the science of plant life and a branch of biology. A botanist or plant scientist is a scientist who specialises in this field. The term "botany" comes from the Ancient Greek word ?????? (botan?) meaning "pasture", "grass", or "fodder"; ?????? is in turn derived from ??????? (boskein), "to feed" or "to graze".[1][2][3] Traditionally, botany has also included the study of fungi and algae by mycologists and phycologists respectively, with the study of these three groups of organisms remaining within the sphere of interest of the International Botanical Congress. Nowadays, botanists (in the strict sense) study approximately 410,000 species of land plants of which some 391,000 species are vascular plants (including ca 369,000 species of flowering plants),[4] and ca 20,000 are bryophytes.[5] Read more
Botany, also called plant science(s), plant biology or phytology, is the science of plant life and a branch of biology. A botanist or plant scientist is a scientist who specialises in this field. The term "botany" comes from the Ancient Greek word ?????? (botan?) meaning "pasture", "grass", or "fodder"; ?????? is in turn derived from ??????? (boskein), "to feed" or "to graze".[1][2][3] Traditionally, botany has also included the study of fungi and algae by mycologists and phycologists respectively, with the study of these three groups of organisms remaining within the sphere of interest of the International Botanical Congress. Nowadays, botanists (in the strict sense) study approximately 410,000 species of land plants of which some 391,000 species are vascular plants (including ca 369,000 species of flowering plants),[4] and ca 20,000 are bryophytes.[5] Read more
-
Bulletproof Web Design
 No matter how visually appealing or packed with content your Web site is, it isn't succeeding if it's not reaching the widest possible audience. If you get this guide, you can be assured it will! By deconstructing a series of real-world Web sites, author and Web designer extraordinaire Dan Cederholm outlines 10 strategies for creating standardsbased designs that provide flexibility, readability, and user controlkey components of every successful Web site. Each chapter starts out with an example of what Dan refers to as an "unbulletproof" conceptan existing site that employs a traditional approach and its associated pitfalls. Dan then deconstructs that approach, noting its downsides and then making the site over using Cascading Style Sheets (CSS). By the end of each chapter, you'll have replaced traditional, bloated, inaccessible page components with lean markup and CSS. The guide culminates with a chapter that pieces together all of the page components discussed in prior chapters into a single page template Read more
No matter how visually appealing or packed with content your Web site is, it isn't succeeding if it's not reaching the widest possible audience. If you get this guide, you can be assured it will! By deconstructing a series of real-world Web sites, author and Web designer extraordinaire Dan Cederholm outlines 10 strategies for creating standardsbased designs that provide flexibility, readability, and user controlkey components of every successful Web site. Each chapter starts out with an example of what Dan refers to as an "unbulletproof" conceptan existing site that employs a traditional approach and its associated pitfalls. Dan then deconstructs that approach, noting its downsides and then making the site over using Cascading Style Sheets (CSS). By the end of each chapter, you'll have replaced traditional, bloated, inaccessible page components with lean markup and CSS. The guide culminates with a chapter that pieces together all of the page components discussed in prior chapters into a single page template Read more
-
C# APPLICATIONS
 C#'s principal designer and lead architect at Microsoft is Anders Hejlsberg, who was previously involved with the design of Turbo Pascal, Embarcadero Delphi (formerly CodeGear Delphi, Inprise Delphi and Borland Delphi), and Visual J++. In interviews and technical papers he has stated that flaws[citation needed] in most major programming languages (e.g. C++, Java, Delphi, and Smalltalk) drove the fundamentals of the Common Language Runtime (CLR), which, in turn, drove the design of the C# language itself.
James Gosling, who created the Java programming language in 1994, and Bill Joy, a co-founder of Sun Microsystems, the originator of Java, called C# an "imitation" of Java; Gosling further said that "[C# is] sort of Java with reliability, productivity and security deleted."[17][18] Klaus Kreft and Angelika Langer (authors of a C++ streams book) stated in a blog post that "Java and C# are almost identical programming languages. Boring repetition that lacks innovation,"[19] "Hardly anybody will claim that Java or C# are revolutionary programming languages that changed the way we write programs," and "C# borrowed a lot from Java - and vice versa. Now that C# supports boxing and unboxing, we'll have a very similar feature in Java."[20] In July 2000, Anders Hejlsberg said that C# is "not a Java clone" and is "much closer to C++" in its design.[21] Read more
C#'s principal designer and lead architect at Microsoft is Anders Hejlsberg, who was previously involved with the design of Turbo Pascal, Embarcadero Delphi (formerly CodeGear Delphi, Inprise Delphi and Borland Delphi), and Visual J++. In interviews and technical papers he has stated that flaws[citation needed] in most major programming languages (e.g. C++, Java, Delphi, and Smalltalk) drove the fundamentals of the Common Language Runtime (CLR), which, in turn, drove the design of the C# language itself.
James Gosling, who created the Java programming language in 1994, and Bill Joy, a co-founder of Sun Microsystems, the originator of Java, called C# an "imitation" of Java; Gosling further said that "[C# is] sort of Java with reliability, productivity and security deleted."[17][18] Klaus Kreft and Angelika Langer (authors of a C++ streams book) stated in a blog post that "Java and C# are almost identical programming languages. Boring repetition that lacks innovation,"[19] "Hardly anybody will claim that Java or C# are revolutionary programming languages that changed the way we write programs," and "C# borrowed a lot from Java - and vice versa. Now that C# supports boxing and unboxing, we'll have a very similar feature in Java."[20] In July 2000, Anders Hejlsberg said that C# is "not a Java clone" and is "much closer to C++" in its design.[21] Read more
-
C# Applications (Edition 3)
 C# supports strongly typed implicit variable declarations with the keyword var, and implicitly typed arrays with the keyword new[] followed by a collection initializer.
C# supports a strict Boolean data type, bool. Statements that take conditions, such as while and if, require an expression of a type that implements the true operator, such as the Boolean type. While C++ also has a Boolean type, it can be freely converted to and from integers, and expressions such as if(a) require only that a is convertible to bool, allowing a to be an int, or a pointer. C# disallows this "integer meaning true or false" approach, on the grounds that forcing programmers to use expressions that return exactly bool can prevent certain types of programming mistakes such as if (a = b) (use of assignment = instead of equality ==, which while not an error in C or C++, will be caught by the compiler anyway). Read more
C# supports strongly typed implicit variable declarations with the keyword var, and implicitly typed arrays with the keyword new[] followed by a collection initializer.
C# supports a strict Boolean data type, bool. Statements that take conditions, such as while and if, require an expression of a type that implements the true operator, such as the Boolean type. While C++ also has a Boolean type, it can be freely converted to and from integers, and expressions such as if(a) require only that a is convertible to bool, allowing a to be an int, or a pointer. C# disallows this "integer meaning true or false" approach, on the grounds that forcing programmers to use expressions that return exactly bool can prevent certain types of programming mistakes such as if (a = b) (use of assignment = instead of equality ==, which while not an error in C or C++, will be caught by the compiler anyway). Read more
-
C# Java Programmers
 Welcome to C# for Java Programmers.I think you’ll ?nd that this book will be both enjoyable and challenging at the same time.It will cover Microsoft’s new platform called .NET and the exciting new language for the platform called C#. According to Microsoft,the C# language is a simple,modern,object-oriented,and type-safe programming language derived from C and C++.But looking closely,you can see that C# also has a lot of similarities with Java.Our main goal here is to teach you the C# language by leveraging your existing Java skills. I know,I know,you’re probably wondering why you should learn another language when you already know Java and are reasonably comfortable with it.Well,here are several reasons: ? First,it’s from Microsoft.When a big company like Microsoft puts most of their resources into a new technology it’s hard for developers not to take notice.This new technology will certainly make an impact in the industry. ? As a programmer,C# is a language that will bene?t you if it’s add to your repertoire.With your Java skills,it’ll be a relatively small leap to learn this new language.Therefore,learning C# will increase your marketability in the workplace relatively painlessly. ? By learning C# and .NET,you’ll have several choices when implementing a solution for a speci?c project.For example,you can choose between .NET and J2EE when it comes to developing XML-based Web services. ? It’s arguable that Java lacks the performance needed when it comes to Windows applications development.C# enables you to develop fast Read more
Welcome to C# for Java Programmers.I think you’ll ?nd that this book will be both enjoyable and challenging at the same time.It will cover Microsoft’s new platform called .NET and the exciting new language for the platform called C#. According to Microsoft,the C# language is a simple,modern,object-oriented,and type-safe programming language derived from C and C++.But looking closely,you can see that C# also has a lot of similarities with Java.Our main goal here is to teach you the C# language by leveraging your existing Java skills. I know,I know,you’re probably wondering why you should learn another language when you already know Java and are reasonably comfortable with it.Well,here are several reasons: ? First,it’s from Microsoft.When a big company like Microsoft puts most of their resources into a new technology it’s hard for developers not to take notice.This new technology will certainly make an impact in the industry. ? As a programmer,C# is a language that will bene?t you if it’s add to your repertoire.With your Java skills,it’ll be a relatively small leap to learn this new language.Therefore,learning C# will increase your marketability in the workplace relatively painlessly. ? By learning C# and .NET,you’ll have several choices when implementing a solution for a speci?c project.For example,you can choose between .NET and J2EE when it comes to developing XML-based Web services. ? It’s arguable that Java lacks the performance needed when it comes to Windows applications development.C# enables you to develop fast Read more
-
C++ Primer
 Learning C++ is an adventure of discovery, particularly because the language accommodates several programming paradigms, including object-oriented programming, generic programming, and the traditional procedural programming. C++ was a moving target as the language added new features, but now, with the ISO/ANSI C++ Standard, Second Edition (2003), in place, the language has stabilized. Contemporary compilers support most or all of the features mandated by the standard, and programmers have had time to get used to applying these features. The fifth edition of this book, C++ Primer Plus, reflects the ISO/ANSI standard and describes this matured version of C++. C++ Primer Plus discusses the basic C language and presents C++ features, making this book self-contained. It presents C++ fundamentals and illustrates them with short, to-the-point programs that are easy to copy and experiment with. You’ll learn about input/output (I/O), how to make programs perform repetitive tasks and make choices, the many ways to handle data, and how to use functions. You’ll learn about the many features C++ has added to C, including the following: •Classes and objects • Inheritance •Polymorphism, virtual functions, and runtime type identification (RTTI) • Function overloading • Reference variables •Generic, or type-independent, programming, as provided by templates and the Standard Template Library (STL) •The exception mechanism for handling error conditions •Namespaces for managing names of functions, classes, and variables
Read more
Learning C++ is an adventure of discovery, particularly because the language accommodates several programming paradigms, including object-oriented programming, generic programming, and the traditional procedural programming. C++ was a moving target as the language added new features, but now, with the ISO/ANSI C++ Standard, Second Edition (2003), in place, the language has stabilized. Contemporary compilers support most or all of the features mandated by the standard, and programmers have had time to get used to applying these features. The fifth edition of this book, C++ Primer Plus, reflects the ISO/ANSI standard and describes this matured version of C++. C++ Primer Plus discusses the basic C language and presents C++ features, making this book self-contained. It presents C++ fundamentals and illustrates them with short, to-the-point programs that are easy to copy and experiment with. You’ll learn about input/output (I/O), how to make programs perform repetitive tasks and make choices, the many ways to handle data, and how to use functions. You’ll learn about the many features C++ has added to C, including the following: •Classes and objects • Inheritance •Polymorphism, virtual functions, and runtime type identification (RTTI) • Function overloading • Reference variables •Generic, or type-independent, programming, as provided by templates and the Standard Template Library (STL) •The exception mechanism for handling error conditions •Namespaces for managing names of functions, classes, and variables
Read more
-
C++ Programming-A Self Teaching Guide
 If you’re looking for an easy way to learn C++ and want to immediately start writing your own programs, this is the resource you need. The hands-on approach and step-by-step instruction guide you through each phase of C++ programming with easy-to-understand language from start to finish.
Whether or not you have previous C++ experience, you’ll get an excellent foundation here, discovering how computer programs and programming languages work. Next, you’ll learn the basics of the language— what data types, variables, and operators are and what they do, then on to functions, arrays, loops, and beyond. With no unnecessary, time-consuming material included, plus quizzes at the end of each chapter and a final exam, you’ll emerge a C++ pro, completing and running your very own complex programs in no time.
Read more
If you’re looking for an easy way to learn C++ and want to immediately start writing your own programs, this is the resource you need. The hands-on approach and step-by-step instruction guide you through each phase of C++ programming with easy-to-understand language from start to finish.
Whether or not you have previous C++ experience, you’ll get an excellent foundation here, discovering how computer programs and programming languages work. Next, you’ll learn the basics of the language— what data types, variables, and operators are and what they do, then on to functions, arrays, loops, and beyond. With no unnecessary, time-consuming material included, plus quizzes at the end of each chapter and a final exam, you’ll emerge a C++ pro, completing and running your very own complex programs in no time.
Read more
-
C++ standard Library
 This book presents ideas, concepts, solutions, and examples from many sources. In a way it does not seem fair that my name is the only name on the cover. Thus, I'd like to thank all the people and companies who helped and supported me during the past few years.
First, I'd like to thank Dietmar Kühl. Dietmar is an expert on C++, especially on input/output streams and internationalization (he implemented an I/O stream library just for fun). He not only translated major parts of this book from German to English, he also wrote sections of this book using his expertise. In addition, he provided me with invaluable feedback over the years.
Second, I'd like to thank all the reviewers and everyone else who gave me their opinion. These people endow the book with a quality it would never have had without their input. (Because the list is extensive, please fogive me for any oversight.) The reviewers for the English version of this book included Chuck Allison, Greg Comeau, James A. Crotinger, Gabriel Dos Reis, Alan Ezust, Nathan Meyers, Werner Mossner, Todd Veldhuizen, Chichiang Wan, Judy Ward, and Thomas Wikehult. The German reviewers included Ralf Boecker, Dirk Herrmann, Dietmar Kühl, Edda Lörke, Herbert Scheubner, Dominik Strasser, and Martin Weitzel. Additional input was provided by Matt Austern, Valentin Bonnard, Greg Colvin, Beman Dawes, Bill Gibbons, Lois Goldthwaite, Andrew Koenig, Steve Rumbsby, Bjarne Stroustrup, and David Vandevoorde. Read more
This book presents ideas, concepts, solutions, and examples from many sources. In a way it does not seem fair that my name is the only name on the cover. Thus, I'd like to thank all the people and companies who helped and supported me during the past few years.
First, I'd like to thank Dietmar Kühl. Dietmar is an expert on C++, especially on input/output streams and internationalization (he implemented an I/O stream library just for fun). He not only translated major parts of this book from German to English, he also wrote sections of this book using his expertise. In addition, he provided me with invaluable feedback over the years.
Second, I'd like to thank all the reviewers and everyone else who gave me their opinion. These people endow the book with a quality it would never have had without their input. (Because the list is extensive, please fogive me for any oversight.) The reviewers for the English version of this book included Chuck Allison, Greg Comeau, James A. Crotinger, Gabriel Dos Reis, Alan Ezust, Nathan Meyers, Werner Mossner, Todd Veldhuizen, Chichiang Wan, Judy Ward, and Thomas Wikehult. The German reviewers included Ralf Boecker, Dirk Herrmann, Dietmar Kühl, Edda Lörke, Herbert Scheubner, Dominik Strasser, and Martin Weitzel. Additional input was provided by Matt Austern, Valentin Bonnard, Greg Colvin, Beman Dawes, Bill Gibbons, Lois Goldthwaite, Andrew Koenig, Steve Rumbsby, Bjarne Stroustrup, and David Vandevoorde. Read more
-
Calculus
 Calculus (from Latin calculus, literally "small pebble used for counting on an abacus")[1] is the mathematical study of continuous change, in the same way that geometry is the study of shape and algebra is the study of generalizations of arithmetic operations. It has two major branches, differential calculus (concerning rates of change and slopes of curves),[2] and integral calculus (concerning accumulation of quantities and the areas under and between curves);[3] these two branches are related to each other by the fundamental theorem of calculus. Both branches make use of the fundamental notions of convergence of infinite sequences and infinite series to a well-defined limit. Generally, modern calculus is considered to have been developed in the 17th century by Isaac Newton and Gottfried Leibniz. Today, calculus has widespread uses in science, engineering and economics. Read more
Calculus (from Latin calculus, literally "small pebble used for counting on an abacus")[1] is the mathematical study of continuous change, in the same way that geometry is the study of shape and algebra is the study of generalizations of arithmetic operations. It has two major branches, differential calculus (concerning rates of change and slopes of curves),[2] and integral calculus (concerning accumulation of quantities and the areas under and between curves);[3] these two branches are related to each other by the fundamental theorem of calculus. Both branches make use of the fundamental notions of convergence of infinite sequences and infinite series to a well-defined limit. Generally, modern calculus is considered to have been developed in the 17th century by Isaac Newton and Gottfried Leibniz. Today, calculus has widespread uses in science, engineering and economics. Read more
-
Cancer Staging and Treatment
 A variety of end points may be measured and reported from clinical studies in oncology. These may include total mortality (or survival from the initiation of therapy), cause-specific mortality, quality of life, or indirect surrogates of these three outcomes, such as disease-free survival, progression-free survival, or tumor response rate. End points may also be determined within study designs of varying strength, ranging from the gold standard -- the randomized double-blinded controlled clinical trial -- to case series experiences from nonconsecutive patients. The PDQ editorial boards use a formal ranking system of levels of evidence to help the reader judge the strength of evidence linked to the reported results of a therapeutic strategy. For any given therapy, results can be ranked on each of the following two scales: (1) strength of the study design and (2) strength of the end points. Together, the two rankings give an idea of the overall level of evidence. Depending on perspective, different expert panels, professional organizations, or individual physicians may use different "cut points" of overall strength of evidence in formulating therapeutic guidelines or in taking action. However, a formal description of the level of evidence provides a uniform framework for the data, leading to specific recommendations Read more
A variety of end points may be measured and reported from clinical studies in oncology. These may include total mortality (or survival from the initiation of therapy), cause-specific mortality, quality of life, or indirect surrogates of these three outcomes, such as disease-free survival, progression-free survival, or tumor response rate. End points may also be determined within study designs of varying strength, ranging from the gold standard -- the randomized double-blinded controlled clinical trial -- to case series experiences from nonconsecutive patients. The PDQ editorial boards use a formal ranking system of levels of evidence to help the reader judge the strength of evidence linked to the reported results of a therapeutic strategy. For any given therapy, results can be ranked on each of the following two scales: (1) strength of the study design and (2) strength of the end points. Together, the two rankings give an idea of the overall level of evidence. Depending on perspective, different expert panels, professional organizations, or individual physicians may use different "cut points" of overall strength of evidence in formulating therapeutic guidelines or in taking action. However, a formal description of the level of evidence provides a uniform framework for the data, leading to specific recommendations Read more
-
Child and Adolescent Clinical Psychopharmacology
 Child and Adolescent Clinical Psychopharmacology. Since that time, there have been enormous changes in the drug armamentarium and in the practice of child, adolescent, and adult psychopharmacology. Although advances in the field almost always occur in adult psychopharmacology first, the new drugs are being introduced into the practice of child and adolescent psychopharmacology more and more rapidly. By 1995, when the second edition of this book was published, the atypical neuroleptics and serotonin specific reuptake inhibitors (SSRIs) were being introduced into clinical practice with children and adolescents. Today they have replaced the standard neuroleptics and the tricyclic antidepressents as the first line drugs used by most child and adolescent psychopharmacologists to treat schizophrenia, major depressive disorder, and many other childhood disorders. Read more
Child and Adolescent Clinical Psychopharmacology. Since that time, there have been enormous changes in the drug armamentarium and in the practice of child, adolescent, and adult psychopharmacology. Although advances in the field almost always occur in adult psychopharmacology first, the new drugs are being introduced into the practice of child and adolescent psychopharmacology more and more rapidly. By 1995, when the second edition of this book was published, the atypical neuroleptics and serotonin specific reuptake inhibitors (SSRIs) were being introduced into clinical practice with children and adolescents. Today they have replaced the standard neuroleptics and the tricyclic antidepressents as the first line drugs used by most child and adolescent psychopharmacologists to treat schizophrenia, major depressive disorder, and many other childhood disorders. Read more
-
Clinical Anesthesia Procedures
 Clinical Anesthesia Procedures of the Massachusetts General Hospital was written by residents, fellows, staff, and alumni of the Department of Anesthesia and Critical Care at the Massachusetts General Hospital. This manual continues to emphasize the clinical fundamentals involved in the safe administration of anesthesia, perioperative care, and pain management. The suggestions reflect current clinical practices at our hospital; other methods may be equally effective.
This handbook complements readings in textbooks and journals and assumes some prior knowledge of anesthesia and critical care. It is designed to be an accessible and accurate source of information for practicing anesthesiologists, anesthesia residents, nurse anesthetists, medical students, medical and surgical residents, nurses, respiratory therapists, and other health care professionals involved in perioperative care. The manual is not intended to replace experienced clinical teaching or substitute for detailed study. Each chapter contains a reading list for those who desire additional information on a topic. Read more
Clinical Anesthesia Procedures of the Massachusetts General Hospital was written by residents, fellows, staff, and alumni of the Department of Anesthesia and Critical Care at the Massachusetts General Hospital. This manual continues to emphasize the clinical fundamentals involved in the safe administration of anesthesia, perioperative care, and pain management. The suggestions reflect current clinical practices at our hospital; other methods may be equally effective.
This handbook complements readings in textbooks and journals and assumes some prior knowledge of anesthesia and critical care. It is designed to be an accessible and accurate source of information for practicing anesthesiologists, anesthesia residents, nurse anesthetists, medical students, medical and surgical residents, nurses, respiratory therapists, and other health care professionals involved in perioperative care. The manual is not intended to replace experienced clinical teaching or substitute for detailed study. Each chapter contains a reading list for those who desire additional information on a topic. Read more
-
Clinical Cardiac Electrophysiology
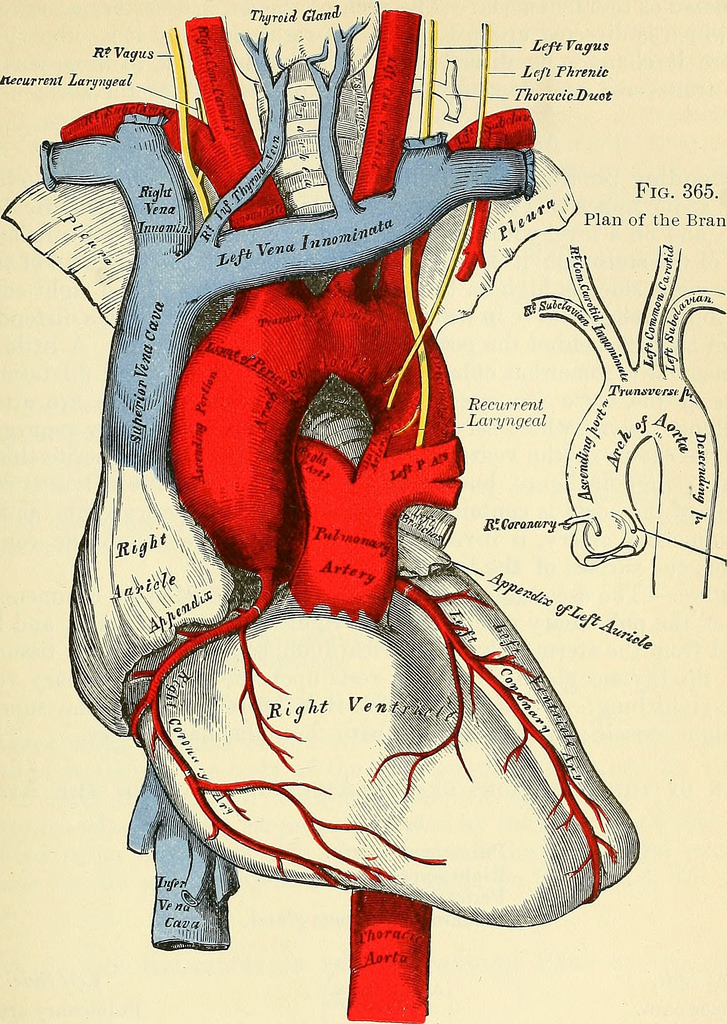 The study of the heart as an electrical organ has fascinated physiologists and physicians for nearly a century and a half. Matteucci ( 1) studied electrical current in pigeon hearts, and Kölliker and Müller (2) studied discrete electrical activity in association with each cardiac contraction in the frog. Study of the human ECG awaited the discoveries of Waller (3) and, most important Einthoven (4), whose use and development of the string galvanometer permitted the standardization and widespread use of that instrument. Almost simultaneously, anatomists and pathologists were tracing the atrioventricular (A–V) conduction system. Many of the pathways, both normal and abnormal, still bear the names of the men who described them. This group of men included Wilhem His ( 5), who discovered the muscle bundle joining the atrial and ventricular septae that is known as the common A–V bundle or the bundle of His Read more
The study of the heart as an electrical organ has fascinated physiologists and physicians for nearly a century and a half. Matteucci ( 1) studied electrical current in pigeon hearts, and Kölliker and Müller (2) studied discrete electrical activity in association with each cardiac contraction in the frog. Study of the human ECG awaited the discoveries of Waller (3) and, most important Einthoven (4), whose use and development of the string galvanometer permitted the standardization and widespread use of that instrument. Almost simultaneously, anatomists and pathologists were tracing the atrioventricular (A–V) conduction system. Many of the pathways, both normal and abnormal, still bear the names of the men who described them. This group of men included Wilhem His ( 5), who discovered the muscle bundle joining the atrial and ventricular septae that is known as the common A–V bundle or the bundle of His Read more
-
CLINICAL GENETICS
 Since the first edition of this book in 1989 there have been enormous changes in clinical genetics, reflecting the knowledge generated from the tremendous advances in molecular biology, culminating in the publication of the first draft of the human genome sequence in 2001, and the dissemination of information via the internet. The principles of genetic assessment and the aims of genetic counselling have not changed, but the classification of genetic disease and the practice of clinical genetics has been significantly altered by this new knowledge. To interpret all the information now available it is necessary to understand the basic principles of inheritance and its chromosomal and molecular basis. Recent advances in medical genetics have had a considerable impact on other specialties, providing a new range of molecular diagnostic tests applicable to many branches of medicine, and more patients are presenting to their general practitioners with concerns about a family history of disorders such as cancer. Increasingly, other specialties are involved in the genetic aspects of the conditions they treat and need to provide information about genetic risk, undertake genetic testing and provide appropriate counselling. All medical students, irrespective of their eventual career choice therefore need to be familiar with genetic principles, both scientific and clinical, and to be aware of the ethical implications of genetic technologies that enable manipulation of the human genome that may have future application in areas such as gene therapy of human cloning. The aim of this third edition of the ABC is therefore to provide an introduction to the various aspects of medical genetics for medical students, clinicians, nurses and allied professionals who are not working within the field of genetics, to generate an interest in the subject and to guide readers in the direction of further, more detailed information. Read more
Since the first edition of this book in 1989 there have been enormous changes in clinical genetics, reflecting the knowledge generated from the tremendous advances in molecular biology, culminating in the publication of the first draft of the human genome sequence in 2001, and the dissemination of information via the internet. The principles of genetic assessment and the aims of genetic counselling have not changed, but the classification of genetic disease and the practice of clinical genetics has been significantly altered by this new knowledge. To interpret all the information now available it is necessary to understand the basic principles of inheritance and its chromosomal and molecular basis. Recent advances in medical genetics have had a considerable impact on other specialties, providing a new range of molecular diagnostic tests applicable to many branches of medicine, and more patients are presenting to their general practitioners with concerns about a family history of disorders such as cancer. Increasingly, other specialties are involved in the genetic aspects of the conditions they treat and need to provide information about genetic risk, undertake genetic testing and provide appropriate counselling. All medical students, irrespective of their eventual career choice therefore need to be familiar with genetic principles, both scientific and clinical, and to be aware of the ethical implications of genetic technologies that enable manipulation of the human genome that may have future application in areas such as gene therapy of human cloning. The aim of this third edition of the ABC is therefore to provide an introduction to the various aspects of medical genetics for medical students, clinicians, nurses and allied professionals who are not working within the field of genetics, to generate an interest in the subject and to guide readers in the direction of further, more detailed information. Read more
-
Clinical Neurology 5th edition
 The fifth edition of Clinical Neurology, like its predecessors, offers a problem-oriented approach to neurology based on the authors' experience in teaching medical students and house staff at the University of California, San Francisco. Chapters are organized according to problems such as headache, seizures, stroke, and coma, because these are the conditions for which patients usually seek medical care. Careful history taking and neurologic examination are emphasized, as these remain the cornerstones of neurologic diagnosis, even in an era of technologic diagnostic advances. Read more
The fifth edition of Clinical Neurology, like its predecessors, offers a problem-oriented approach to neurology based on the authors' experience in teaching medical students and house staff at the University of California, San Francisco. Chapters are organized according to problems such as headache, seizures, stroke, and coma, because these are the conditions for which patients usually seek medical care. Careful history taking and neurologic examination are emphasized, as these remain the cornerstones of neurologic diagnosis, even in an era of technologic diagnostic advances. Read more
-
Computational Molecular Biology
 Computational biology involves the development and application of data-analytical and theoretical methods, mathematical modeling and computational simulation techniques to the study of biological, behavioral, and social systems.[1] The field is broadly defined and includes foundations in computer science, applied mathematics, animation, statistics, biochemistry, chemistry, biophysics, molecular biology, genetics, genomics, ecology, evolution, anatomy, neuroscience, and visualization.[2]
Computational biology is different from biological computation, which is a subfield of computer science and computer engineering using bioengineering and biology to build computers, but is similar to bioinformatics, which is an interdisciplinary science using computers to store and process biological data. Read more
Computational biology involves the development and application of data-analytical and theoretical methods, mathematical modeling and computational simulation techniques to the study of biological, behavioral, and social systems.[1] The field is broadly defined and includes foundations in computer science, applied mathematics, animation, statistics, biochemistry, chemistry, biophysics, molecular biology, genetics, genomics, ecology, evolution, anatomy, neuroscience, and visualization.[2]
Computational biology is different from biological computation, which is a subfield of computer science and computer engineering using bioengineering and biology to build computers, but is similar to bioinformatics, which is an interdisciplinary science using computers to store and process biological data. Read more
-
Computer Applications -C++ Performance programming techniques
 Efficient C++ explodes that myth. Written by two authors with first-hand experience wringing the last ounce of performance from commercial C++ applications, this book demonstrates the potential of C++ to produce highly efficient programs. The book reveals practical, everyday object-oriented design principles and C++ coding techniques that can yield large performance improvements. It points out common pitfalls in both design and code that generate hidden operating costs.
This book focuses on combining C++'s power and flexibility with high performance and scalability, resulting in the best of both worlds. Specific topics include temporary objects, memory management, templates, inheritance, virtual functions, inlining, reference-counting, STL, and much more. Read more
Efficient C++ explodes that myth. Written by two authors with first-hand experience wringing the last ounce of performance from commercial C++ applications, this book demonstrates the potential of C++ to produce highly efficient programs. The book reveals practical, everyday object-oriented design principles and C++ coding techniques that can yield large performance improvements. It points out common pitfalls in both design and code that generate hidden operating costs.
This book focuses on combining C++'s power and flexibility with high performance and scalability, resulting in the best of both worlds. Specific topics include temporary objects, memory management, templates, inheritance, virtual functions, inlining, reference-counting, STL, and much more. Read more
-
Computer Applications- C++ network programming
 C++ Network Programming, Volume 2, focuses on ACE frameworks, providing thorough coverage of the concepts, patterns, and usage rules that form their structure. This book is a practical guide to designing object-oriented frameworks and shows developers how to apply frameworks to concurrent networked applications. C++ Networking, Volume 1, introduced ACE and the wrapper facades, which are basic network computing ingredients. Volume 2 explains how frameworks build on wrapper facades to provide higher-level communication services.
Read more
C++ Network Programming, Volume 2, focuses on ACE frameworks, providing thorough coverage of the concepts, patterns, and usage rules that form their structure. This book is a practical guide to designing object-oriented frameworks and shows developers how to apply frameworks to concurrent networked applications. C++ Networking, Volume 1, introduced ACE and the wrapper facades, which are basic network computing ingredients. Volume 2 explains how frameworks build on wrapper facades to provide higher-level communication services.
Read more
-
Computer Applications-C++ Compiler
 C++ is a large, complex language, and learning it is never entirely easy. But some concepts and techniques must be thoroughly mastered if programmers are ever to do professional-quality work. This book cuts through the technical details to reveal what is commonly understood to be absolutely essential. In one slim volume, Steve Dewhurst distills what he and other experienced managers, trainers, and authors have found to be the most critical knowledge required for successful C++ programming. It doesn't matter where or when you first learned C++. Before you take another step, use this book as your guide to make sure you've got it right!
Read more
C++ is a large, complex language, and learning it is never entirely easy. But some concepts and techniques must be thoroughly mastered if programmers are ever to do professional-quality work. This book cuts through the technical details to reveal what is commonly understood to be absolutely essential. In one slim volume, Steve Dewhurst distills what he and other experienced managers, trainers, and authors have found to be the most critical knowledge required for successful C++ programming. It doesn't matter where or when you first learned C++. Before you take another step, use this book as your guide to make sure you've got it right!
Read more
-
Computer Applications-C++ Compiler
 C++ Compiler optimizes performance for applications running on Intel architecture-based computers. Performance gains are a result of the features listed below:
Feature Benefit High Performance Achieve a significant performance gain by using optimizations Support for Streaming SIMD Extensions Advantage of new Intel microarchitecture Automatic vectorizer Advantage of parallelism in your code achieved automatically OpenMP* Support Shared memory parallel programming Floating-point optimizations Improved floating-point performance Data prefetching Improved performance due to the accelerated data delivery Interprocedural optimizations Achieve a significant performance gain by optimizing between modules Whole program optimization Improved performance between modules in larger applications Profile-guided optimization Improved performance based on profiling frequently-used functions Processor dispatch Taking advantage of the latest Intel architecture features while maintaining object code compatibility with Read more
C++ Compiler optimizes performance for applications running on Intel architecture-based computers. Performance gains are a result of the features listed below:
Feature Benefit High Performance Achieve a significant performance gain by using optimizations Support for Streaming SIMD Extensions Advantage of new Intel microarchitecture Automatic vectorizer Advantage of parallelism in your code achieved automatically OpenMP* Support Shared memory parallel programming Floating-point optimizations Improved floating-point performance Data prefetching Improved performance due to the accelerated data delivery Interprocedural optimizations Achieve a significant performance gain by optimizing between modules Whole program optimization Improved performance between modules in larger applications Profile-guided optimization Improved performance based on profiling frequently-used functions Processor dispatch Taking advantage of the latest Intel architecture features while maintaining object code compatibility with Read more
-
Computer applications-In basic c programming
 C is an imperative procedural language. It was designed to be compiled using a relatively straightforward compiler, to provide low-level access to memory, to provide language constructs that map efficiently to machine instructions, and to require minimal run-time support. Despite its low-level capabilities, the language was designed to encourage cross-platform programming. A standards-compliant and portably written C program can be compiled for a very wide variety of computer platforms and operating systems with few changes to its source code. The language has become available on a very wide range of platforms, from embedded microcontrollers to supercomputers Read more
C is an imperative procedural language. It was designed to be compiled using a relatively straightforward compiler, to provide low-level access to memory, to provide language constructs that map efficiently to machine instructions, and to require minimal run-time support. Despite its low-level capabilities, the language was designed to encourage cross-platform programming. A standards-compliant and portably written C program can be compiled for a very wide variety of computer platforms and operating systems with few changes to its source code. The language has become available on a very wide range of platforms, from embedded microcontrollers to supercomputers Read more
-
Core Java
 The seventh edition of Core Java 2, Volume II, covers advanced user-interface programming and the enterprise features of the Java 2 Platform, Standard Edition (J2SE™). Like Volume I (which covers the most important language and library features), this book has been completely updated and revised for J2SE 5.0. All of the sample programs have been updated and carefully crafted to illustrate practical solutions to the type of real-world problems professional developers encounter
Read more
The seventh edition of Core Java 2, Volume II, covers advanced user-interface programming and the enterprise features of the Java 2 Platform, Standard Edition (J2SE™). Like Volume I (which covers the most important language and library features), this book has been completely updated and revised for J2SE 5.0. All of the sample programs have been updated and carefully crafted to illustrate practical solutions to the type of real-world problems professional developers encounter
Read more
-
Crackproof Your Software
 This book is designed to help all programmers who have ever written their own software to better protect their software from illegal copying. It will also be useful to programmers creating freeware who wish to protect their source code.
The idea to write a book like this came to me some time ago when I realized how poorly the topic is covered and how difficult it is to acquire the information necessary to adequately protect software. When I was involved with game production in the Czech and Slovak Republics, I was astonished at how simple their protection was, and that very often they had no protection at all — yet it is so easy to protect software, at least at a basic level.
The problem lies in the lack of information and experience in this field. That's why I wrote this book, which will present many previously unaddressed topics concerning software protection.
Read more
This book is designed to help all programmers who have ever written their own software to better protect their software from illegal copying. It will also be useful to programmers creating freeware who wish to protect their source code.
The idea to write a book like this came to me some time ago when I realized how poorly the topic is covered and how difficult it is to acquire the information necessary to adequately protect software. When I was involved with game production in the Czech and Slovak Republics, I was astonished at how simple their protection was, and that very often they had no protection at all — yet it is so easy to protect software, at least at a basic level.
The problem lies in the lack of information and experience in this field. That's why I wrote this book, which will present many previously unaddressed topics concerning software protection.
Read more
-
CSRF: Attack and Defense
 CSRF stands for cross-site request forgery. It’s also known as session riding or XSRF. CSRF takes advantage of the inherent statelessness of the web to simulate user actions on one website (the target site) from another website (the attacking site). Typically, CSRF will be used to perform actions of the attacker’s choosing using the victim’s authenticated session. If a victim has logged into the target site, an attacker can coerce the victim’s browser to perform actions on the target website. Read more
CSRF stands for cross-site request forgery. It’s also known as session riding or XSRF. CSRF takes advantage of the inherent statelessness of the web to simulate user actions on one website (the target site) from another website (the attacking site). Typically, CSRF will be used to perform actions of the attacker’s choosing using the victim’s authenticated session. If a victim has logged into the target site, an attacker can coerce the victim’s browser to perform actions on the target website. Read more
-
CSS Hacks and Filters
 The theory of Cascading Style Sheets (CSS) is a means to an end:better,more efficient Web site design.In the real world,however,CSS does not provide a perfect,clear-cut path to that goal.To achieve the promise of CSS,working designers have employed a series of workarounds known collectively as hacks.At the most basic level,a CSS hack is a modification to the standard CSS code.Like any deviation from the norm,the use of CSS hacks has both its supporters and detractors:Some designers feel CSS hacks are an absolute necessity and others are fervently opposed to them. To figure out why the Web design community is divided over CSS hacks— and which camp you should be in—you’ll need a little background on the emergence of CSS.
Read more
The theory of Cascading Style Sheets (CSS) is a means to an end:better,more efficient Web site design.In the real world,however,CSS does not provide a perfect,clear-cut path to that goal.To achieve the promise of CSS,working designers have employed a series of workarounds known collectively as hacks.At the most basic level,a CSS hack is a modification to the standard CSS code.Like any deviation from the norm,the use of CSS hacks has both its supporters and detractors:Some designers feel CSS hacks are an absolute necessity and others are fervently opposed to them. To figure out why the Web design community is divided over CSS hacks— and which camp you should be in—you’ll need a little background on the emergence of CSS.
Read more
-
Current Pediatric Diagnosis & Treatment
 Current Pediatric Diagnosis & Treatment features practical, up-to-date, well-referenced information on the care of children from birth through infancy and adolescence. CPDT emphasizes the clinical aspects of pediatric care while also covering the important underlying principles. Its goal is to provide a guide to diagnosis, understanding, and treatment of the medical problems of all pediatric patients in an easy-to-use and readable format
Read more
Current Pediatric Diagnosis & Treatment features practical, up-to-date, well-referenced information on the care of children from birth through infancy and adolescence. CPDT emphasizes the clinical aspects of pediatric care while also covering the important underlying principles. Its goal is to provide a guide to diagnosis, understanding, and treatment of the medical problems of all pediatric patients in an easy-to-use and readable format
Read more
-
Current Topics in Computational Molecular Biology
 the book would be useful to a broad readership, including students, nonprofessionals, and bioinformatic experts who want to brush up topics related to their own research areas. The 19 chapters are grouped into four sections. The introductory section is a chapter by Temple Smith, who attempts to set bioinformatics into a useful historical context. For over half a century, mathematics and even computer-based analyses have played a fundamental role in bringing our biological understanding to its current level. To a very large extent, what is new is the type and sheer volume of new data. The birth of bioinformatics was a direct result of this new data explosion. As this interdisciplinary area matures, it is providing the data and computational support for functional genomics, which is de?ned as the research domain focused on linking the behavior of cells, organisms, and populations to the information encoded in the genomes. The second of the four sections consists of six chapters on computational methods for comparative sequence and genome analyses Read more
the book would be useful to a broad readership, including students, nonprofessionals, and bioinformatic experts who want to brush up topics related to their own research areas. The 19 chapters are grouped into four sections. The introductory section is a chapter by Temple Smith, who attempts to set bioinformatics into a useful historical context. For over half a century, mathematics and even computer-based analyses have played a fundamental role in bringing our biological understanding to its current level. To a very large extent, what is new is the type and sheer volume of new data. The birth of bioinformatics was a direct result of this new data explosion. As this interdisciplinary area matures, it is providing the data and computational support for functional genomics, which is de?ned as the research domain focused on linking the behavior of cells, organisms, and populations to the information encoded in the genomes. The second of the four sections consists of six chapters on computational methods for comparative sequence and genome analyses Read more
-
Cybercrime
 This book, more than any other I’ve written up to this point in my life, was a labor of love. It allowed me to combine the knowledge and experience of two careers (over a decade in government and law enforcement, and close to another decade in the computer ?eld, encompassing almost 20 years of working with computers as a hobbyist).When I was a working police of?cer, computer crime was an esoteric specialty area—investigators in small- and medium-sized agencies rarely encountered a case involving digital evidence, and the term cybercrime was unheard of in most police circles. Today, all of that has changed. In fact, our whole way of life has changed over the past two decades, and many of those changes can be directly attributed to the Internet. I met my husband on the Net in 1994, when I was still a cop and he was practicing medicine.We’ve come a long way, baby, since then. Today, the two of us make our livings online, as authors, consultants, and providers of online training. Ninety percent of our business is conducted via the Internet. Many of our friendships began in the virtual world, and we use e-mail to keep in touch with family members in remote locations, with whom we probably would rarely have contact otherwise.There are plenty of others out there like us, whose “real world” lives are inextricably intertwined with the time that we spend in the netherworld of cyberspace. It is inevitable, I suppose, that members of the same antisocial element of society I dealt with as a police of?cer would ?nd their ways onto the Net, as well. Read more
This book, more than any other I’ve written up to this point in my life, was a labor of love. It allowed me to combine the knowledge and experience of two careers (over a decade in government and law enforcement, and close to another decade in the computer ?eld, encompassing almost 20 years of working with computers as a hobbyist).When I was a working police of?cer, computer crime was an esoteric specialty area—investigators in small- and medium-sized agencies rarely encountered a case involving digital evidence, and the term cybercrime was unheard of in most police circles. Today, all of that has changed. In fact, our whole way of life has changed over the past two decades, and many of those changes can be directly attributed to the Internet. I met my husband on the Net in 1994, when I was still a cop and he was practicing medicine.We’ve come a long way, baby, since then. Today, the two of us make our livings online, as authors, consultants, and providers of online training. Ninety percent of our business is conducted via the Internet. Many of our friendships began in the virtual world, and we use e-mail to keep in touch with family members in remote locations, with whom we probably would rarely have contact otherwise.There are plenty of others out there like us, whose “real world” lives are inextricably intertwined with the time that we spend in the netherworld of cyberspace. It is inevitable, I suppose, that members of the same antisocial element of society I dealt with as a police of?cer would ?nd their ways onto the Net, as well. Read more
-
C|HFI – Computer Hacking Forensic Investigator
 Hacking and electronic crimes sophistication has grown at an exponential rate in recent years. In fact, recent reports have indicated[CC1] that cyber crime already surpasses the illegal drug trade! Unethical hackers, better known as black hats, are preying on information systems of government, corporate, public, and private networks and are constantly testing the security mechanisms of these organizations to the limit with the sole aim of exploiting them and profiting from the exercise. High-profile crimes have proven that the traditional approach to computer security is simply not sufficient, even with the strongest perimeter, properly configured defense mechanisms such as firewalls, intrusion detection, and prevention systems, strong end-to-end encryption standards, and anti-virus software. Hackers have proven their dedication and ability to systematically penetrate networks all over the world. In some cases, black hats may be able to execute attacks so flawlessly that they can compromise a system, steal everything of value, and completely erase their tracks in less than 20 minutes! The EC-Council Press is dedicated to stopping hackers in their tracks. Read more
Hacking and electronic crimes sophistication has grown at an exponential rate in recent years. In fact, recent reports have indicated[CC1] that cyber crime already surpasses the illegal drug trade! Unethical hackers, better known as black hats, are preying on information systems of government, corporate, public, and private networks and are constantly testing the security mechanisms of these organizations to the limit with the sole aim of exploiting them and profiting from the exercise. High-profile crimes have proven that the traditional approach to computer security is simply not sufficient, even with the strongest perimeter, properly configured defense mechanisms such as firewalls, intrusion detection, and prevention systems, strong end-to-end encryption standards, and anti-virus software. Hackers have proven their dedication and ability to systematically penetrate networks all over the world. In some cases, black hats may be able to execute attacks so flawlessly that they can compromise a system, steal everything of value, and completely erase their tracks in less than 20 minutes! The EC-Council Press is dedicated to stopping hackers in their tracks. Read more
-
Eclipse Distilled
 Organized for rapid access, focused on productivity, Eclipse Distilled brings together all the answers you need to make the most of today's most powerful Java development environment. David Carlson introduces proven best practices for working with Eclipse, and shows exactly how to integrate Eclipse into any Agile development process.
Part I shows how to customize workspaces, projects, perspectives, and views for optimal efficiencyand how to leverage Eclipse's rapid development, navigation, and debugging features to maximize both productivity and code quality. Part II focuses entirely on Agile development, demonstrating how Eclipse can simplify team ownership, refactoring, continuous testing, continuousintegration, and other Agile practices. Coverage includes
Managing Eclipse projects from start to finish: handling both content and complexit Read more
Organized for rapid access, focused on productivity, Eclipse Distilled brings together all the answers you need to make the most of today's most powerful Java development environment. David Carlson introduces proven best practices for working with Eclipse, and shows exactly how to integrate Eclipse into any Agile development process.
Part I shows how to customize workspaces, projects, perspectives, and views for optimal efficiencyand how to leverage Eclipse's rapid development, navigation, and debugging features to maximize both productivity and code quality. Part II focuses entirely on Agile development, demonstrating how Eclipse can simplify team ownership, refactoring, continuous testing, continuousintegration, and other Agile practices. Coverage includes
Managing Eclipse projects from start to finish: handling both content and complexit Read more
-
Eclipse: Step-by-Step
 Just as Eclipse is one of the greatest breakthroughs in programming since the graphical user interface, this book may be the greatest breakthrough you will experience in learning a new programming environment. The systematic, step-by-step approach will get you started in the least amount of time possible, and will give you a tremendous foundation to propel you into the future of programming.
If you have any programming experience at all, this book will teach you how to use Eclipse in the most effective way, systematically guiding you through each screen, telling you what to type, which buttons to push, and walking you through building your first application in Eclipse. Where you go from there is up to you!
You will be able to use this book even if your only knowledge of Java is how to spell it. However, that doesn’t mean that Java programmers can’t benefit! Even experienced developers can make use of this book, since it covers three areas that are of crucial interest these days: Eclipse, IBM’s Software Widget Toolkit (the SWT), and JDBC. If you’ve wanted to see a working application using any of those technologies, then this book is for you. Read more
Just as Eclipse is one of the greatest breakthroughs in programming since the graphical user interface, this book may be the greatest breakthrough you will experience in learning a new programming environment. The systematic, step-by-step approach will get you started in the least amount of time possible, and will give you a tremendous foundation to propel you into the future of programming.
If you have any programming experience at all, this book will teach you how to use Eclipse in the most effective way, systematically guiding you through each screen, telling you what to type, which buttons to push, and walking you through building your first application in Eclipse. Where you go from there is up to you!
You will be able to use this book even if your only knowledge of Java is how to spell it. However, that doesn’t mean that Java programmers can’t benefit! Even experienced developers can make use of this book, since it covers three areas that are of crucial interest these days: Eclipse, IBM’s Software Widget Toolkit (the SWT), and JDBC. If you’ve wanted to see a working application using any of those technologies, then this book is for you. Read more
-
Economics
 Economic well-being is created in a production process, meaning all economic activities that aim directly or indirectly to satisfy human wants and needs. The degree to which the needs are satisfied is often accepted as a measure of economic well-being. In production there are two features which explain increasing economic well-being. They are improving quality-price-ratio of goods and services and increasing incomes from growing and more efficient market production.
The most important forms of production are
market production
public production
household production Read more
Economic well-being is created in a production process, meaning all economic activities that aim directly or indirectly to satisfy human wants and needs. The degree to which the needs are satisfied is often accepted as a measure of economic well-being. In production there are two features which explain increasing economic well-being. They are improving quality-price-ratio of goods and services and increasing incomes from growing and more efficient market production.
The most important forms of production are
market production
public production
household production Read more
-
Encyclopedia of Biological Chemistry
 The Journal of Biological Chemistry is a weekly peer-reviewed scientific journal that was established in 1905.[1] Since 1925, it is published by the American Society for Biochemistry and Molecular Biology. It covers research in areas of biochemistry and molecular biology. The editor-in-chief is Lila Gierasch.[2] All its articles are available free after one year of publication. In press articles are available free on its website immediately after acceptance Read more
The Journal of Biological Chemistry is a weekly peer-reviewed scientific journal that was established in 1905.[1] Since 1925, it is published by the American Society for Biochemistry and Molecular Biology. It covers research in areas of biochemistry and molecular biology. The editor-in-chief is Lila Gierasch.[2] All its articles are available free after one year of publication. In press articles are available free on its website immediately after acceptance Read more
-
ENERGY METABOLISM IN THE BRAIN
 Studies of glucose metabolism in the brain reflect a dichotomy due to the fact that the complex, integrating functions of the brain can only be stud- ied in the intact, functioning brain in the conscious individual (human or animal), whereas properties of brain cells, cell-cell interactions, and mech- anisms are most readily evaluated in vitro under controlled conditions us- ing brain slices, subcellular fractions or purified, isolated cells of different types. In viuo studies have most commonly been done in studies with labeled 2-deoxy-@glucose (DG) or 2-fluorodeoxyglucose (FDG). “1maging”with DG revolutionized investigations of correlations between brain function and brain metabolism (Sokoloff et aZ., 1977)) because this glucose analog enables local functional analysis of hexokinase activity in viva, from which local rates of glucose utilization can be calculated under steady-state conditions. On the other side, it is becoming overwhelmingly clear that such studies repre- sent only one aspect of brain function, i.e., the “big picture,” identifying the pathways and magnitude of functional metabolic activities; the underlying contributions of different cells and cell types in the brain are not identified and quantified, and the character of the energy-requiring processes are not determined. Brain cells can behave metabolically in very different manners in response to various stimuli and interact so that one cell type may gener- ate a glucose metabolite (e.g., glutamate or lactate), which then undergoes “metabolic trafficking” to sustain function, to be further metabolized in a different cell type, or even to leave the activated area. These heterogeneous interactions have the consequence that imaging of overall brain metabolism cannot provide a picture of glucose metabolism at the cellular level. A variety of in vitro methods have been used to assess metabolic activities Read more
Studies of glucose metabolism in the brain reflect a dichotomy due to the fact that the complex, integrating functions of the brain can only be stud- ied in the intact, functioning brain in the conscious individual (human or animal), whereas properties of brain cells, cell-cell interactions, and mech- anisms are most readily evaluated in vitro under controlled conditions us- ing brain slices, subcellular fractions or purified, isolated cells of different types. In viuo studies have most commonly been done in studies with labeled 2-deoxy-@glucose (DG) or 2-fluorodeoxyglucose (FDG). “1maging”with DG revolutionized investigations of correlations between brain function and brain metabolism (Sokoloff et aZ., 1977)) because this glucose analog enables local functional analysis of hexokinase activity in viva, from which local rates of glucose utilization can be calculated under steady-state conditions. On the other side, it is becoming overwhelmingly clear that such studies repre- sent only one aspect of brain function, i.e., the “big picture,” identifying the pathways and magnitude of functional metabolic activities; the underlying contributions of different cells and cell types in the brain are not identified and quantified, and the character of the energy-requiring processes are not determined. Brain cells can behave metabolically in very different manners in response to various stimuli and interact so that one cell type may gener- ate a glucose metabolite (e.g., glutamate or lactate), which then undergoes “metabolic trafficking” to sustain function, to be further metabolized in a different cell type, or even to leave the activated area. These heterogeneous interactions have the consequence that imaging of overall brain metabolism cannot provide a picture of glucose metabolism at the cellular level. A variety of in vitro methods have been used to assess metabolic activities Read more
-
English Grammar
 English grammar is the way in which meanings are encoded into wordings in the English language. This includes the structure of words, phrases, clauses, and sentences, right up to the structure of whole texts.
There are historical, social, cultural and regional variations of English. Divergences from the grammar described here occur in some dialects of English. This article describes a generalized present-day Standard English, the form of speech and writing found in types of public discourse including broadcasting, education, entertainment, government, and news including both formal and informal speech. There are differences in grammar between the standard forms of British, American, and Australian English, although these are minor compared with the differences in vocabulary and pronunciation. Read more
English grammar is the way in which meanings are encoded into wordings in the English language. This includes the structure of words, phrases, clauses, and sentences, right up to the structure of whole texts.
There are historical, social, cultural and regional variations of English. Divergences from the grammar described here occur in some dialects of English. This article describes a generalized present-day Standard English, the form of speech and writing found in types of public discourse including broadcasting, education, entertainment, government, and news including both formal and informal speech. There are differences in grammar between the standard forms of British, American, and Australian English, although these are minor compared with the differences in vocabulary and pronunciation. Read more
-
Enterprise J2ME: Developing Mobile Java Applications
 J2ME offers an extraordinarily flexible and robust platform for developing mobile applications with enterprise-class performance, reliability, and value. Now, leading mobile developer Michael Yuan covers every aspect of building industrialstrength applications with J2ME: design, architecture, tools, processes, business issues, and more.
Yuan introduces innovations that make the platform even more powerful, ranging from
new J2ME profiles and wireless messaging APIs to mobile databases and web services tools. These innovations allow existing Java(TM) developers (especially J2EE(TM) developers) to leverage their skills and add mobility to enterprise applications. Yuan also presents more than a dozen complete sample applicationsincluding the application that earned him the grand prize in Nextel, Sun, and Motorola's nationwide wireless developer contest. Read more
J2ME offers an extraordinarily flexible and robust platform for developing mobile applications with enterprise-class performance, reliability, and value. Now, leading mobile developer Michael Yuan covers every aspect of building industrialstrength applications with J2ME: design, architecture, tools, processes, business issues, and more.
Yuan introduces innovations that make the platform even more powerful, ranging from
new J2ME profiles and wireless messaging APIs to mobile databases and web services tools. These innovations allow existing Java(TM) developers (especially J2EE(TM) developers) to leverage their skills and add mobility to enterprise applications. Yuan also presents more than a dozen complete sample applicationsincluding the application that earned him the grand prize in Nextel, Sun, and Motorola's nationwide wireless developer contest. Read more
-
Enterprise JavaBeans
 Enterprise JavaBeans are easy. Well, at least when you compare EJB to what you’d have to do to write your own scalable, transactional, secure, persistent, concurrent enterprise component server. In this chapter, we’ll develop, deploy, and run an EJB application, and then dive into the details. Before we’re done, we’ll look at the use, benefi ts, and characteristics of EJB, and we’ll look (briefl y) at how EJB containers work
Read more
Enterprise JavaBeans are easy. Well, at least when you compare EJB to what you’d have to do to write your own scalable, transactional, secure, persistent, concurrent enterprise component server. In this chapter, we’ll develop, deploy, and run an EJB application, and then dive into the details. Before we’re done, we’ll look at the use, benefi ts, and characteristics of EJB, and we’ll look (briefl y) at how EJB containers work
Read more
-
Essentials of Complementary and Alternative Medicine
 This book is the result of many minds, hearts, and souls who have shared a vision of healing with me. It would not exist without them. It began when Lance Sholdt, then at the Uniformed Services University of the Health Sciences, asked if I would work with him to put together a course in complementary and alternative medicine for the medical students. His careful construction of this course helped us outline the contents of the book. This book is the brainchild of Jeff Levin. He was the first to suggest that a textbook like this was needed and could be written. His heartfelt work and attention to detail kept things moving when I was bogged down. Janette Carlucci is the soul of the book, managing both the special features and the day-to-day contact with the many authors. To her, a special thanks on this journey. Ron Chez provided a much needed balance for the book. He was always ready and willing to assist with a critical eye and keep us anchored to how this book could be of benefit for patients. I would also like to thank the editors, Jane Velker, Beth Goldner, and Joyce Murphy, for understanding the complexity of the topic and for a commitment to quality over deadlines. And Tim Hiscock for finally saying that we were going to press—ready or not. I would just as soon have worked another three years on it as finish. Read more
This book is the result of many minds, hearts, and souls who have shared a vision of healing with me. It would not exist without them. It began when Lance Sholdt, then at the Uniformed Services University of the Health Sciences, asked if I would work with him to put together a course in complementary and alternative medicine for the medical students. His careful construction of this course helped us outline the contents of the book. This book is the brainchild of Jeff Levin. He was the first to suggest that a textbook like this was needed and could be written. His heartfelt work and attention to detail kept things moving when I was bogged down. Janette Carlucci is the soul of the book, managing both the special features and the day-to-day contact with the many authors. To her, a special thanks on this journey. Ron Chez provided a much needed balance for the book. He was always ready and willing to assist with a critical eye and keep us anchored to how this book could be of benefit for patients. I would also like to thank the editors, Jane Velker, Beth Goldner, and Joyce Murphy, for understanding the complexity of the topic and for a commitment to quality over deadlines. And Tim Hiscock for finally saying that we were going to press—ready or not. I would just as soon have worked another three years on it as finish. Read more
-
Ethical Hacking
 A Beginners Guide to Ethical Hacking is a great resource for people interested in ethical (whitehat) hacking. It is targeted at „beginners”, but some „intermediate” users may find value in this book as well. Some people think that there is nothing ethical about hacking – I think that there is nothing ethical about attacking, but hacking can almost always be done ethically. Hackers are thinkers who seek to determine their limitations through challenging their skills, and this book serves to educate readers about how they can challenge themselves in an ethical way. The book starts by defining the ethical boundaries of hackers – what the cognoscenti considers too far. It then quickly jumps into the realm of programming and how code-writing can be leveraged to achieve the readers’ goals. Some might argue that programming or reverse-engineering is old school, and the new school is all about root, but just like in school, you have to start with the Introduction to classes before you can move on to the Advanced ones. Read more
A Beginners Guide to Ethical Hacking is a great resource for people interested in ethical (whitehat) hacking. It is targeted at „beginners”, but some „intermediate” users may find value in this book as well. Some people think that there is nothing ethical about hacking – I think that there is nothing ethical about attacking, but hacking can almost always be done ethically. Hackers are thinkers who seek to determine their limitations through challenging their skills, and this book serves to educate readers about how they can challenge themselves in an ethical way. The book starts by defining the ethical boundaries of hackers – what the cognoscenti considers too far. It then quickly jumps into the realm of programming and how code-writing can be leveraged to achieve the readers’ goals. Some might argue that programming or reverse-engineering is old school, and the new school is all about root, but just like in school, you have to start with the Introduction to classes before you can move on to the Advanced ones. Read more
-
Ethical Hacking and Countermeasures
 The EC-Council | Press Ethical Hacking and Countermeasures series is intended for those studying to become security officers, auditors, security professionals, site administrators, and anyone who is concerned about or responsible for the integrity of the network infrastructure. The series includes a broad base of topics in offensive network security, ethical hacking, as well as network defense and countermeasures. The content of this series is designed to immerse learners into an interactive environment where they will be shown how to scan, test, hack, and secure information systems. A wide variety of tools, viruses, and malware is presented in these books, providing a complete understanding of the tactics and tools used by hackers. By gaining a thorough understanding of how hackers operate, ethical hackers are able to set up strong countermeasures and defensive systems to protect their organizations’ critical infrastructure and information. The series, when used in its entirety, helps prepare readers to take and succeed on the C|EH certification exam from EC-Council. Read more
The EC-Council | Press Ethical Hacking and Countermeasures series is intended for those studying to become security officers, auditors, security professionals, site administrators, and anyone who is concerned about or responsible for the integrity of the network infrastructure. The series includes a broad base of topics in offensive network security, ethical hacking, as well as network defense and countermeasures. The content of this series is designed to immerse learners into an interactive environment where they will be shown how to scan, test, hack, and secure information systems. A wide variety of tools, viruses, and malware is presented in these books, providing a complete understanding of the tactics and tools used by hackers. By gaining a thorough understanding of how hackers operate, ethical hackers are able to set up strong countermeasures and defensive systems to protect their organizations’ critical infrastructure and information. The series, when used in its entirety, helps prepare readers to take and succeed on the C|EH certification exam from EC-Council. Read more
-
Exploring C++
 This book has been more difficult and time consuming than any of my previous books. I appreciate beyond words the patience of Apress and the staff who helped bring this project to fruition: particularly Matthew Moodie and Richard Dal Porto. I am especially grateful to my Technical Reviewer, Francis Glassborow, whose deep knowledge of C++ has saved me from mistakes big and small. If any technical errors remain, no doubt I introduced them too late in the editing cycle for Francis to spot them. Most of all, I thank my wife, Cheryl, whose support and encouragement sustained me when I lacked the strength to carry on. I also thank my children who put up with days and evenings without me while I finished this book. I love you all. Finally, I thank the scientists and doctors who have worked miracles in the treatment of rheumatoid arthritis, permitting me to continue to work, write, and play.
Read more
This book has been more difficult and time consuming than any of my previous books. I appreciate beyond words the patience of Apress and the staff who helped bring this project to fruition: particularly Matthew Moodie and Richard Dal Porto. I am especially grateful to my Technical Reviewer, Francis Glassborow, whose deep knowledge of C++ has saved me from mistakes big and small. If any technical errors remain, no doubt I introduced them too late in the editing cycle for Francis to spot them. Most of all, I thank my wife, Cheryl, whose support and encouragement sustained me when I lacked the strength to carry on. I also thank my children who put up with days and evenings without me while I finished this book. I love you all. Finally, I thank the scientists and doctors who have worked miracles in the treatment of rheumatoid arthritis, permitting me to continue to work, write, and play.
Read more
-
Foundation Mathematics
 Foundations of mathematics is the study of the philosophical and logical[1] and/or algorithmic basis of mathematics, or, in a broader sense, the mathematical investigation of what underlies the philosophical theories concerning the nature of mathematics.[2] In this latter sense, the distinction between foundations of mathematics and philosophy of mathematics turns out to be quite vague. Foundations of mathematics can be conceived as the study of the basic mathematical concepts (number, geometrical figure, set, function, etc.) and how they form hierarchies of more complex structures and concepts, especially the fundamentally important structures that form the language of mathematics (formulas, theories and their models giving a meaning to formulas, definitions, proofs, algorithms, etc.) also called metamathematical concepts, with an eye to the philosophical aspects and the unity of mathematics. The search for foundations of mathematics is a central question of the philosophy of mathematics; the abstract nature of mathematical objects presents special philosophical challenges Read more
Foundations of mathematics is the study of the philosophical and logical[1] and/or algorithmic basis of mathematics, or, in a broader sense, the mathematical investigation of what underlies the philosophical theories concerning the nature of mathematics.[2] In this latter sense, the distinction between foundations of mathematics and philosophy of mathematics turns out to be quite vague. Foundations of mathematics can be conceived as the study of the basic mathematical concepts (number, geometrical figure, set, function, etc.) and how they form hierarchies of more complex structures and concepts, especially the fundamentally important structures that form the language of mathematics (formulas, theories and their models giving a meaning to formulas, definitions, proofs, algorithms, etc.) also called metamathematical concepts, with an eye to the philosophical aspects and the unity of mathematics. The search for foundations of mathematics is a central question of the philosophy of mathematics; the abstract nature of mathematical objects presents special philosophical challenges Read more
-
FTP Exploits
 This discusses one of many possible uses of the "FTP server bounce attack". The mechanism used is probably well-known, but to date interest in detailing or fixing it seems low to nonexistent. This particular example demonstrates yet another way in which most electronically enforced "export restrictions" are completely useless and trivial to bypass. It is chosen in an effort to make the reader sit up and notice that there are some really ill-conceived aspects of the standard FTP protocol.
Read more
This discusses one of many possible uses of the "FTP server bounce attack". The mechanism used is probably well-known, but to date interest in detailing or fixing it seems low to nonexistent. This particular example demonstrates yet another way in which most electronically enforced "export restrictions" are completely useless and trivial to bypass. It is chosen in an effort to make the reader sit up and notice that there are some really ill-conceived aspects of the standard FTP protocol.
Read more
-
General Mathematics
 Mathematics (from Greek ?????? máth?ma, “knowledge, study, learning”) is the study of topics such as quantity (numbers),[2] structure,[3] space,[2] and change.[4][5][6] There is a range of views among mathematicians and philosophers as to the exact scope and definition of mathematics.[7][8]
Mathematicians seek out patterns[9][10] and use them to formulate new conjectures. Mathematicians resolve the truth or falsity of conjectures by mathematical proof. When mathematical structures are good models of real phenomena, then mathematical reasoning can provide insight or predictions about nature. Through the use of abstraction and logic, mathematics developed from counting, calculation, measurement, and the systematic study of the shapes and motions of physical objects. Practical mathematics has been a human activity from as far back as written records exist. The research required to solve mathematical problems can take years or even centuries of sustained inquiry. Read more
Mathematics (from Greek ?????? máth?ma, “knowledge, study, learning”) is the study of topics such as quantity (numbers),[2] structure,[3] space,[2] and change.[4][5][6] There is a range of views among mathematicians and philosophers as to the exact scope and definition of mathematics.[7][8]
Mathematicians seek out patterns[9][10] and use them to formulate new conjectures. Mathematicians resolve the truth or falsity of conjectures by mathematical proof. When mathematical structures are good models of real phenomena, then mathematical reasoning can provide insight or predictions about nature. Through the use of abstraction and logic, mathematics developed from counting, calculation, measurement, and the systematic study of the shapes and motions of physical objects. Practical mathematics has been a human activity from as far back as written records exist. The research required to solve mathematical problems can take years or even centuries of sustained inquiry. Read more
-
Geology
 Geology (from the Ancient Greek ??, g?, i.e. "earth" and -?o???, -logia, i.e. "study of, discourse"[1][2]) is an earth science concerned with the solid Earth, the rocks of which it is composed, and the processes by which they change over time. Geology can also refer generally to the study of the solid features of any terrestrial planet (such as the geology of the Moon or Mars).
Geology gives insight into the history of the Earth by providing the primary evidence for plate tectonics, the evolutionary history of life, and past climates. Geology is important for mineral and hydrocarbon exploration and exploitation, evaluating water resources, understanding of natural hazards, the remediation of environmental problems, and for providing insights into past climate change. Geology also plays a role in geotechnical engineering and is a major academic discipline. Read more
Geology (from the Ancient Greek ??, g?, i.e. "earth" and -?o???, -logia, i.e. "study of, discourse"[1][2]) is an earth science concerned with the solid Earth, the rocks of which it is composed, and the processes by which they change over time. Geology can also refer generally to the study of the solid features of any terrestrial planet (such as the geology of the Moon or Mars).
Geology gives insight into the history of the Earth by providing the primary evidence for plate tectonics, the evolutionary history of life, and past climates. Geology is important for mineral and hydrocarbon exploration and exploitation, evaluating water resources, understanding of natural hazards, the remediation of environmental problems, and for providing insights into past climate change. Geology also plays a role in geotechnical engineering and is a major academic discipline. Read more
-
GMAT
 he Graduate Management Admission Test (GMAT (/?d?i?mæt/ (JEE-mat))) is a computer adaptive test (CAT) intended to assess certain analytical, writing, quantitative, verbal, and reading skills in written English for use in admission to a graduate management program, such as an MBA.[3] It requires knowledge of certain grammar and knowledge of certain algebra, geometry, and arithmetic. The GMAT does not measure business knowledge or skill, nor does it measure intelligence.[4] According to the test owning company, the Graduate Management Admission Council (GMAC), the GMAT assesses analytical writing and problem-solving abilities, while also addressing data sufficiency, logic, and critical reasoning skills that it believes to be vital to real-world business and management success.[5] It can be taken up to five times a year Read more
he Graduate Management Admission Test (GMAT (/?d?i?mæt/ (JEE-mat))) is a computer adaptive test (CAT) intended to assess certain analytical, writing, quantitative, verbal, and reading skills in written English for use in admission to a graduate management program, such as an MBA.[3] It requires knowledge of certain grammar and knowledge of certain algebra, geometry, and arithmetic. The GMAT does not measure business knowledge or skill, nor does it measure intelligence.[4] According to the test owning company, the Graduate Management Admission Council (GMAC), the GMAT assesses analytical writing and problem-solving abilities, while also addressing data sufficiency, logic, and critical reasoning skills that it believes to be vital to real-world business and management success.[5] It can be taken up to five times a year Read more
-
GRE
 The Graduate Record Examinations (GRE) is a standardized test that is an admissions requirement for most Graduate Schools in the United States.[7] The GRE is owned and administered by Educational Testing Service (ETS) who created it in 1949.[8] According to ETS, the GRE aims to measure verbal reasoning, quantitative reasoning, analytical writing, and critical thinking skills that have been acquired over a long period of learning. The content of the GRE consists of certain specific algebra, geometry, arithmetic, and vocabulary. The GRE General Test is offered as a computer-based exam administered at Prometric testing centers.
In the graduate school admissions process, the level of emphasis that is placed upon GRE scores varies widely between schools and between departments within schools. The importance of a GRE score can range from being a mere admission formality to an important selection factor. Read more
The Graduate Record Examinations (GRE) is a standardized test that is an admissions requirement for most Graduate Schools in the United States.[7] The GRE is owned and administered by Educational Testing Service (ETS) who created it in 1949.[8] According to ETS, the GRE aims to measure verbal reasoning, quantitative reasoning, analytical writing, and critical thinking skills that have been acquired over a long period of learning. The content of the GRE consists of certain specific algebra, geometry, arithmetic, and vocabulary. The GRE General Test is offered as a computer-based exam administered at Prometric testing centers.
In the graduate school admissions process, the level of emphasis that is placed upon GRE scores varies widely between schools and between departments within schools. The importance of a GRE score can range from being a mere admission formality to an important selection factor. Read more
-
Gynecology and Women's Health
 The book was a distillation of the teaching and practice of gynecology at the Free Hospital for Women, which was founded in 1875, and a continuation of prior texts by Dr. William Graves, the first Professor of Gynecology at Harvard Medical School. It was at the Free Hospital that John Rock collaborated with Celso Garcia and others at the Worcester Foundation in the development of the birth control pill in the 1950s. Robert W. Kistner (1917-1990) started at the Free Hospital for Women in 1952 and became an Associate Clinical Professor of Obstetrics and Gynecology in 1984. He was a very skilled and popular gynecological surgeon, endocrinologist, and teacher who distilled his knowledge of the field into this text. As the field expanded he engaged the help of colleagues for subsequent editions. The current editors are pleased to be able to carry on the tradition. We wish to express our appreciation to all of the contributors for this Seventh Edition, for their scholarship and hard work, and to acknowledge our debt to authors of prior editions that provide the foundation for the current effort. Finally we wish to recognize the able assistance of Susan Holman, Ph.D., who as manuscript coordinator had a central role in the preparation of the book with help in editing, communicating with authors and the publishers, and smooth processing of manuscripts. Read more
The book was a distillation of the teaching and practice of gynecology at the Free Hospital for Women, which was founded in 1875, and a continuation of prior texts by Dr. William Graves, the first Professor of Gynecology at Harvard Medical School. It was at the Free Hospital that John Rock collaborated with Celso Garcia and others at the Worcester Foundation in the development of the birth control pill in the 1950s. Robert W. Kistner (1917-1990) started at the Free Hospital for Women in 1952 and became an Associate Clinical Professor of Obstetrics and Gynecology in 1984. He was a very skilled and popular gynecological surgeon, endocrinologist, and teacher who distilled his knowledge of the field into this text. As the field expanded he engaged the help of colleagues for subsequent editions. The current editors are pleased to be able to carry on the tradition. We wish to express our appreciation to all of the contributors for this Seventh Edition, for their scholarship and hard work, and to acknowledge our debt to authors of prior editions that provide the foundation for the current effort. Finally we wish to recognize the able assistance of Susan Holman, Ph.D., who as manuscript coordinator had a central role in the preparation of the book with help in editing, communicating with authors and the publishers, and smooth processing of manuscripts. Read more
-
Hacking and Securing
 This book is geared toward iOS developers looking to design secure applications. This is not necessarily limited to government or financial applications, but may also pertain to applications with assets or other features that the developer is looking to protect. You’ll need a solid foundation of Objective-C coding on iOS to understand a majority of this book. A further understanding of C or assembly language will also help, but is not required. While this book primarily focuses on iOS, much of the material can also be applied directly to the Mac OS X desktop. Given that both environments run an Objective-C environment and share many of the same tools, you’ll find much of this book can be used to expose vulnerabilities in your company’s desktop applications as well. Read more
This book is geared toward iOS developers looking to design secure applications. This is not necessarily limited to government or financial applications, but may also pertain to applications with assets or other features that the developer is looking to protect. You’ll need a solid foundation of Objective-C coding on iOS to understand a majority of this book. A further understanding of C or assembly language will also help, but is not required. While this book primarily focuses on iOS, much of the material can also be applied directly to the Mac OS X desktop. Given that both environments run an Objective-C environment and share many of the same tools, you’ll find much of this book can be used to expose vulnerabilities in your company’s desktop applications as well. Read more
-
Hacking Photoshop
 Photoshop is a tough beast to tame by using logic or clicking here,there,and everywhere in the hope of breaking it in,throwing a saddle on it,and riding into the sunset. Sadly,there is no magic spell for mastering or taming Photoshop.If there were,there would be less need for books such as this one,Hacking Photoshop® CS2.No,the only sure formula that seems to work involves learning the basics and then adding to your base knowledge some of the secret handshakes known to the experts ...and that’s the raison d’être of this book.It’s written with the sole intention of imparting insider knowledge that will help you to understand what Photoshop is capable of and help you speed up your workflow by revealing some of these “secret handshakes.” Read more
Photoshop is a tough beast to tame by using logic or clicking here,there,and everywhere in the hope of breaking it in,throwing a saddle on it,and riding into the sunset. Sadly,there is no magic spell for mastering or taming Photoshop.If there were,there would be less need for books such as this one,Hacking Photoshop® CS2.No,the only sure formula that seems to work involves learning the basics and then adding to your base knowledge some of the secret handshakes known to the experts ...and that’s the raison d’être of this book.It’s written with the sole intention of imparting insider knowledge that will help you to understand what Photoshop is capable of and help you speed up your workflow by revealing some of these “secret handshakes.” Read more
-
Hacking Windows
 Windows XP is a great operating system.It is faster and more secure than any other version of Windows.However,for some,it is not fast and secure enough.By picking up this book,you have started a three-part journey that will guide you through all of the steps of customizing,optimizing for performance,and securing Windows XP.I am not talking about minor little tweaks;this book is going to show you how to conduct major surgery on your Windows XP box. Visually,Windows XP is superior to all other Windows versions.No other version of Windows has ever looked this good.So how could you make it look better? Customize it! Impress your friends and refresh your dull desktop with a cool new look.I am going to show you how to completely change the way Windows XP looks during all stages of its operation. Performance-wise,Windows XP has made great advances.However,for some computer users of older hardware,running Windows XP can be like trying to pull a 100-foot yacht behind a tiny import car.Although Windows XP will not bust your CPU quite so much as a yacht would,it can slow down the operation of your computer because there are so many new features.To help you out,I am going to show you how to get the new features under control;I’ll also tell you about some tricks that I have found to speed up the operation of Windows XP.If you already have the V12 4 x 4 of computers,and you have no problem pulling the 100-foot yacht,then you will still benefit from the performance tips. Windows XP is a lot more secure than prior Windows operating systems.However,as we all know from recent history,it has not been doing very well.This book is going to show you how to use some of the new features of Windows XP Service Pack 2,as well as many other cool security tips,to make Windows XP much securer.Congratulations on starting your journey. Your computer will be in better shape than ever in no time! Read more
Windows XP is a great operating system.It is faster and more secure than any other version of Windows.However,for some,it is not fast and secure enough.By picking up this book,you have started a three-part journey that will guide you through all of the steps of customizing,optimizing for performance,and securing Windows XP.I am not talking about minor little tweaks;this book is going to show you how to conduct major surgery on your Windows XP box. Visually,Windows XP is superior to all other Windows versions.No other version of Windows has ever looked this good.So how could you make it look better? Customize it! Impress your friends and refresh your dull desktop with a cool new look.I am going to show you how to completely change the way Windows XP looks during all stages of its operation. Performance-wise,Windows XP has made great advances.However,for some computer users of older hardware,running Windows XP can be like trying to pull a 100-foot yacht behind a tiny import car.Although Windows XP will not bust your CPU quite so much as a yacht would,it can slow down the operation of your computer because there are so many new features.To help you out,I am going to show you how to get the new features under control;I’ll also tell you about some tricks that I have found to speed up the operation of Windows XP.If you already have the V12 4 x 4 of computers,and you have no problem pulling the 100-foot yacht,then you will still benefit from the performance tips. Windows XP is a lot more secure than prior Windows operating systems.However,as we all know from recent history,it has not been doing very well.This book is going to show you how to use some of the new features of Windows XP Service Pack 2,as well as many other cool security tips,to make Windows XP much securer.Congratulations on starting your journey. Your computer will be in better shape than ever in no time! Read more
-
Hematology: Basic Principles and Practice
 an enormous amount of new scientific information has been generated in the area of hematology. This knowledge has been the result of both laboratory-based research and clinical trials. Exciting new data have been reported in virtually all areas of preclinical and clinical hematology research. This new edition serves as a resource for students, residents, fellows, scientists, and practicing physicians who are eager to learn about the science and practice of hematology. This third edition of Hematology: Basic Principles and Practice should be viewed as a work in progress; since the appearance of the first edition of this textbook in 1991, the book has evolved as it relates to content, focus, and size. This evolution reflects, in large part, the new directions and growth of hematology as an academic and clinical discipline. In order to retain the quality and vitality displayed in the first two editions, over thirty new primary authors have been added to this book. This changing of the guard is healthy for a text in order to ensure its timeliness and freshness. A significant number of new chapters appear in this volume. These new chapters represent a commitment by the editorial group to constructive change in order to create an excellent book. The authors have continued to update their chapters several times during the 24 months it has taken to complete this volume. The editors would like to thank the authors for these additional efforts, which assure that the text is up to date and comprehensive. Read more
an enormous amount of new scientific information has been generated in the area of hematology. This knowledge has been the result of both laboratory-based research and clinical trials. Exciting new data have been reported in virtually all areas of preclinical and clinical hematology research. This new edition serves as a resource for students, residents, fellows, scientists, and practicing physicians who are eager to learn about the science and practice of hematology. This third edition of Hematology: Basic Principles and Practice should be viewed as a work in progress; since the appearance of the first edition of this textbook in 1991, the book has evolved as it relates to content, focus, and size. This evolution reflects, in large part, the new directions and growth of hematology as an academic and clinical discipline. In order to retain the quality and vitality displayed in the first two editions, over thirty new primary authors have been added to this book. This changing of the guard is healthy for a text in order to ensure its timeliness and freshness. A significant number of new chapters appear in this volume. These new chapters represent a commitment by the editorial group to constructive change in order to create an excellent book. The authors have continued to update their chapters several times during the 24 months it has taken to complete this volume. The editors would like to thank the authors for these additional efforts, which assure that the text is up to date and comprehensive. Read more
-
Hibernate
 Hibernate ORM (Hibernate in short) is an object-relational mapping tool for the Java programming language. It provides a framework for mapping an object-oriented domain model to a relational database. Hibernate handles object-relational impedance mismatch problems by replacing direct, persistent database accesses with high-level object handling functions.
Hibernate is free software that is distributed under the GNU Lesser General Public License 2.1.
Hibernate's primary feature is mapping from Java classes to database tables, and mapping from Java data types to SQL data types. Hibernate also provides data query and retrieval facilities. It generates SQL calls and relieves the developer from the manual handling and object conversion of the result setHibernate ORM (Hibernate in short) is an object-relational mapping tool for the Java programming language. It provides a framework for mapping an object-oriented domain model to a relational database. Hibernate handles object-relational impedance mismatch problems by replacing direct, persistent database accesses with high-level object handling functions. Read more
Hibernate ORM (Hibernate in short) is an object-relational mapping tool for the Java programming language. It provides a framework for mapping an object-oriented domain model to a relational database. Hibernate handles object-relational impedance mismatch problems by replacing direct, persistent database accesses with high-level object handling functions.
Hibernate is free software that is distributed under the GNU Lesser General Public License 2.1.
Hibernate's primary feature is mapping from Java classes to database tables, and mapping from Java data types to SQL data types. Hibernate also provides data query and retrieval facilities. It generates SQL calls and relieves the developer from the manual handling and object conversion of the result setHibernate ORM (Hibernate in short) is an object-relational mapping tool for the Java programming language. It provides a framework for mapping an object-oriented domain model to a relational database. Hibernate handles object-relational impedance mismatch problems by replacing direct, persistent database accesses with high-level object handling functions. Read more
-
History of Mathematics
 he area of study known as the history of mathematics is primarily an investigation into the origin of discoveries in mathematics and, to a lesser extent, an investigation into the mathematical methods and notation of the past.
Before the modern age and the worldwide spread of knowledge, written examples of new mathematical developments have come to light only in a few locales. The most ancient mathematical texts available are Plimpton 322 (Babylonian c. 1900 BC),[2] the Rhind Mathematical Papyrus (Egyptian c. 2000–1800 BC)[3] and the Moscow Mathematical Papyrus (Egyptian c. 1890 BC). All of these texts concern the so-called Pythagorean theorem, which seems to be the most ancient and widespread mathematical development after basic arithmetic and geometry. Read more
he area of study known as the history of mathematics is primarily an investigation into the origin of discoveries in mathematics and, to a lesser extent, an investigation into the mathematical methods and notation of the past.
Before the modern age and the worldwide spread of knowledge, written examples of new mathematical developments have come to light only in a few locales. The most ancient mathematical texts available are Plimpton 322 (Babylonian c. 1900 BC),[2] the Rhind Mathematical Papyrus (Egyptian c. 2000–1800 BC)[3] and the Moscow Mathematical Papyrus (Egyptian c. 1890 BC). All of these texts concern the so-called Pythagorean theorem, which seems to be the most ancient and widespread mathematical development after basic arithmetic and geometry. Read more
-
HTML Guidelines for Web Developers
 In this book, we give you extensive insight into the new possibilities of HTML5. In addition to the classic specification components, such as video, audio, canvas, intelligent forms, offline applications, and microdata (to name but a few), this overview also includes topics in the immediate context of HTML5—for example, geolocation, web storage, WebSockets, and web workers. Numerous compact, clear, and practical examples illustrate the new elements and techniques in HTML5. There is something here for everyone, whether you decide you want to construct a web log, program your own video and audio player, use the browser as a graphics program, work with geographical data, test to the limit the capacity of your browser, or prefer to live out your playful nature by trying a quiz with drag and drop or playing Battleships! with WebSockets. We also give you plenty of tips and tricks regarding JavaScript and the DOM. It is to be expected that sooner or later all browsers, in order to remain competitive in the future, will accommodate HTML5. We therefore decided not to include workarounds and compatibility libraries in most cases. In this book you will find pure HTML5, supported in our examples by at least one browser, but in most cases supported already by several manufacturers. For an up-to-date and complete reference of the new HTML elements, we refer you to the Internet. You will find the relevant links in the appropriate text passages of this book. Read more
In this book, we give you extensive insight into the new possibilities of HTML5. In addition to the classic specification components, such as video, audio, canvas, intelligent forms, offline applications, and microdata (to name but a few), this overview also includes topics in the immediate context of HTML5—for example, geolocation, web storage, WebSockets, and web workers. Numerous compact, clear, and practical examples illustrate the new elements and techniques in HTML5. There is something here for everyone, whether you decide you want to construct a web log, program your own video and audio player, use the browser as a graphics program, work with geographical data, test to the limit the capacity of your browser, or prefer to live out your playful nature by trying a quiz with drag and drop or playing Battleships! with WebSockets. We also give you plenty of tips and tricks regarding JavaScript and the DOM. It is to be expected that sooner or later all browsers, in order to remain competitive in the future, will accommodate HTML5. We therefore decided not to include workarounds and compatibility libraries in most cases. In this book you will find pure HTML5, supported in our examples by at least one browser, but in most cases supported already by several manufacturers. For an up-to-date and complete reference of the new HTML elements, we refer you to the Internet. You will find the relevant links in the appropriate text passages of this book. Read more
-
IBPS
 Institute of Banking Personnel Selection also known as IBPS[1] is a self-governing recruitment body that was started with an aim to encourage the recruitments & placements of young graduates through Personnel Selection in Public Sector Banks in India (except SBI). Apart from this, IBPS has also established its name to provide the standardized systems for assessment and result processing services to any organizations on request.
To originate its main motive, IBPS in 2011, has started the Common Written Examination to hire the skilled graduates on the reputed positions of Officers and Clerks in Indian Banks. As the time passed away, IBPS became the most ambitious recruitment journey for young graduates. Nowadays, any candidate who aspire to get a job in any of the 27 Public Sector Banks or 82 Regional Rural Banks must have qualified the IBPS Online Test followed by the Interview Process. Read more
Institute of Banking Personnel Selection also known as IBPS[1] is a self-governing recruitment body that was started with an aim to encourage the recruitments & placements of young graduates through Personnel Selection in Public Sector Banks in India (except SBI). Apart from this, IBPS has also established its name to provide the standardized systems for assessment and result processing services to any organizations on request.
To originate its main motive, IBPS in 2011, has started the Common Written Examination to hire the skilled graduates on the reputed positions of Officers and Clerks in Indian Banks. As the time passed away, IBPS became the most ambitious recruitment journey for young graduates. Nowadays, any candidate who aspire to get a job in any of the 27 Public Sector Banks or 82 Regional Rural Banks must have qualified the IBPS Online Test followed by the Interview Process. Read more
-
IELTS
 IELTS (International English Language Testing System) è un test appositamente progettato per chi vuole studiare o lavorare in un Paese di lingua inglese. È ufficialmente riconosciuto in Regno Unito, Australia, Canada, Irlanda, Sudafrica, Nuova Zelanda e Stati Uniti come verifica linguistica per l'ammissione ai corsi universitari o per l'immigrazione. In Italia è gestito dal British Council. Read more
IELTS (International English Language Testing System) è un test appositamente progettato per chi vuole studiare o lavorare in un Paese di lingua inglese. È ufficialmente riconosciuto in Regno Unito, Australia, Canada, Irlanda, Sudafrica, Nuova Zelanda e Stati Uniti come verifica linguistica per l'ammissione ai corsi universitari o per l'immigrazione. In Italia è gestito dal British Council. Read more
-
Introduction to Computer Graphics Using Java 2D and 3D
 computer graphics started as a research and application ?eld that was the domain of only a few experts, for instance in the area of computer aided design (CAD). Nowadays, any person using a personal computer bene?ts from the developments in computer graphics. Operating systems and application programs with graphical user interfaces (GUIs) belong to the simplest applications of computer graphics. Visualisation techniques, ranging from simple histograms to dynamic 3D animations showing changes of winds or currents over time, use computer graphics in the same manner as popular computer games. Even those who do not use a personal computer might see the results of computer graphics on TV or in cinemas where parts of scenes or even a whole movie might be produced by computer graphics techniques. Without powerful hardware in the form of fast processors, su?ciently large memory and special graphics cards, most of these applications would not have been possible. In addition to these hardware requirements e?cient algorithms as well as programming tools that are easy to use and ?exible at the time are required. Nowadays, a standard personal computer is su?cient to generate impressive graphics and animations using freely available programming platforms like OpenGL or Java 3D. In addition to at least an elementary understanding of programming, the use of such platforms also requires basic knowledge about the underlying background, concepts and methods of computer graphics. Read more
computer graphics started as a research and application ?eld that was the domain of only a few experts, for instance in the area of computer aided design (CAD). Nowadays, any person using a personal computer bene?ts from the developments in computer graphics. Operating systems and application programs with graphical user interfaces (GUIs) belong to the simplest applications of computer graphics. Visualisation techniques, ranging from simple histograms to dynamic 3D animations showing changes of winds or currents over time, use computer graphics in the same manner as popular computer games. Even those who do not use a personal computer might see the results of computer graphics on TV or in cinemas where parts of scenes or even a whole movie might be produced by computer graphics techniques. Without powerful hardware in the form of fast processors, su?ciently large memory and special graphics cards, most of these applications would not have been possible. In addition to these hardware requirements e?cient algorithms as well as programming tools that are easy to use and ?exible at the time are required. Nowadays, a standard personal computer is su?cient to generate impressive graphics and animations using freely available programming platforms like OpenGL or Java 3D. In addition to at least an elementary understanding of programming, the use of such platforms also requires basic knowledge about the underlying background, concepts and methods of computer graphics. Read more
-
INTRODUCTION TO PROTEOMICS
 This book is an introduction to the new field of proteomics. It is intended to describe how proteins and proteomes can be analyzed and studied. Despite widespread, growing interest in proteomics, an understanding of proteomics tools and technologies is only slowly penetrating the research community at large. This book addresses the need to introduce biologists to new tools and approaches, and is for both students of biology and experienced, practicing biologists. Anyone who has taken a graduate level biochemistry course should be able to take from this book a reasonable understanding of what proteomics is all about and how it is practiced. The experienced biologist should encounter much here that is familiar, but refocused to facilitate studies of the proteome. The achievement of long-sought milestones in genome sequencing, analytical instrumentation, computing power, and user-friendly software tools has irrevocably changed the practice of biology. After years of studying the individual components of living systems, we can now study the systems themselves in comprehensive scope and in exquisite molecular detail. We therefore face the tasks of effectively employing new technologies, of dealing with mountains of data, and, most important, of adjusting our thinking to understand complex systems as opposed to their individual components.
Read more
This book is an introduction to the new field of proteomics. It is intended to describe how proteins and proteomes can be analyzed and studied. Despite widespread, growing interest in proteomics, an understanding of proteomics tools and technologies is only slowly penetrating the research community at large. This book addresses the need to introduce biologists to new tools and approaches, and is for both students of biology and experienced, practicing biologists. Anyone who has taken a graduate level biochemistry course should be able to take from this book a reasonable understanding of what proteomics is all about and how it is practiced. The experienced biologist should encounter much here that is familiar, but refocused to facilitate studies of the proteome. The achievement of long-sought milestones in genome sequencing, analytical instrumentation, computing power, and user-friendly software tools has irrevocably changed the practice of biology. After years of studying the individual components of living systems, we can now study the systems themselves in comprehensive scope and in exquisite molecular detail. We therefore face the tasks of effectively employing new technologies, of dealing with mountains of data, and, most important, of adjusting our thinking to understand complex systems as opposed to their individual components.
Read more
-
IT Auditing
 IT audits have focused on enterprise systems using enterprise-based tools. As enterprise systems move to outsourced and cloud-based services, new cloud-based tools are needed to audit these distributed systems. Either enterprise vendors will rewrite their tools to address cloud-based systems or new and existing cloud-based tools will be used to assist auditors with these distributed systems. The book gives good insights on how to address these new challenges and provides recommendations on auditing cloud-based services.”
Read more
IT audits have focused on enterprise systems using enterprise-based tools. As enterprise systems move to outsourced and cloud-based services, new cloud-based tools are needed to audit these distributed systems. Either enterprise vendors will rewrite their tools to address cloud-based systems or new and existing cloud-based tools will be used to assist auditors with these distributed systems. The book gives good insights on how to address these new challenges and provides recommendations on auditing cloud-based services.”
Read more
-
J2EE Handbook
 This handbook is a concise guide to architecting, designing and building J2EE applications. This handbook will guide the technical architect through the entire J2EE project including identifying business requirements, performing use-case analysis, object and data modeling, and guiding a development team during construction. Whether you are about to architect your first J2EE application or are looking for ways to keep your projects on-time and on-budget, you will refer to this handbook again and again.
Read more
This handbook is a concise guide to architecting, designing and building J2EE applications. This handbook will guide the technical architect through the entire J2EE project including identifying business requirements, performing use-case analysis, object and data modeling, and guiding a development team during construction. Whether you are about to architect your first J2EE application or are looking for ways to keep your projects on-time and on-budget, you will refer to this handbook again and again.
Read more
-
J2EE Open Source Toolkit
 This book is about architecture. More specifically, the book is about creating platform architecture by selecting the right components for the platform, combining them, and making certain that all of the integrated components work together. It is also about open source Java and the components that can be selected to build the platform. The purpose of this book is to enable you to select and assemble various open source components needed to demonstrate and build applications using Java 2 Enterprise Edition (J2EE) technologies by creating a Java platform that’s suitable for enterprise-class applications.
Read more
This book is about architecture. More specifically, the book is about creating platform architecture by selecting the right components for the platform, combining them, and making certain that all of the integrated components work together. It is also about open source Java and the components that can be selected to build the platform. The purpose of this book is to enable you to select and assemble various open source components needed to demonstrate and build applications using Java 2 Enterprise Edition (J2EE) technologies by creating a Java platform that’s suitable for enterprise-class applications.
Read more
-
J2ME (Java 2 Micro Edition)
 Micro Edition or Java ME is a computing platform for development and deployment of portable code for embedded and mobile devices (micro-controllers, sensors, gateways, mobile phones, personal digital assistants, TV set-top boxes, printers).[1] Java ME was formerly known as Java 2 Platform, Micro Edition or J2ME.
The platform uses the object-oriented Java programming language. It is part of the Java software-platform family. Java ME was designed by Sun Microsystems, acquired by Oracle Corporation in 2010; the platform replaced[when?] a similar technology, PersonalJava. Originally developed under the Java Community Process as JSR 68, the different flavors of Java ME have evolved in separate JSRs. Sun provides a reference implementation of the specification, but has tended not to provide free binary implementations of its Java ME runtime environment for mobile devices, rather relying on third parties to provide their own. Read more
Micro Edition or Java ME is a computing platform for development and deployment of portable code for embedded and mobile devices (micro-controllers, sensors, gateways, mobile phones, personal digital assistants, TV set-top boxes, printers).[1] Java ME was formerly known as Java 2 Platform, Micro Edition or J2ME.
The platform uses the object-oriented Java programming language. It is part of the Java software-platform family. Java ME was designed by Sun Microsystems, acquired by Oracle Corporation in 2010; the platform replaced[when?] a similar technology, PersonalJava. Originally developed under the Java Community Process as JSR 68, the different flavors of Java ME have evolved in separate JSRs. Sun provides a reference implementation of the specification, but has tended not to provide free binary implementations of its Java ME runtime environment for mobile devices, rather relying on third parties to provide their own. Read more
-
J2ME: The Complete Reference
 Java technology has evolved from a programming language designed to create machine-independent embedded systems into a robust, vendor-independent, machine-independent, server-side technology, enabling the corporate community to realize the full potential of web-centric applications. JavabeganwiththereleaseoftheJavaDevelopmentKit(JDK).Itwasobviousfrom the start that Java was on a fast track to becoming a solution to the problems of many corporate systems. More interface and libraries were extended in the JDK as the corporate world demanded—and received—application programming interfaces (API) that addressed real-world situations. JDK API extensions fully integrated into the JDK with the release of the Java 2 StandardEdition(J2SE)oftheJDK.J2SEcontainsalltheAPIsneededtobuildindustrial strength Java applications. However, the corporate world felt J2SE lacked the strength required for developing enterprise-wide applications and for servicing the needs of developers of mobile and embedded systems. Again the corporate community pushed Sun Microsystems, Inc. to revise Java technology to address needs of an enterprise. Sun Microsystems, Inc. then launched the Java Community Program (JCP) that brought together corporate users, vendors, and technologists to develop a standard for enterprise Java APIs Read more
Java technology has evolved from a programming language designed to create machine-independent embedded systems into a robust, vendor-independent, machine-independent, server-side technology, enabling the corporate community to realize the full potential of web-centric applications. JavabeganwiththereleaseoftheJavaDevelopmentKit(JDK).Itwasobviousfrom the start that Java was on a fast track to becoming a solution to the problems of many corporate systems. More interface and libraries were extended in the JDK as the corporate world demanded—and received—application programming interfaces (API) that addressed real-world situations. JDK API extensions fully integrated into the JDK with the release of the Java 2 StandardEdition(J2SE)oftheJDK.J2SEcontainsalltheAPIsneededtobuildindustrial strength Java applications. However, the corporate world felt J2SE lacked the strength required for developing enterprise-wide applications and for servicing the needs of developers of mobile and embedded systems. Again the corporate community pushed Sun Microsystems, Inc. to revise Java technology to address needs of an enterprise. Sun Microsystems, Inc. then launched the Java Community Program (JCP) that brought together corporate users, vendors, and technologists to develop a standard for enterprise Java APIs Read more
-
Java 2 micro edition
 Java Platform, Micro Edition (Java ME) provides a robust, flexible environment for applications running on embedded and mobile devices in the Internet of Things: micro-controllers, sensors, gateways, mobile phones, personal digital assistants (PDAs), TV set-top boxes, printers and more. Java ME includes flexible user interfaces, robust security, built-in network protocols, and support for networked and offline applications that can be downloaded dynamically. Applications based on Java ME are portable across many devices, yet leverage each device's native capabilities. Read more
Java Platform, Micro Edition (Java ME) provides a robust, flexible environment for applications running on embedded and mobile devices in the Internet of Things: micro-controllers, sensors, gateways, mobile phones, personal digital assistants (PDAs), TV set-top boxes, printers and more. Java ME includes flexible user interfaces, robust security, built-in network protocols, and support for networked and offline applications that can be downloaded dynamically. Applications based on Java ME are portable across many devices, yet leverage each device's native capabilities. Read more
-
Java Business Component Developer
 Primarily written for developers who know basic Java and want to pass the Sun Certified Business Component Developer exam CX-310-090, this study kit shows how to use EJB in developing enterprise applications. With the popularity of J2EE in the enterprise, SCBCD certification is an important credential for an EJB developer to earn. Focused on the exam objectives, the content goes beyond simply ""exam-cram."" More than 130 review questions with answers distributed over all chapters and an Exam's Eye View section at the end of each chapter that emphasizes the important points in the chapter from the exam's perspective are provided. Read more
Primarily written for developers who know basic Java and want to pass the Sun Certified Business Component Developer exam CX-310-090, this study kit shows how to use EJB in developing enterprise applications. With the popularity of J2EE in the enterprise, SCBCD certification is an important credential for an EJB developer to earn. Focused on the exam objectives, the content goes beyond simply ""exam-cram."" More than 130 review questions with answers distributed over all chapters and an Exam's Eye View section at the end of each chapter that emphasizes the important points in the chapter from the exam's perspective are provided. Read more
-
Java Development with Ant
 Encompassing Java-centric software project best practices for designing and automating build, test, and deployment processes using ANT, this book is written for developers using Java in large software projects and those who have reached the limits of classic IDE development systems. Benefiting developers who apply extreme programming methodology to Java projects, this resource provides detailed coverage of ANT and explains how to use it in large projects and extend it when needed. In addition to using ANT for Java applications, it includes discussions of servlets and J2EE applications, which cover the majority of Java development projects. Read more
Encompassing Java-centric software project best practices for designing and automating build, test, and deployment processes using ANT, this book is written for developers using Java in large software projects and those who have reached the limits of classic IDE development systems. Benefiting developers who apply extreme programming methodology to Java projects, this resource provides detailed coverage of ANT and explains how to use it in large projects and extend it when needed. In addition to using ANT for Java applications, it includes discussions of servlets and J2EE applications, which cover the majority of Java development projects. Read more
-
Java On The Edge
 Enterprise Java Beans and JavaServer Pages deliver the tools you need to develop state-of-the-art multi-tier applications for the Internet or an intranet. But how do you create robust components for these two APIs--and get them to work together with each other and the rest of the containers in Java 2 Enterprise Edition? This unique guide delivers the answers. With lucid explanations and lots of sample code illustrating the development of a hotel reservation system, Lou Marco shows you step by step how to harness the power of JSP and EJB-and create cutting-edge J2EE applications
Read more
Enterprise Java Beans and JavaServer Pages deliver the tools you need to develop state-of-the-art multi-tier applications for the Internet or an intranet. But how do you create robust components for these two APIs--and get them to work together with each other and the rest of the containers in Java 2 Enterprise Edition? This unique guide delivers the answers. With lucid explanations and lots of sample code illustrating the development of a hotel reservation system, Lou Marco shows you step by step how to harness the power of JSP and EJB-and create cutting-edge J2EE applications
Read more
-
Java Persistence with Hibernate
 Hibernate is an object-relational mapping (ORM) library for the Java language, providing a framework for mapping an object-oriented domain model to a traditional relational database. Hibernate solves object-relational impedance mismatch problems by replacing direct persistence-related database accesses with high-level object handling functions.
Hibernate is free as open source software that is distributed under the GNU Lesser General Public License.
Hibernate's primary feature is mapping from Java classes to database tables (and from Java data types to SQL data types). Hibernate also provides data query and retrieval facilities. Hibernate generates the SQL calls and relieves the developer from manual result set handling and object conversion, keeping the application portable to all supported SQL databases, with database portability delivered at very little performance overhead. Read more
Hibernate is an object-relational mapping (ORM) library for the Java language, providing a framework for mapping an object-oriented domain model to a traditional relational database. Hibernate solves object-relational impedance mismatch problems by replacing direct persistence-related database accesses with high-level object handling functions.
Hibernate is free as open source software that is distributed under the GNU Lesser General Public License.
Hibernate's primary feature is mapping from Java classes to database tables (and from Java data types to SQL data types). Hibernate also provides data query and retrieval facilities. Hibernate generates the SQL calls and relieves the developer from manual result set handling and object conversion, keeping the application portable to all supported SQL databases, with database portability delivered at very little performance overhead. Read more
-
Java Programmig
 Java Programming, Sixth Edition provides the beginning programmer with a guide to developing applications using the Java programming language. Java is popular among professional programmers because it can be used to build visually interesting graphical user interface (GUI) and Web-based applications. Java also provides an excellent environment for the beginning programmer—a student quickly can build useful programs while learning the basics of structured and object-oriented programming techniques. This textbook assumes that you have little or no programming experience. This book provides a solid background in good object-oriented programming techniques and introduces terminology using clear, familiar language. The writing is nontechnical and emphasizes good programming practices. The examples are business examples; they do not assume a mathematical background beyond high-school business math. In addition, the examples illustrate only one or two major points; they do not contain so many features that you become lost following irrelevant and extraneous details. The explanations in this textbook are written clearly in straightforward sentences, making it easier for native and nonnative English speakers alike to master the programming concepts. Complete, working code examples appear frequently in each chapter; these examples help students make the transition from the theoretical to the practical. The code presented in each chapter can also be downloaded from the publisher’s Web site, so that students can easily run the programs and experiment with changes to them.
Read more
Java Programming, Sixth Edition provides the beginning programmer with a guide to developing applications using the Java programming language. Java is popular among professional programmers because it can be used to build visually interesting graphical user interface (GUI) and Web-based applications. Java also provides an excellent environment for the beginning programmer—a student quickly can build useful programs while learning the basics of structured and object-oriented programming techniques. This textbook assumes that you have little or no programming experience. This book provides a solid background in good object-oriented programming techniques and introduces terminology using clear, familiar language. The writing is nontechnical and emphasizes good programming practices. The examples are business examples; they do not assume a mathematical background beyond high-school business math. In addition, the examples illustrate only one or two major points; they do not contain so many features that you become lost following irrelevant and extraneous details. The explanations in this textbook are written clearly in straightforward sentences, making it easier for native and nonnative English speakers alike to master the programming concepts. Complete, working code examples appear frequently in each chapter; these examples help students make the transition from the theoretical to the practical. The code presented in each chapter can also be downloaded from the publisher’s Web site, so that students can easily run the programs and experiment with changes to them.
Read more
-
Java programming on linux
 This book is neither a course in Java programming nor a manual for the Linux OS. While the well-written text provides overviews of both Java and Linux, it's really a compendium of information you'll want on hand once you've chosen Java-on-Linux. Coverage includes: configuring your Linux desktop, a list of the Java core classes, a rundown of compilers, the Kaffe cleanroom, tidbits about Linus Torvalds and Richard Stallman, the Open Source movement, when JIT compilers are a benefit, threads, GNU, what's supported where, decompilers and obfuscators, and improved graphical rendering. This must-have book will answer your questions and provide enjoyable browsing for a long time
Read more
This book is neither a course in Java programming nor a manual for the Linux OS. While the well-written text provides overviews of both Java and Linux, it's really a compendium of information you'll want on hand once you've chosen Java-on-Linux. Coverage includes: configuring your Linux desktop, a list of the Java core classes, a rundown of compilers, the Kaffe cleanroom, tidbits about Linus Torvalds and Richard Stallman, the Open Source movement, when JIT compilers are a benefit, threads, GNU, what's supported where, decompilers and obfuscators, and improved graphical rendering. This must-have book will answer your questions and provide enjoyable browsing for a long time
Read more
-
Java Server Faces
 In JavaServer Faces, developers learn how to use the new JavaServer Faces framework to build real-world web applications. The book contains everything you'll need: how to construct the HTML on the front end; how to create the user interface components that connect the front end to your business objects; how to write a back-end that's JSFfriendly; and how to create the deployment
descriptors that tie everything together. This book is a complete guide to the crucial new JSF technology. Read more
In JavaServer Faces, developers learn how to use the new JavaServer Faces framework to build real-world web applications. The book contains everything you'll need: how to construct the HTML on the front end; how to create the user interface components that connect the front end to your business objects; how to write a back-end that's JSFfriendly; and how to create the deployment
descriptors that tie everything together. This book is a complete guide to the crucial new JSF technology. Read more
-
Javabean Development
 In order to function as a JavaBean class, an object class must obey certain conventions about method naming, construction, and behaviour. These conventions make it possible to have tools that can use, reuse, replace, and connect Java Beans.
The required conventions are as follows:
The class must have a public default constructor (with no arguments). This allows easy instantiation within editing and activation frameworks.
The class properties must be accessible using get, set, is (can be used for boolean properties instead of get), and other methods (so-called accessor methods and mutator methods) according to a standard naming convention. This allows easy automated inspection and updating of bean state within frameworks, many of which include custom editors for various types of properties. Setters can have one or more than one argument.
The class should be serializable. (This allows applications and frameworks to reliably save, store, and restore the bean's state in a manner independent of the VM and of the platform.) Read more
In order to function as a JavaBean class, an object class must obey certain conventions about method naming, construction, and behaviour. These conventions make it possible to have tools that can use, reuse, replace, and connect Java Beans.
The required conventions are as follows:
The class must have a public default constructor (with no arguments). This allows easy instantiation within editing and activation frameworks.
The class properties must be accessible using get, set, is (can be used for boolean properties instead of get), and other methods (so-called accessor methods and mutator methods) according to a standard naming convention. This allows easy automated inspection and updating of bean state within frameworks, many of which include custom editors for various types of properties. Setters can have one or more than one argument.
The class should be serializable. (This allows applications and frameworks to reliably save, store, and restore the bean's state in a manner independent of the VM and of the platform.) Read more
-
JDK 1.4
 The Java Development Kit (JDK) is an implementation of either one of the Java Platform, Standard Edition, Java Platform, Enterprise Edition, or Java Platform, Micro Edition platforms[1] released by Oracle Corporation in the form of a binary product aimed at Java developers on Solaris, Linux, macOS or Windows. The JDK includes a private JVM and a few other resources to finish the development of a Java Application.[2] Since the introduction of the Java platform, it has been by far the most widely used Software Development Kit (SDK).[citation needed] On 17 November 2006, Sun announced that they would release it under the GNU General Public License (GPL), thus making it free software. This happened in large part on 8 May 2007, when Sun contributed the source code to the OpenJDK Read more
The Java Development Kit (JDK) is an implementation of either one of the Java Platform, Standard Edition, Java Platform, Enterprise Edition, or Java Platform, Micro Edition platforms[1] released by Oracle Corporation in the form of a binary product aimed at Java developers on Solaris, Linux, macOS or Windows. The JDK includes a private JVM and a few other resources to finish the development of a Java Application.[2] Since the introduction of the Java platform, it has been by far the most widely used Software Development Kit (SDK).[citation needed] On 17 November 2006, Sun announced that they would release it under the GNU General Public License (GPL), thus making it free software. This happened in large part on 8 May 2007, when Sun contributed the source code to the OpenJDK Read more
-
JOURNALISM
 Journalism is the production and distribution of reports on the interaction of events, facts, ideas, and people that are the "news of the day" and that impacts society to at least some degree. The word applies to the occupation (professional or not), the methods of gathering information, and the organizing literary styles. Journalistic media include: print, television, radio, Internet, and, in the past, newsreels. Read more
Journalism is the production and distribution of reports on the interaction of events, facts, ideas, and people that are the "news of the day" and that impacts society to at least some degree. The word applies to the occupation (professional or not), the methods of gathering information, and the organizing literary styles. Journalistic media include: print, television, radio, Internet, and, in the past, newsreels. Read more
-
JSF 1.2 Components
 Java developers and Web designers today need more powerful tools to deliver the richer, faster, and smoother web experience that users now demand. JavaServer Faces is an advanced web application framework that includes hundreds of powerful, feature-rich, Ajax-enabled UI components that provide all of the functionality needed to build web applications in a Web 2.0 world. There has never been a better time to learn JSF. The JSF ecosystem is growing fast and the abundance of JSF components, development tools, industry conferences, and job opportunities is impressive. Learning JSF can be a challenge, but this book makes it easy by showing you the most important JSF technologies and concepts that you need to know to become a JSF professional. Read more
Java developers and Web designers today need more powerful tools to deliver the richer, faster, and smoother web experience that users now demand. JavaServer Faces is an advanced web application framework that includes hundreds of powerful, feature-rich, Ajax-enabled UI components that provide all of the functionality needed to build web applications in a Web 2.0 world. There has never been a better time to learn JSF. The JSF ecosystem is growing fast and the abundance of JSF components, development tools, industry conferences, and job opportunities is impressive. Learning JSF can be a challenge, but this book makes it easy by showing you the most important JSF technologies and concepts that you need to know to become a JSF professional. Read more
-
JSF Core
 This book is suitable for web developers whose main focus is user interface design, as well as for programmers who implement reusable components for web applications. This is in stark contrast to the of?cial JSF speci?cation, a dense and pompously worded document whose principal audience is framework implementors, as well as long-suffering book authors. The ?rst half of the book, extending to the middle of Chapter 6, focuses on the JSF tags Read more
This book is suitable for web developers whose main focus is user interface design, as well as for programmers who implement reusable components for web applications. This is in stark contrast to the of?cial JSF speci?cation, a dense and pompously worded document whose principal audience is framework implementors, as well as long-suffering book authors. The ?rst half of the book, extending to the middle of Chapter 6, focuses on the JSF tags Read more
-
JSP Tag Libraries
 JavaServer Pages Standard Tag Library (JSTL) encapsulates as simple tags the core functionality common to many Web applications. JSTL has support for common, structural tasks such as iteration and conditionals, tags for manipulating XML documents, internationalization tags, and SQL tags. It also provides a framework for integrating existing custom tags with JSTL tags. Read more
JavaServer Pages Standard Tag Library (JSTL) encapsulates as simple tags the core functionality common to many Web applications. JSTL has support for common, structural tasks such as iteration and conditionals, tags for manipulating XML documents, internationalization tags, and SQL tags. It also provides a framework for integrating existing custom tags with JSTL tags. Read more
-
JSTL in Action
 JSTL in Action shows you how to write rich, dynamic web pages without programming. From simple loops to tricky XML processing, every feature of JSTL is covered and exercised in numerous useful examples. Whether you are a novice page author or an experienced Javaprogrammer, this book shows you easy ways to create powerful web sites.
Read more
JSTL in Action shows you how to write rich, dynamic web pages without programming. From simple loops to tricky XML processing, every feature of JSTL is covered and exercised in numerous useful examples. Whether you are a novice page author or an experienced Javaprogrammer, this book shows you easy ways to create powerful web sites.
Read more
-
Linux
 The development of Linux is one of the most prominent examples of free and open-source software collaboration. The underlying source code may be used, modified and distributed?—?commercially or non-commercially?—?by anyone under the terms of its respective licenses, such as the GNU General Public License. Typically, Linux is packagedin a form known as a Linux distribution (or distro for short) for both desktop and server use. Some of the most popular mainstream Linux distributions[29][30][31] are Arch Linux, CentOS, Debian, Fedora, Gentoo Linux, Linux Mint, Mageia, openSUSE and Ubuntu, together with commercial distributions such as Red Hat Enterprise Linux and SUSE Linux Enterprise Server. Distributions include the Linux kernel, supporting utilities and libraries, many of which are provided by the GNU Project, and usually a large amount of application software to fulfil the distribution's intended use. Read more
The development of Linux is one of the most prominent examples of free and open-source software collaboration. The underlying source code may be used, modified and distributed?—?commercially or non-commercially?—?by anyone under the terms of its respective licenses, such as the GNU General Public License. Typically, Linux is packagedin a form known as a Linux distribution (or distro for short) for both desktop and server use. Some of the most popular mainstream Linux distributions[29][30][31] are Arch Linux, CentOS, Debian, Fedora, Gentoo Linux, Linux Mint, Mageia, openSUSE and Ubuntu, together with commercial distributions such as Red Hat Enterprise Linux and SUSE Linux Enterprise Server. Distributions include the Linux kernel, supporting utilities and libraries, many of which are provided by the GNU Project, and usually a large amount of application software to fulfil the distribution's intended use. Read more
-
Linux Kernel Architecture
 the kernel, but required to understand what the kernel does, is encountered in this book, I will brie?y introduce you to it. To gain a more thorough understanding, however, consult the books on computing fundamentalsthat I recommend.Naturally, thereis a large selection of texts,but some booksthat I found particularly insightful and illuminating include C Programming Language, by Brian W. Kernighan and Denis M. Ritchie [KR88]; Modern Operating Systems, by Andrew S. Tanenbaum [Tan07] on the basics of operatingsystemsingeneral;OperatingSystems:DesignandImplementation,byAndrewS.Tanenbaumand Albert S. Woodhull [TW06]onUnix(Minix) inparticular; Advanced Programming in theUnix Environment, by W. Richard Stevens and Stephen A. Rago [SR05] on userspace programming; and the two volumes Computer Architecture and Computer Organization and Design, on the foundations of computer architecture by John L. Hennessy and David A. Patterson [HP06, PH07]. All have established themselves as classics in the literature. Read more
the kernel, but required to understand what the kernel does, is encountered in this book, I will brie?y introduce you to it. To gain a more thorough understanding, however, consult the books on computing fundamentalsthat I recommend.Naturally, thereis a large selection of texts,but some booksthat I found particularly insightful and illuminating include C Programming Language, by Brian W. Kernighan and Denis M. Ritchie [KR88]; Modern Operating Systems, by Andrew S. Tanenbaum [Tan07] on the basics of operatingsystemsingeneral;OperatingSystems:DesignandImplementation,byAndrewS.Tanenbaumand Albert S. Woodhull [TW06]onUnix(Minix) inparticular; Advanced Programming in theUnix Environment, by W. Richard Stevens and Stephen A. Rago [SR05] on userspace programming; and the two volumes Computer Architecture and Computer Organization and Design, on the foundations of computer architecture by John L. Hennessy and David A. Patterson [HP06, PH07]. All have established themselves as classics in the literature. Read more
-
Linux Kernel Development
 Linux kernel and the applications that use it become more widely used, we are seeing an increasing number of system software developers who wish to become involved in the development and maintenance of Linux. Some of these engineers are motivated purely by personal interest, some work for Linux companies, some work for hardware manufacturers, and some are involved with in-house development projects. But all face a common problem:The learning curve for the kernel is getting longer and steeper.The system is becoming increasingly complex, and it is very large.And as the years pass, the current members of the kernel development team gain deeper and broader knowledge of the kernel’s internals, which widens the gap between them and newcomers. I believe that this declining accessibility of the Linux source base is already a problem for the quality of the kernel, and it will become more serious over time.Those who care for Linux clearly have an interest in increasing the number of developers who can contribute to the kernel. One approach to this problem is to keep the code clean: sensible interfaces, consistent layout,“do one thing, do it well,” and so on.This is Linus Torvalds’ solution. The approach that I counsel is to liberally apply commentary to the code: words that the reader can use to understand what the coder intended to achieve at the time. (The process of identifying divergences between the intent and the implementation is known as debugging. It is hard to do this if the intent is not known.) But even code commentary does not provide the broad-sweep view of what a major subsystem is intended to do, and of how its developers set about doing it.This, the starting point of understanding, is what the written word serves best. Robert Love’s contribution provides a means by which experienced developers can gain that essential view of what services the kernel subsystems are supposed to provide, and of how they set about providing them.This will be sufficient knowledge for many people: the curious, the application developers, those who wish to evaluate the kernel’s design, and others. Read more
Linux kernel and the applications that use it become more widely used, we are seeing an increasing number of system software developers who wish to become involved in the development and maintenance of Linux. Some of these engineers are motivated purely by personal interest, some work for Linux companies, some work for hardware manufacturers, and some are involved with in-house development projects. But all face a common problem:The learning curve for the kernel is getting longer and steeper.The system is becoming increasingly complex, and it is very large.And as the years pass, the current members of the kernel development team gain deeper and broader knowledge of the kernel’s internals, which widens the gap between them and newcomers. I believe that this declining accessibility of the Linux source base is already a problem for the quality of the kernel, and it will become more serious over time.Those who care for Linux clearly have an interest in increasing the number of developers who can contribute to the kernel. One approach to this problem is to keep the code clean: sensible interfaces, consistent layout,“do one thing, do it well,” and so on.This is Linus Torvalds’ solution. The approach that I counsel is to liberally apply commentary to the code: words that the reader can use to understand what the coder intended to achieve at the time. (The process of identifying divergences between the intent and the implementation is known as debugging. It is hard to do this if the intent is not known.) But even code commentary does not provide the broad-sweep view of what a major subsystem is intended to do, and of how its developers set about doing it.This, the starting point of understanding, is what the written word serves best. Robert Love’s contribution provides a means by which experienced developers can gain that essential view of what services the kernel subsystems are supposed to provide, and of how they set about providing them.This will be sufficient knowledge for many people: the curious, the application developers, those who wish to evaluate the kernel’s design, and others. Read more
-
Linux System Administration
Books such as Linux System Administration come into existence only with the contribution of many people’s efforts. Consider it impossible to list them all here. First, we would like to thank Andy Oram, whose editing, writing, and management efforts to get this book into shape seem remarkable. Apart from working as the overall editor, Andy contributed materially to the content of this book. Andy functioned like a project manager and demonstrated both patience and discipline. We could not have asked more from the contributions of Falko Timme, Phil Howard, and Herschel Cohen. Falko lent his time and expertise to Chapters 2 and 4. Phil wrote the bulk of Chapter 11 and provided the framework for Chapter 10 and the accompanying appendix of scripts. Herschel wrote sections of several chapters, including Chapters 8 and 10, and contributed his expertise to Chapter 6. All three contributors also reviewed other parts of the book. Read more
-
Lung Cancer: Principles and Practice
 lung cancer is the leading cause of cancer-related deaths in North America and Europe, and its incidence is rising elsewhere,” ensuring an increasing number of lung cancer deaths worldwide. Unfortunately, we can substitute “remains the leading cause” for “is the leading cause.” In 1997 alone, 178,100 new lung cancer patients were diagnosed in the United States. Lung cancer is rising at an exponential rate in women and in under-served populations. Children and young adults continue to smoke in alarming proportions. Read more
lung cancer is the leading cause of cancer-related deaths in North America and Europe, and its incidence is rising elsewhere,” ensuring an increasing number of lung cancer deaths worldwide. Unfortunately, we can substitute “remains the leading cause” for “is the leading cause.” In 1997 alone, 178,100 new lung cancer patients were diagnosed in the United States. Lung cancer is rising at an exponential rate in women and in under-served populations. Children and young adults continue to smoke in alarming proportions. Read more
-
Mac mini Hacks & Mods
 If you ever stumble into some of the geekier discussion forums around the Internet, you may come across a community of people who enjoy modifying, or modding, their PCs. They’re keen on showing off how they changed the look or function of their PC using cutting, painting, and soldering techniques, or by adding stuff — some of it pretty weird — that isn’t normally there.
There is a software equivalent of modding: hacking. This is programming changes in software to make it look different or to make it do something it wasn’t designed to.
There is also a third type of computer change: using your computer for a radically different purpose, hacking your perception of what a computer is, or modding your noncomputer possessions to fit the computer.
The mini was tailor-made for all three of these types of changes. Oh sure, Apple wants you to think that the mini is perfect and complete the way it is. But then, this isn’t the book that Apple wanted me to write Read more
If you ever stumble into some of the geekier discussion forums around the Internet, you may come across a community of people who enjoy modifying, or modding, their PCs. They’re keen on showing off how they changed the look or function of their PC using cutting, painting, and soldering techniques, or by adding stuff — some of it pretty weird — that isn’t normally there.
There is a software equivalent of modding: hacking. This is programming changes in software to make it look different or to make it do something it wasn’t designed to.
There is also a third type of computer change: using your computer for a radically different purpose, hacking your perception of what a computer is, or modding your noncomputer possessions to fit the computer.
The mini was tailor-made for all three of these types of changes. Oh sure, Apple wants you to think that the mini is perfect and complete the way it is. But then, this isn’t the book that Apple wanted me to write Read more
-
Manual of Outpatient Gynecology
 Manual of Outpatient Gynecology, Fourth Edition, is a practical text designed to aid in the treatment of outpatient gynecologic problems. It is meant to emphasize office diagnosis and treatment for the most frequently encountered problems and various sensitive subjects encountered in office medicine.
Women are often the health care monitors for family members and frequently ask questions regarding different age groups. Since there is a heightened interest in herbal and vitamin remedies, various “natural” treatments have been added to several chapters throughout the manual, and a chapter has been devoted to complimentary and alternative medicine. The health care maintenance chapter includes updated recommendations for health care maintenance for all age groups. Discussions of inpatient management and of most surgical therapies are beyond the scope of this book Read more
Manual of Outpatient Gynecology, Fourth Edition, is a practical text designed to aid in the treatment of outpatient gynecologic problems. It is meant to emphasize office diagnosis and treatment for the most frequently encountered problems and various sensitive subjects encountered in office medicine.
Women are often the health care monitors for family members and frequently ask questions regarding different age groups. Since there is a heightened interest in herbal and vitamin remedies, various “natural” treatments have been added to several chapters throughout the manual, and a chapter has been devoted to complimentary and alternative medicine. The health care maintenance chapter includes updated recommendations for health care maintenance for all age groups. Discussions of inpatient management and of most surgical therapies are beyond the scope of this book Read more
-
Medical Embryology
 Medical Embryology adheres to the tradition established by the original publication—it provides a concise but thorough description of embryology and its clinical signi?cance, an awareness of which is essentialinthediagnosisandpreventionofbirthdefects.Recentadvancesingenetics, developmental biology, maternal-fetal medicine, and public health have signi?cantlyincreasedourknowledgeofembryologyanditsrelevance.Because birthdefectsaretheleadingcauseofinfantmortalityandamajorcontributorto disabilities,andbecausenewpreventionstrategieshavebeendeveloped,understandingtheprinciplesofembryologyisimportantforhealthcareprofessionals. Toaccomplishitsgoal,Langman’sMedicalEmbryologyretainsitsuniqueapproachofcombininganeconomyoftextwithexcellentdiagramsandscanning electron micrographs. It reinforces basic embryologic concepts by providing numerous clinical examples that result from abnormalities in developmental processes. The following pedagogic features and updates in the ninth edition help facilitate student learning:
Read more
Medical Embryology adheres to the tradition established by the original publication—it provides a concise but thorough description of embryology and its clinical signi?cance, an awareness of which is essentialinthediagnosisandpreventionofbirthdefects.Recentadvancesingenetics, developmental biology, maternal-fetal medicine, and public health have signi?cantlyincreasedourknowledgeofembryologyanditsrelevance.Because birthdefectsaretheleadingcauseofinfantmortalityandamajorcontributorto disabilities,andbecausenewpreventionstrategieshavebeendeveloped,understandingtheprinciplesofembryologyisimportantforhealthcareprofessionals. Toaccomplishitsgoal,Langman’sMedicalEmbryologyretainsitsuniqueapproachofcombininganeconomyoftextwithexcellentdiagramsandscanning electron micrographs. It reinforces basic embryologic concepts by providing numerous clinical examples that result from abnormalities in developmental processes. The following pedagogic features and updates in the ninth edition help facilitate student learning:
Read more
-
Medicine Recommendations
 Primary Care Medicine Recommendations was derived to be both a pocket handbook and a PDA application from the fourth edition of our textbook Primary Care Medicine (PCM). It is designed as a portable decision tool and provides detailed specific recommendations for the screening, workup, and management of more than 200 unique clinical problems seen in the outpatient setting. The recommendations have been organized, written, and formatted for the pocket handbook and PDA platform so that they are easily readable and readily accessible wherever and whenever you need them. Read more
Primary Care Medicine Recommendations was derived to be both a pocket handbook and a PDA application from the fourth edition of our textbook Primary Care Medicine (PCM). It is designed as a portable decision tool and provides detailed specific recommendations for the screening, workup, and management of more than 200 unique clinical problems seen in the outpatient setting. The recommendations have been organized, written, and formatted for the pocket handbook and PDA platform so that they are easily readable and readily accessible wherever and whenever you need them. Read more
-
Microsoft Visual C++
 Microsoft has turned its attention to the needs of a new generation of programmers. The changes that Microsoft has made respond to the growing need of programmers to quickly develop applications that are robust and able to work on multiple platforms. With the seamless integration of the .NET Framework, Visual C++ developers now enjoy the ability to create applications that can run under the Windows operating system, as the core of a server-side applet, or on many other platforms. This chapter begins your process of becoming a C++ programmer by covering information that orients you to the C++ language, Visual C++, and the .NET Framework. When you're finished with this chapter, you'll be ready to dive right in and create your first program. By developing this application, you'll gain a sense of the steps required to build a program and some of the strengths of developing using the Visual C++ toolset. Read more
Microsoft has turned its attention to the needs of a new generation of programmers. The changes that Microsoft has made respond to the growing need of programmers to quickly develop applications that are robust and able to work on multiple platforms. With the seamless integration of the .NET Framework, Visual C++ developers now enjoy the ability to create applications that can run under the Windows operating system, as the core of a server-side applet, or on many other platforms. This chapter begins your process of becoming a C++ programmer by covering information that orients you to the C++ language, Visual C++, and the .NET Framework. When you're finished with this chapter, you'll be ready to dive right in and create your first program. By developing this application, you'll gain a sense of the steps required to build a program and some of the strengths of developing using the Visual C++ toolset. Read more
-
Microsoft Visual Studio
 Visual Basic is a third-generation event-driven programming language and integrated development environment (IDE) from Microsoft for its Component Object Model(COM) programming model first released in 1991 and declared legacy during 2008. Microsoft intended Visual Basic to be relatively easy to learn and use.[1][2] Visual Basic was derived from BASIC, a user-friendly programming language designed for beginners, and it enables the rapid application development (RAD) of graphical user interface (GUI) applications, access to databases using Data Access Objects, Remote Data Objects, or ActiveX Data Objects, and creation of ActiveX controls and objects. Read more
Visual Basic is a third-generation event-driven programming language and integrated development environment (IDE) from Microsoft for its Component Object Model(COM) programming model first released in 1991 and declared legacy during 2008. Microsoft intended Visual Basic to be relatively easy to learn and use.[1][2] Visual Basic was derived from BASIC, a user-friendly programming language designed for beginners, and it enables the rapid application development (RAD) of graphical user interface (GUI) applications, access to databases using Data Access Objects, Remote Data Objects, or ActiveX Data Objects, and creation of ActiveX controls and objects. Read more
-
MS-SQL
 This book and its sequelInside Microsoft SQL Server 2005: T-SQL Programmingcover advanced TSQL querying, query tuning, and programming in SQL Server 2005. They are designed for programmers and DBAs who need to write and optimize code in both SQL Server 2000 and 2005. For brevity, I'll refer to the books as Inside T-SQL Querying and Inside T-SQL Programming.
The books focus on practical common problems, discussing several approaches to tackle each one. You will be introduced to many polished techniques that will enhance your toolbox and coding vocabulary, allowing you to provide efficient solutions in a natural manner. Read more
This book and its sequelInside Microsoft SQL Server 2005: T-SQL Programmingcover advanced TSQL querying, query tuning, and programming in SQL Server 2005. They are designed for programmers and DBAs who need to write and optimize code in both SQL Server 2000 and 2005. For brevity, I'll refer to the books as Inside T-SQL Querying and Inside T-SQL Programming.
The books focus on practical common problems, discussing several approaches to tackle each one. You will be introduced to many polished techniques that will enhance your toolbox and coding vocabulary, allowing you to provide efficient solutions in a natural manner. Read more
-
MY SQL
 MySQL is written in C and C++. Its SQL parser is written in yacc, but it uses a home-brewed lexical analyzer.[18] MySQL works on many system platforms, including AIX, BSDi, FreeBSD, HP-UX, eComStation, i5/OS, IRIX, Linux, macOS, Microsoft Windows, NetBSD, Novell NetWare, OpenBSD, OpenSolaris, OS/2 Warp, QNX, Oracle Solaris, Symbian, SunOS, SCO OpenServer, SCO UnixWare, Sanos and Tru64. A port of MySQL to OpenVMS also exists.[19]
The MySQL server software itself and the client libraries use dual-licensing distribution. They are offered under GPL version 2,[20] beginning from 28 June 2000[21] (which in 2009 has been extended with a FLOSSLicense Exception)[22] or to use a proprietary license. Read more
MySQL is written in C and C++. Its SQL parser is written in yacc, but it uses a home-brewed lexical analyzer.[18] MySQL works on many system platforms, including AIX, BSDi, FreeBSD, HP-UX, eComStation, i5/OS, IRIX, Linux, macOS, Microsoft Windows, NetBSD, Novell NetWare, OpenBSD, OpenSolaris, OS/2 Warp, QNX, Oracle Solaris, Symbian, SunOS, SCO OpenServer, SCO UnixWare, Sanos and Tru64. A port of MySQL to OpenVMS also exists.[19]
The MySQL server software itself and the client libraries use dual-licensing distribution. They are offered under GPL version 2,[20] beginning from 28 June 2000[21] (which in 2009 has been extended with a FLOSSLicense Exception)[22] or to use a proprietary license. Read more
-
Network Forensics
 This book would not exist without the support of two widely respected security professionals: Rob Lee and Ed Skoudis. Three years ago, Rob Lee tapped us to create the network forensics curriculum for the SANS Institute. This was the ?rst time that we pooled our joint knowledge on the subject, and actually gave that body of work a name. Since that time, Rob has continued to act as a mentor and friend, constantly pushing us to improve our work, incorporate feedback, and extend the limits of our knowledge. Rob: Thank you for your high standards, your open and honest feedback, and most of all for believing in us. We could not have accomplished this without you. Ed, in turn, encouraged us to write this book and kindly took the time to introduce us to his editor. His advice on the process proved invaluable. Thank you, Ed, for all of your help and support. We are forever grateful. Thanks to all the terri?c sta? at Pearson who put so much time and e?ort into producing this book, especially our wonderful editor, Chris Guzikowski, as well as Jessica Goldstein, Raina Chrobak, Julie Nahil, Olivia Basegio, Chris Zahn, Karen Gettman, Chuti Prasertsith, John Fuller, and Elizabeth Ryan. A very special thanks as well to the great team at Laserwords for producing this book, especially Patty Donovan for her patience and kindness. Many thanks to Jonah Elgart for creating the awesome cover illustration. We deeply appreciate the work of Dr. Dan Geer, who kindly wrote the foreword for this book. We are very grateful to our friends and colleagues who conducted technical reviews of the book: Michael Ford, Erik Hjelmvik, Randy Marchany, Craig Wright, and Joshua Wright. Their perspectives and attention to detail made this book in?nitely better.
Read more
This book would not exist without the support of two widely respected security professionals: Rob Lee and Ed Skoudis. Three years ago, Rob Lee tapped us to create the network forensics curriculum for the SANS Institute. This was the ?rst time that we pooled our joint knowledge on the subject, and actually gave that body of work a name. Since that time, Rob has continued to act as a mentor and friend, constantly pushing us to improve our work, incorporate feedback, and extend the limits of our knowledge. Rob: Thank you for your high standards, your open and honest feedback, and most of all for believing in us. We could not have accomplished this without you. Ed, in turn, encouraged us to write this book and kindly took the time to introduce us to his editor. His advice on the process proved invaluable. Thank you, Ed, for all of your help and support. We are forever grateful. Thanks to all the terri?c sta? at Pearson who put so much time and e?ort into producing this book, especially our wonderful editor, Chris Guzikowski, as well as Jessica Goldstein, Raina Chrobak, Julie Nahil, Olivia Basegio, Chris Zahn, Karen Gettman, Chuti Prasertsith, John Fuller, and Elizabeth Ryan. A very special thanks as well to the great team at Laserwords for producing this book, especially Patty Donovan for her patience and kindness. Many thanks to Jonah Elgart for creating the awesome cover illustration. We deeply appreciate the work of Dr. Dan Geer, who kindly wrote the foreword for this book. We are very grateful to our friends and colleagues who conducted technical reviews of the book: Michael Ford, Erik Hjelmvik, Randy Marchany, Craig Wright, and Joshua Wright. Their perspectives and attention to detail made this book in?nitely better.
Read more
-
Networking
 When looking at networking basics, understanding how a network operates is the first step to understanding routing, switching, and wireless. The network operates by connecting computers and peripherals using switches, routers, and access points. These devices are the essential networking basics that allow the various pieces of equipment connected to your network to communicate with one another, as well as with other networks.
Read more
When looking at networking basics, understanding how a network operates is the first step to understanding routing, switching, and wireless. The network operates by connecting computers and peripherals using switches, routers, and access points. These devices are the essential networking basics that allow the various pieces of equipment connected to your network to communicate with one another, as well as with other networks.
Read more
-
Ninja Hacking
 This work is not what most people would expect to read when they pick up a “hacking” book. Rather than showing the reader how to perform traditional penetration test attacks against networks and systems, we will be taking an unusual journey, intended to expand the mind of the reader and force them to see system and network security from a completely different perspective. Ninja Hacking provides the reader with a unique perspective of how to conduct unorthodox attacks against computing networks using disguise, espionage, stealth, and concealment. Many books on hacking discuss traditional methods used to gather information from corporate networks and systems. However, there are many infiltration techniques that are unconventional, which can yield greater access into a target network. By blending ancient practices of the Japanese ninja with current hacking methodologies, additional attack vectors can be realized. Ninja Hacking explores historical Ninjutsu techniques and relates them to realworld penetration tests and hacking efforts in a manner that expands the mindset, tools, and methods of information of security experts who are intent on covertly assaulting a target network. Read more
This work is not what most people would expect to read when they pick up a “hacking” book. Rather than showing the reader how to perform traditional penetration test attacks against networks and systems, we will be taking an unusual journey, intended to expand the mind of the reader and force them to see system and network security from a completely different perspective. Ninja Hacking provides the reader with a unique perspective of how to conduct unorthodox attacks against computing networks using disguise, espionage, stealth, and concealment. Many books on hacking discuss traditional methods used to gather information from corporate networks and systems. However, there are many infiltration techniques that are unconventional, which can yield greater access into a target network. By blending ancient practices of the Japanese ninja with current hacking methodologies, additional attack vectors can be realized. Ninja Hacking explores historical Ninjutsu techniques and relates them to realworld penetration tests and hacking efforts in a manner that expands the mindset, tools, and methods of information of security experts who are intent on covertly assaulting a target network. Read more
-
Nueroanotomy
 Neuroanatomy have endeavored 1) to provide a structural basis for understanding the function of the central nervous system; 2) to emphasize points of clinical relevance through use of appropriate terminology and examples; and 3) to integrate neuroanatomical and clinical information in a format that will meet the educational needs of the user. The goal of the sixth edition is to continue this philosophy and to present structural information and concepts in an even more clinically useful and relevant format. Information learned in the basic science setting should ?ow as seamlessly as possible into the clinical setting. I have received many constructive suggestions and comments from my colleagues and students. This is especially the case for the modi?cations made in Chapters 2, 5, 7, 8, and 9 in this new edition. The names of the individuals who have provided suggestions or comments are given in the Acknowledgments. Read more
Neuroanatomy have endeavored 1) to provide a structural basis for understanding the function of the central nervous system; 2) to emphasize points of clinical relevance through use of appropriate terminology and examples; and 3) to integrate neuroanatomical and clinical information in a format that will meet the educational needs of the user. The goal of the sixth edition is to continue this philosophy and to present structural information and concepts in an even more clinically useful and relevant format. Information learned in the basic science setting should ?ow as seamlessly as possible into the clinical setting. I have received many constructive suggestions and comments from my colleagues and students. This is especially the case for the modi?cations made in Chapters 2, 5, 7, 8, and 9 in this new edition. The names of the individuals who have provided suggestions or comments are given in the Acknowledgments. Read more
-
Number theory
 Number theory or, in older usage, arithmetic is a branch of pure mathematics devoted primarily to the study of the integers. It is sometimes called "The Queen of Mathematics" because of its foundational place in the discipline.[1] Number theorists study prime numbers as well as the properties of objects made out of integers (e.g., rational numbers) or defined as generalizations of the integers (e.g., algebraic integers). Read more
Number theory or, in older usage, arithmetic is a branch of pure mathematics devoted primarily to the study of the integers. It is sometimes called "The Queen of Mathematics" because of its foundational place in the discipline.[1] Number theorists study prime numbers as well as the properties of objects made out of integers (e.g., rational numbers) or defined as generalizations of the integers (e.g., algebraic integers). Read more
-
Oracle
 A Developer’s Guide is intended both for intermediate-level Oracle developers who are designing or coding applications in SQL and PL/SQL and for advanced PL/SQL programmers who need to learn new PL/SQL 9i features. In addition to providing developers with detailed coverage of the PS/SQL 9i language itself, author Bulusu Lakshman covers the techniques for using PL/SQL 9i for server-side applications and provides the methodology for implementing robust applications. Lakshman also mentors developers in implementing effective techniques for real-world and code-centric Oracle applications that, in the long run, will save them time and energy.
Oracle9i PL/SQL: A Developer’s Guide is a solid source for the development of Oracle9i PL/SQL applications. Developers incorporating these technologies into new applications and those migrating from earlier version will both find Lakshman’s expert treatment of the topic beneficial.
Read more
A Developer’s Guide is intended both for intermediate-level Oracle developers who are designing or coding applications in SQL and PL/SQL and for advanced PL/SQL programmers who need to learn new PL/SQL 9i features. In addition to providing developers with detailed coverage of the PS/SQL 9i language itself, author Bulusu Lakshman covers the techniques for using PL/SQL 9i for server-side applications and provides the methodology for implementing robust applications. Lakshman also mentors developers in implementing effective techniques for real-world and code-centric Oracle applications that, in the long run, will save them time and energy.
Oracle9i PL/SQL: A Developer’s Guide is a solid source for the development of Oracle9i PL/SQL applications. Developers incorporating these technologies into new applications and those migrating from earlier version will both find Lakshman’s expert treatment of the topic beneficial.
Read more
-
Pediatric Drug Reference
 Medicine has existed for thousands of years, during most of which it was an art (an area of skill and knowledge) frequently having connections to the religious and philosophical beliefs of local culture. For example, a medicine man would apply herbs and say prayers for healing, or an ancient philosopher and physician would apply bloodletting according to the theories of humorism. In recent centuries, since the advent of modern science, most medicine has become a combination of art and science (both basic and applied, under the umbrella of medical science). While stitching technique for sutures is an art learned through practice, the knowledge of what happens at the cellular and molecular level in the tissues being stitched arises through science. Read more
Medicine has existed for thousands of years, during most of which it was an art (an area of skill and knowledge) frequently having connections to the religious and philosophical beliefs of local culture. For example, a medicine man would apply herbs and say prayers for healing, or an ancient philosopher and physician would apply bloodletting according to the theories of humorism. In recent centuries, since the advent of modern science, most medicine has become a combination of art and science (both basic and applied, under the umbrella of medical science). While stitching technique for sutures is an art learned through practice, the knowledge of what happens at the cellular and molecular level in the tissues being stitched arises through science. Read more
-
Penetration Tester’s
 Penetration testing is often considered an art as much as it is a science, but even an artist needs the right brushes to do the job well. Many commercial and open source tools exist for performing penetration testing, but it’s often hard to ensure that you know what tools are available and which ones to use for a certain task. Through the next 10 chapters, we’ll be exploring the plethora of open source tools that are available to you as a penetration tester, how to use them, and in which situations they apply. Open source tools are pieces of softwarewhich are availablewith the source code so that the software can be modi?ed and improved by other interested contributors. In most cases, this software comes with a license allowing for distribution of the modi?ed software version with the requirement that the source code continue to be included with the distribution. In many cases, open source software becomes a community effort where dozens if not hundreds of people are actively contributing code and improvements to the software project. This type of project tends to result in a stronger and more valuable piece of software than what would often be developed by a single individual or small company. While commercial tools certainly exist in the penetration testing space, they’re often expensive and, in some cases, too automated to be useful for all penetration testing scenarios. There are many common situations where the open source tools that we will be talking about ?ll a need better and (obviously) more cost effectively than any commercial tool. The tools that we will be discussing throughout this book are all open source and available for you to use in your work as a penetration tester Read more
Penetration testing is often considered an art as much as it is a science, but even an artist needs the right brushes to do the job well. Many commercial and open source tools exist for performing penetration testing, but it’s often hard to ensure that you know what tools are available and which ones to use for a certain task. Through the next 10 chapters, we’ll be exploring the plethora of open source tools that are available to you as a penetration tester, how to use them, and in which situations they apply. Open source tools are pieces of softwarewhich are availablewith the source code so that the software can be modi?ed and improved by other interested contributors. In most cases, this software comes with a license allowing for distribution of the modi?ed software version with the requirement that the source code continue to be included with the distribution. In many cases, open source software becomes a community effort where dozens if not hundreds of people are actively contributing code and improvements to the software project. This type of project tends to result in a stronger and more valuable piece of software than what would often be developed by a single individual or small company. While commercial tools certainly exist in the penetration testing space, they’re often expensive and, in some cases, too automated to be useful for all penetration testing scenarios. There are many common situations where the open source tools that we will be talking about ?ll a need better and (obviously) more cost effectively than any commercial tool. The tools that we will be discussing throughout this book are all open source and available for you to use in your work as a penetration tester Read more
-
PHP
 PHP is a server-side scripting language designed primarily for web development but also used as a general-purpose programming language. Originally created by Rasmus Lerdorf in 1994,[4] the PHP reference implementation is now produced by The PHP Development Team.[5] PHP originally stood for Personal Home Page,[4] but it now stands for the recursive acronym PHP: Hypertext Preprocessor.[6]
PHP code may be embedded into HTML or HTML5 markup, or it can be used in combination with various web template systems, web content management systems and web frameworks. PHP code is usually processed by a PHP interpreter implemented as a module in the web server or as a Common Gateway Interface (CGI) executable. The web server software combines the results of the interpreted and executed PHP code, which may be any type of data, including images, with the generated web page. PHP code may also be executed with a command-line interface (CLI) and can be used to implement standalone graphical applications.[7] Read more
PHP is a server-side scripting language designed primarily for web development but also used as a general-purpose programming language. Originally created by Rasmus Lerdorf in 1994,[4] the PHP reference implementation is now produced by The PHP Development Team.[5] PHP originally stood for Personal Home Page,[4] but it now stands for the recursive acronym PHP: Hypertext Preprocessor.[6]
PHP code may be embedded into HTML or HTML5 markup, or it can be used in combination with various web template systems, web content management systems and web frameworks. PHP code is usually processed by a PHP interpreter implemented as a module in the web server or as a Common Gateway Interface (CGI) executable. The web server software combines the results of the interpreted and executed PHP code, which may be any type of data, including images, with the generated web page. PHP code may also be executed with a command-line interface (CLI) and can be used to implement standalone graphical applications.[7] Read more
-
Physics
 Physics is one of the oldest academic disciplines, perhaps the oldest through its inclusion of astronomy.[9] Over the last two millennia, physics was a part of natural philosophy along with chemistry, biology, and certain branches of mathematics, but during the scientific revolution in the 17th century, the natural sciences emerged as unique research programs in their own right.[b] Physics intersects with many interdisciplinary areas of research, such as biophysics and quantum chemistry, and the boundaries of physics are not rigidly defined. New ideas in physics often explain the fundamental mechanisms of other sciences[6] while opening new avenues of research in areas such as mathematics and philosophy Read more
Physics is one of the oldest academic disciplines, perhaps the oldest through its inclusion of astronomy.[9] Over the last two millennia, physics was a part of natural philosophy along with chemistry, biology, and certain branches of mathematics, but during the scientific revolution in the 17th century, the natural sciences emerged as unique research programs in their own right.[b] Physics intersects with many interdisciplinary areas of research, such as biophysics and quantum chemistry, and the boundaries of physics are not rigidly defined. New ideas in physics often explain the fundamental mechanisms of other sciences[6] while opening new avenues of research in areas such as mathematics and philosophy Read more
-
Political Science
 Political science, also called government,[1][2] is a social science which deals with systems of governance, and the analysis of political activities, political thoughts and political behaviour.[3] It deals extensively with the theory and practice of politics which is commonly thought of as determining of the distribution of power and resources. Political scientists "see themselves engaged in revealing the relationships underlying political events and conditions, and from these revelations they attempt to construct general principles about the way the world of politics works." Read more
Political science, also called government,[1][2] is a social science which deals with systems of governance, and the analysis of political activities, political thoughts and political behaviour.[3] It deals extensively with the theory and practice of politics which is commonly thought of as determining of the distribution of power and resources. Political scientists "see themselves engaged in revealing the relationships underlying political events and conditions, and from these revelations they attempt to construct general principles about the way the world of politics works." Read more
-
Primary Care Medicine
 Primary care is coordinated, comprehensive, and personal care, available on both a first-contact and a continuous basis. It incorporates several tasks: medical diagnosis and treatment, psychological assessment and management, personal support, communication of information about illness, prevention, and health maintenance.
This book addresses the clinical problems encountered by primary care physicians in the office practice of adult medicine. In this setting, the physician's responsibilities and tasks extend beyond the narrow technologic confines of medical diagnosis and treatment. Although a great deal of effort must be focused on accurate diagnosis and technically sound therapy, the other clinical tasks that complete the very definition of primary care also assume major importance. Read more
Primary care is coordinated, comprehensive, and personal care, available on both a first-contact and a continuous basis. It incorporates several tasks: medical diagnosis and treatment, psychological assessment and management, personal support, communication of information about illness, prevention, and health maintenance.
This book addresses the clinical problems encountered by primary care physicians in the office practice of adult medicine. In this setting, the physician's responsibilities and tasks extend beyond the narrow technologic confines of medical diagnosis and treatment. Although a great deal of effort must be focused on accurate diagnosis and technically sound therapy, the other clinical tasks that complete the very definition of primary care also assume major importance. Read more
-
Primary Care Pediatrics
 Pediatric primary care practitioners are specialists—they specialize in providing primary care to children. This includes health maintenance, disease prevention, education of new parents, helping parents to develop their parenting skills, helping children and adolescents to learn to care for themselves, identifying intra-familial stress, and teaching conflict resolution.
Pediatric providers specialize in the care of primary complaints in children, such as colds, fevers, earaches, sore throats, coughs, rashes, and minor injuries. Children are not little adults. Well-informed pediatric primary care specialists know more about the causes, microbiology, presentation, diagnosis, intricacies of management, and prognosis of middle ear disease in children than the ear, nose and throat “specialist.” Read more
Pediatric primary care practitioners are specialists—they specialize in providing primary care to children. This includes health maintenance, disease prevention, education of new parents, helping parents to develop their parenting skills, helping children and adolescents to learn to care for themselves, identifying intra-familial stress, and teaching conflict resolution.
Pediatric providers specialize in the care of primary complaints in children, such as colds, fevers, earaches, sore throats, coughs, rashes, and minor injuries. Children are not little adults. Well-informed pediatric primary care specialists know more about the causes, microbiology, presentation, diagnosis, intricacies of management, and prognosis of middle ear disease in children than the ear, nose and throat “specialist.” Read more
-
Pro Apache Struts with Ajax
 This bookwill demonstrate the use of freely available Java Open Source(JOS) development frameworks for building and deploying applications. Specifically, we will focus on the JOS development frameworks available from the Apache Software Foundation (http://apache.org) as well as its Jakarta group (http://jakarta.apache.org). While most books are heavy on explanation and light on actual code demonstration, this book emphasizes approachable code examples. The authors of this book want to provide a roadmap of JOS development tools to build your applications. Our intent in this book is not to present each of the frameworks in minute detail. Frankly, many of the development frameworks presented in this book could have entire books written about them. This book will build a simple application using the following Apache technologies, except for XDoclet: Read more
This bookwill demonstrate the use of freely available Java Open Source(JOS) development frameworks for building and deploying applications. Specifically, we will focus on the JOS development frameworks available from the Apache Software Foundation (http://apache.org) as well as its Jakarta group (http://jakarta.apache.org). While most books are heavy on explanation and light on actual code demonstration, this book emphasizes approachable code examples. The authors of this book want to provide a roadmap of JOS development tools to build your applications. Our intent in this book is not to present each of the frameworks in minute detail. Frankly, many of the development frameworks presented in this book could have entire books written about them. This book will build a simple application using the following Apache technologies, except for XDoclet: Read more
-
Pro Hibernate
 This book would not have been possible without the energy and enthusiasm of the Apress staff: especially Steve Anglin for entrusting us with the project in the first place; Beth Christmas, our Project Manager; Linda Marousek, our Copy Editor; and Katie Stence, our Production Editor. Thank you all. We are indebted to Dilip Thomas, our Technical Editor, whose timely and pithy commentary helped us to polish the rough edges of this work. The parts of the book that we are particularly proud of are usually the direct result of his notes and enquiries. Dave would like to thank his parents for entrusting the family ZX81 to his clutches some years past, and his wonderful girlfriend Kalani Seymour for her patience and enthusiasm. He would also like to thank Jeff Verdegan for his assistance with a particularly tricky example that makes an appearance in Chapter 13. Jeff would like to thank his family, Nancy, Judy, Rob, and Beth, for being supportive during the book-writing process. He’d also like to thank his friends Giuliano, Ronalyn, Roman, Karl, Michael, Jason, Valerie, Micah, and Betsy. Where this book fails to achieve its aims, we the authors are, of course, entirely responsible Read more
This book would not have been possible without the energy and enthusiasm of the Apress staff: especially Steve Anglin for entrusting us with the project in the first place; Beth Christmas, our Project Manager; Linda Marousek, our Copy Editor; and Katie Stence, our Production Editor. Thank you all. We are indebted to Dilip Thomas, our Technical Editor, whose timely and pithy commentary helped us to polish the rough edges of this work. The parts of the book that we are particularly proud of are usually the direct result of his notes and enquiries. Dave would like to thank his parents for entrusting the family ZX81 to his clutches some years past, and his wonderful girlfriend Kalani Seymour for her patience and enthusiasm. He would also like to thank Jeff Verdegan for his assistance with a particularly tricky example that makes an appearance in Chapter 13. Jeff would like to thank his family, Nancy, Judy, Rob, and Beth, for being supportive during the book-writing process. He’d also like to thank his friends Giuliano, Ronalyn, Roman, Karl, Michael, Jason, Valerie, Micah, and Betsy. Where this book fails to achieve its aims, we the authors are, of course, entirely responsible Read more
-
Pro Spring
 In this part of the book,we will introduce the Spring Framework,starting with the steps needed to download the binary and source distributions. We will next explain the Inversion of Control (IoC) patternand aspect-oriented programming (AOP).IoC and AOP lie at the heart of the Spring Framework. Toward the end of Part 1, we will show you, in full detail, various ways to configure Spring-managed beans.Finally,we will round off Part 1 with alook at some of the most important Spring design patterns
Read more
In this part of the book,we will introduce the Spring Framework,starting with the steps needed to download the binary and source distributions. We will next explain the Inversion of Control (IoC) patternand aspect-oriented programming (AOP).IoC and AOP lie at the heart of the Spring Framework. Toward the end of Part 1, we will show you, in full detail, various ways to configure Spring-managed beans.Finally,we will round off Part 1 with alook at some of the most important Spring design patterns
Read more
-
Program in C++
 Find the bugs in these broken programs and become a better programmer. Based on real-world errors, the puzzles range from easy (one wrong character) to mind twisting (errors with multiple threads). Match your wits against the author's and polish your language skills as you try to fix broken programs. Clues help along the way, and answers are provided at the back of the book.
Read more
Find the bugs in these broken programs and become a better programmer. Based on real-world errors, the puzzles range from easy (one wrong character) to mind twisting (errors with multiple threads). Match your wits against the author's and polish your language skills as you try to fix broken programs. Clues help along the way, and answers are provided at the back of the book.
Read more
-
Programming with Microsoft Visual C++ .NET
 Learn how to write solid Visual C++ .NET code today with this comprehensive reference—the latest edition of the industry’s most trusted text. It’s the complete programming guide for intermediate and advanced developers who want to create .NET applications with Visual C++ and the Microsoft .NET Framework. Focusing on core programming techniques, instructions, and solutions, this book shows you what’s new in Visual C++ .NET and walks you through the development life cycle with this powerful language. Get in-depth coverage of the language’s syntax, tools, and APIs—along with expert advice and timesaving techniques. Take advantage of complete, task-based instruction plus your Microsoft Windows and C++ programming skills to produce a new generation of killer Windows and .NET-based applications. Read more
Learn how to write solid Visual C++ .NET code today with this comprehensive reference—the latest edition of the industry’s most trusted text. It’s the complete programming guide for intermediate and advanced developers who want to create .NET applications with Visual C++ and the Microsoft .NET Framework. Focusing on core programming techniques, instructions, and solutions, this book shows you what’s new in Visual C++ .NET and walks you through the development life cycle with this powerful language. Get in-depth coverage of the language’s syntax, tools, and APIs—along with expert advice and timesaving techniques. Take advantage of complete, task-based instruction plus your Microsoft Windows and C++ programming skills to produce a new generation of killer Windows and .NET-based applications. Read more
-
Psychiatric Secrets
 Psychiatric Secrets presents an up-to-date approach to the assessment and treatment of psychiatric disorders in children, adults, and the elderly. It uses a question and answer format to address key principles in clinical practice in keeping with the concept of The Secrets Series® . The questions raise central issues and provide the organizational structure for each chapter. This process of question and answer yields a dialogue through which the expert clinicians who authored each chapter can provide their best “pearls of wisdom” often gained from years of experience as researchers, educators, and practicing clinicians.
Read more
Psychiatric Secrets presents an up-to-date approach to the assessment and treatment of psychiatric disorders in children, adults, and the elderly. It uses a question and answer format to address key principles in clinical practice in keeping with the concept of The Secrets Series® . The questions raise central issues and provide the organizational structure for each chapter. This process of question and answer yields a dialogue through which the expert clinicians who authored each chapter can provide their best “pearls of wisdom” often gained from years of experience as researchers, educators, and practicing clinicians.
Read more
-
Psychology
 psychology is "the scientific study of what makes life most worth living,"[1] or "the scientific study of positive human functioning and flourishing on multiple levels that include the biological, personal, relational, institutional, cultural, and global dimensions of life".[2] Positive psychology is concerned with eudaimonia, "the good life", reflection about what holds the greatest value in life – the factors that contribute the most to a well-lived and fulfilling life. Read more
psychology is "the scientific study of what makes life most worth living,"[1] or "the scientific study of positive human functioning and flourishing on multiple levels that include the biological, personal, relational, institutional, cultural, and global dimensions of life".[2] Positive psychology is concerned with eudaimonia, "the good life", reflection about what holds the greatest value in life – the factors that contribute the most to a well-lived and fulfilling life. Read more
-
Python
 Python is a widely used high-level programming language for general-purpose programming, created by Guido van Rossum and first released in 1991. An interpreted language, Python has a design philosophy that emphasizes code readability (notably using whitespace indentation to delimit code blocks rather than curly brackets or keywords), and a syntax that allows programmers to express concepts in fewer lines of code than might be used in languages such as C++ or Java.[22][23] The language provides constructs intended to enable writing clear programs on both a small and large scale. Read more
Python is a widely used high-level programming language for general-purpose programming, created by Guido van Rossum and first released in 1991. An interpreted language, Python has a design philosophy that emphasizes code readability (notably using whitespace indentation to delimit code blocks rather than curly brackets or keywords), and a syntax that allows programmers to express concepts in fewer lines of code than might be used in languages such as C++ or Java.[22][23] The language provides constructs intended to enable writing clear programs on both a small and large scale. Read more
-
Risk Analysis and Security
 his book contains information obtained from authentic and highly regarded sources. Reasonable efforts have been made to publish reliable data and information, but the author and publisher cannot assume responsibility for the validity of all materials or the consequences of their use. The authors and publishers have attempted to trace the copyright holders of all material reproduced in this publication and apologize to copyright holders if permission to publish in this form has not been obtained. If any copyright material has not been acknowledged please write and let us know so we may rectify in any future reprint. Except as permitted under U.S. Copyright Law, no part of this book may be reprinted, reproduced, transmitted, or utilized in any form by any electronic, mechanical, or other means, now known or hereafter invented, including photocopying, microfilming, and recording, or in any information storage or retrieval system, without written permission from the publishers. Read more
his book contains information obtained from authentic and highly regarded sources. Reasonable efforts have been made to publish reliable data and information, but the author and publisher cannot assume responsibility for the validity of all materials or the consequences of their use. The authors and publishers have attempted to trace the copyright holders of all material reproduced in this publication and apologize to copyright holders if permission to publish in this form has not been obtained. If any copyright material has not been acknowledged please write and let us know so we may rectify in any future reprint. Except as permitted under U.S. Copyright Law, no part of this book may be reprinted, reproduced, transmitted, or utilized in any form by any electronic, mechanical, or other means, now known or hereafter invented, including photocopying, microfilming, and recording, or in any information storage or retrieval system, without written permission from the publishers. Read more
-
Secure Programming
 Secure Programming Cookbook for C and C++ is an important new resource for developers serious about writing secure code for Unix® (including Linux®) and Windows® environments. This essential code companion covers a wide range of topics, including safe initialization, access control, input validation, symmetric and public key cryptography, cryptographic hashes and MACs, authentication and key exchange, PKI, random numbers, and antitampering. Read more
Secure Programming Cookbook for C and C++ is an important new resource for developers serious about writing secure code for Unix® (including Linux®) and Windows® environments. This essential code companion covers a wide range of topics, including safe initialization, access control, input validation, symmetric and public key cryptography, cryptographic hashes and MACs, authentication and key exchange, PKI, random numbers, and antitampering. Read more
-
Servlet and JSP Programming
 A Java servlet processes or stores a Java class in Java EE that conforms to the Java Servlet API,[2] a standard for implementing Java classes that respond to requests. Servlets could in principle communicate over any client–server protocol, but they are most often used with the HTTP protocol. Thus "servlet" is often used as shorthand for "HTTP servlet".[3] Thus, a software developer may use a servlet to add dynamic content to a web server using the Java platform. The generated content is commonly HTML, but may be other data such as XML. Servlets can maintain state in session variables across many server transactions by using HTTP cookies, or URL rewriting. Read more
A Java servlet processes or stores a Java class in Java EE that conforms to the Java Servlet API,[2] a standard for implementing Java classes that respond to requests. Servlets could in principle communicate over any client–server protocol, but they are most often used with the HTTP protocol. Thus "servlet" is often used as shorthand for "HTTP servlet".[3] Thus, a software developer may use a servlet to add dynamic content to a web server using the Java platform. The generated content is commonly HTML, but may be other data such as XML. Servlets can maintain state in session variables across many server transactions by using HTTP cookies, or URL rewriting. Read more
-
Smart Home Automation with Linux
 Home automation (HA) is anything that your home does for you automatically to make living there more enjoyable or productive. A smart home is one that appears to apply intelligence to make that happen. To my friends, family, and visitors, my home is both smart and automated; I can e-mail my light switches, I can receive tweets from my CD player, and I have a personalized TV guide e-mailed to me every day. To me, my home is a collection of existing open source software, some consumer-level hardware, and small pieces of glue code that make them all interact. The magic happens in the way they are combined, and it’s those secrets I’ll be exposing in this book. The most cogent phrase in this field is probably “The devil is in the details.” HA requires small confirmed tools that do a single, specific job in much the same way that Unix utility software does one job and does it well. Consequently, my decision to adopt Linux as the underlying operating system is no accident. Unlike the monolithic approach of Microsoft Windows®, there are large repositories of open source software that perform these individual jobs. SMS handling, media playback, X10 control, e-mail, web servers, speech synthesis, and everything in between is freely available—and, more importantly, interoperable. Read more
Home automation (HA) is anything that your home does for you automatically to make living there more enjoyable or productive. A smart home is one that appears to apply intelligence to make that happen. To my friends, family, and visitors, my home is both smart and automated; I can e-mail my light switches, I can receive tweets from my CD player, and I have a personalized TV guide e-mailed to me every day. To me, my home is a collection of existing open source software, some consumer-level hardware, and small pieces of glue code that make them all interact. The magic happens in the way they are combined, and it’s those secrets I’ll be exposing in this book. The most cogent phrase in this field is probably “The devil is in the details.” HA requires small confirmed tools that do a single, specific job in much the same way that Unix utility software does one job and does it well. Consequently, my decision to adopt Linux as the underlying operating system is no accident. Unlike the monolithic approach of Microsoft Windows®, there are large repositories of open source software that perform these individual jobs. SMS handling, media playback, X10 control, e-mail, web servers, speech synthesis, and everything in between is freely available—and, more importantly, interoperable. Read more
-
Spring Persistence with Hibernate
 In this book, I assume that you have a good understanding of the Java programming language, preferably version 1.5 or later, including the Java syntax and basic APIs. You are also expected to have a basic understanding of the JDBC API, relational databases, and the SQL query language. For Chapters 14, you should have a basic understanding of web development with Java, including HTML, JSP, servlets, and a web container such as Tomcat.
The book is primarily for Spring developers and users who want to persist using the popular Hibernate persistence framework. Java, Hibernate, JPA, Spring, and open source developers in general will also find the book useful Read more
In this book, I assume that you have a good understanding of the Java programming language, preferably version 1.5 or later, including the Java syntax and basic APIs. You are also expected to have a basic understanding of the JDBC API, relational databases, and the SQL query language. For Chapters 14, you should have a basic understanding of web development with Java, including HTML, JSP, servlets, and a web container such as Tomcat.
The book is primarily for Spring developers and users who want to persist using the popular Hibernate persistence framework. Java, Hibernate, JPA, Spring, and open source developers in general will also find the book useful Read more
-
SQL Injection
 Many people say they know what SQL injection is, but all they have heard about or experienced are trivial examples. SQL injection is one of the most devastating vulnerabilities to impact a business, as it can lead to exposure of all of the sensitive information stored in an application’s database, including handy information such as usernames, passwords, names, addresses, phone numbers, and credit card details. So, what exactly is SQL injection? It is the vulnerability that results when you give an attacker the ability to influence the Structured Query Language (SQL) queries that an application passes to a back-end database. By being able to influence what is passed to the database, the attacker can leverage the syntax and capabilities of SQL itself, as well as the power and flexibility of supporting database functionality and operating system functionality available to the database. SQL injection is not a vulnerability that exclusively affects Web applications; any code that accepts input from an untrusted source and then uses that input to form dynamic SQL statements could be vulnerable (e.g., “fat client” applications in a client/server architecture). Read more
Many people say they know what SQL injection is, but all they have heard about or experienced are trivial examples. SQL injection is one of the most devastating vulnerabilities to impact a business, as it can lead to exposure of all of the sensitive information stored in an application’s database, including handy information such as usernames, passwords, names, addresses, phone numbers, and credit card details. So, what exactly is SQL injection? It is the vulnerability that results when you give an attacker the ability to influence the Structured Query Language (SQL) queries that an application passes to a back-end database. By being able to influence what is passed to the database, the attacker can leverage the syntax and capabilities of SQL itself, as well as the power and flexibility of supporting database functionality and operating system functionality available to the database. SQL injection is not a vulnerability that exclusively affects Web applications; any code that accepts input from an untrusted source and then uses that input to form dynamic SQL statements could be vulnerable (e.g., “fat client” applications in a client/server architecture). Read more
-
Struts Applications
 This book was written for the intermediate to advanced Java developer who is looking at using open source development frameworks for their own projects. The authors did not spend a lot of time on introductory material regarding the Java programming language or web-based application development. This is a professional-level book that tries to address problems encountered by the software development professional in their work place. The reader should be familiar with building web applications using Java technology. In addition, a basic knowledge of design patterns is helpful Read more
This book was written for the intermediate to advanced Java developer who is looking at using open source development frameworks for their own projects. The authors did not spend a lot of time on introductory material regarding the Java programming language or web-based application development. This is a professional-level book that tries to address problems encountered by the software development professional in their work place. The reader should be familiar with building web applications using Java technology. In addition, a basic knowledge of design patterns is helpful Read more
-
Teach Yourself Java
 This book teaches Java programming from the ground up. It introduces the concepts in English instead of jargon with step-by-step examples of working programs you will create. Spend 24 hours with this book and you’ll be writing your own Java programs, confident in your ability to use the language and learn more about it. You also will have skills that are becoming increasingly important—such as network computing, graphical user interface design, and object-oriented programming. These terms might not mean much to you now. In fact, they’re probably the kind of thing that makes programming seem intimidating and difficult. However, if you can use a computer to balance your checkbook, or create a photo album on Facebook, you can write computer programs by reading Sams Teach Yourself Java in 24 Hours.
Read more
This book teaches Java programming from the ground up. It introduces the concepts in English instead of jargon with step-by-step examples of working programs you will create. Spend 24 hours with this book and you’ll be writing your own Java programs, confident in your ability to use the language and learn more about it. You also will have skills that are becoming increasingly important—such as network computing, graphical user interface design, and object-oriented programming. These terms might not mean much to you now. In fact, they’re probably the kind of thing that makes programming seem intimidating and difficult. However, if you can use a computer to balance your checkbook, or create a photo album on Facebook, you can write computer programs by reading Sams Teach Yourself Java in 24 Hours.
Read more
-
Teach yourself linux
 Linux (pronounced /?l?n?ks/ (About this sound listen) LIN-?ks[9][10] or, less frequently, /?la?n?ks/ LYN-?ks[10][11]) is a Unix-like computer operating system assembled under the model of free and open-source software development and distribution. The defining component of Linux is the Linux kernel,[12] an operating system kernel first released on September 17, 1991 by Linus Torvalds.[13][14][15] The Free Software Foundation uses the name GNU/Linux to describe the operating system, which has led to some controversy. Read more
Linux (pronounced /?l?n?ks/ (About this sound listen) LIN-?ks[9][10] or, less frequently, /?la?n?ks/ LYN-?ks[10][11]) is a Unix-like computer operating system assembled under the model of free and open-source software development and distribution. The defining component of Linux is the Linux kernel,[12] an operating system kernel first released on September 17, 1991 by Linus Torvalds.[13][14][15] The Free Software Foundation uses the name GNU/Linux to describe the operating system, which has led to some controversy. Read more
-
TEXTBOOK of CLINICAL NEUROLOGY
 Neurology is an ever-changing field. Standard safety precautions must be followed, but as new research and clinical experience broaden our knowledge, changes in treatment and drug therapy become necessary or appropriate. Readers are advised to check the product information currently provided by the manufacturer of each drug to be administered to verify the recommended dose, the method and duration of administration, and the contraindications. It is the responsibility of the treating physician, relying on experience and knowledge of the patient, to determine dosages and the best treatment for the patient. Neither the publisher nor the editor assumes any responsibility for any injury and/or damage to persons or property.
Read more
Neurology is an ever-changing field. Standard safety precautions must be followed, but as new research and clinical experience broaden our knowledge, changes in treatment and drug therapy become necessary or appropriate. Readers are advised to check the product information currently provided by the manufacturer of each drug to be administered to verify the recommended dose, the method and duration of administration, and the contraindications. It is the responsibility of the treating physician, relying on experience and knowledge of the patient, to determine dosages and the best treatment for the patient. Neither the publisher nor the editor assumes any responsibility for any injury and/or damage to persons or property.
Read more
-
The J2EE Tutorial Second Edition
 The J2EE(TM) Tutorial, Second Edition , is the complete guide to all major components of the Java 2 Platform, Enterprise Edition (J2EE) version 1.4. Written by members of the J2EE platform team at Sun Microsystems, this is the taskoriented and example-driven book that will have new and intermediate Java programmers building J2EE applications right Read more
The J2EE(TM) Tutorial, Second Edition , is the complete guide to all major components of the Java 2 Platform, Enterprise Edition (J2EE) version 1.4. Written by members of the J2EE platform team at Sun Microsystems, this is the taskoriented and example-driven book that will have new and intermediate Java programmers building J2EE applications right Read more
-
The Java EE 5 Tutorial,Third Edition
 The Java EE 5 Tutorial is an introduction to programming server-side Java applications. This book takes a task-oriented, example-driven approach to show you how to build applications for the Java EE 5 platform. This book also describes the features and functionalities available with NetBeans 5.5.
What's new in this edition? The author team have updated the existing chapters to reflect the changes to JSP, EJB, Servlets, and more. Also, the authors have added new chapters on the Sun Java System Application Server 9 as a deployment environment for server-side technologies. The web-tier technology chapters cover the components used in developing the presentation layer of a Java EE 5 or stand-alone web application. The web services technology chapters cover the APIs used in developing standard web services. The Enterprise JavaBeans (EJB) technology chapters cover the components used in developing the business logic of a Java EE 5 application. Read more
The Java EE 5 Tutorial is an introduction to programming server-side Java applications. This book takes a task-oriented, example-driven approach to show you how to build applications for the Java EE 5 platform. This book also describes the features and functionalities available with NetBeans 5.5.
What's new in this edition? The author team have updated the existing chapters to reflect the changes to JSP, EJB, Servlets, and more. Also, the authors have added new chapters on the Sun Java System Application Server 9 as a deployment environment for server-side technologies. The web-tier technology chapters cover the components used in developing the presentation layer of a Java EE 5 or stand-alone web application. The web services technology chapters cover the APIs used in developing standard web services. The Enterprise JavaBeans (EJB) technology chapters cover the components used in developing the business logic of a Java EE 5 application. Read more
-
THE DESIGN OF THE UNIX OPERATING SYSTEM
 The UNIX system was first described in a 1974 paper in the Communications of the ACM [Thompson 741 by Ken Thompson and Dennis Ritchie. Since that time, it bas become increasingly widespread and popular throughout the computer industry where more and more vendors are offering support for it on their machines. It is especially popular in universities where it is frequently used for operating systems research and case studies. Many books and papers have described parts of the system, among them, two special issues of the Bell System Technical Journal in 1978 EBST.I 781 and 1984 EBLTJ 841. Many books describe the user level interface, particularly how to use electronic mail, how to prepare documents, or how to use the command interpreter called the shell; some books such as The UNIX Programming Environment IKernighan 841 and Advanced UNIX Programming naochkind 851 describe the programming interface. This book describes the internal algorithms and structures that form the basis of the operating system (called the kernel) and their relationship to the programmer interface. It is thus applicable to several environments. First, it can be used as a textbook for an operating systems course at either the advanced undergraduate or first-year graduate level. It is most beneficial to reference the system source code when using the book, but the book can be read independently, too. Second, system programmers can use the book as a reference to gain better understanding of how the kernel works and to compare algorithms used in the UNIX system to algorithms used in other operating systems
Read more
The UNIX system was first described in a 1974 paper in the Communications of the ACM [Thompson 741 by Ken Thompson and Dennis Ritchie. Since that time, it bas become increasingly widespread and popular throughout the computer industry where more and more vendors are offering support for it on their machines. It is especially popular in universities where it is frequently used for operating systems research and case studies. Many books and papers have described parts of the system, among them, two special issues of the Bell System Technical Journal in 1978 EBST.I 781 and 1984 EBLTJ 841. Many books describe the user level interface, particularly how to use electronic mail, how to prepare documents, or how to use the command interpreter called the shell; some books such as The UNIX Programming Environment IKernighan 841 and Advanced UNIX Programming naochkind 851 describe the programming interface. This book describes the internal algorithms and structures that form the basis of the operating system (called the kernel) and their relationship to the programmer interface. It is thus applicable to several environments. First, it can be used as a textbook for an operating systems course at either the advanced undergraduate or first-year graduate level. It is most beneficial to reference the system source code when using the book, but the book can be read independently, too. Second, system programmers can use the book as a reference to gain better understanding of how the kernel works and to compare algorithms used in the UNIX system to algorithms used in other operating systems
Read more
-
The Hacker’s Handbook
 This book contains information obtained from authentic and highly regarded sources. Reprinted material is quoted with permission, and sources are indicated. A wide variety of references are listed. Reasonable efforts have been made to publish reliable data and information, but the authors and the publisher cannot assume responsibility for the validity of all materials or for the consequences of their use.
Neither this book nor any part may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, micro?lming, and recording, or by any information storage or retrieval system, without prior permission in writing from the publisher. Read more
This book contains information obtained from authentic and highly regarded sources. Reprinted material is quoted with permission, and sources are indicated. A wide variety of references are listed. Reasonable efforts have been made to publish reliable data and information, but the authors and the publisher cannot assume responsibility for the validity of all materials or for the consequences of their use.
Neither this book nor any part may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, micro?lming, and recording, or by any information storage or retrieval system, without prior permission in writing from the publisher. Read more
-
The Linux Programming inTerface
 Linux Programming Interface: A Linux and UNIX System Programming Handbook is a book written by Michael Kerrisk, which documents the APIs of the Linux kernel and of the GNU C Library (glibc).
It covers a wide array of topics dealing with the Linux operating system and operating systems in general, as well as providing a brief history of Unix and how it led to the creation of Linux. It provides many samples of code written in the C programming language, and provides learning exercises at the end of many chapters. Kerrisk is a former writer for the Linux Weekly News[1] and the current maintainer for the Linux man pages project, Read more
Linux Programming Interface: A Linux and UNIX System Programming Handbook is a book written by Michael Kerrisk, which documents the APIs of the Linux kernel and of the GNU C Library (glibc).
It covers a wide array of topics dealing with the Linux operating system and operating systems in general, as well as providing a brief history of Unix and how it led to the creation of Linux. It provides many samples of code written in the C programming language, and provides learning exercises at the end of many chapters. Kerrisk is a former writer for the Linux Weekly News[1] and the current maintainer for the Linux man pages project, Read more
-
The Little Black Book of Computer Viruses
 The Little Black Book of Computer Viruses has seen five good years in print. In those five years it has opened a door to seriously ask the question whether it is better to make technical information about computer viruses known or not. When I wrote it, it was largely an experiment. I had no idea what would happen. Would people take the viruses it contained and rewrite them to make all kinds of horrificly destructive viruses? Or would they by and large be used responsibly? At the time I wrote, no anti-virus people would even talk to me, and what I could find in print on the subject was largely unimpressive from a factual standpoint—lots of hype and fear-mongering, but very little solid research that would shed some light on what might happen if I released this book. Being a freedom loving and knowledge seeking American, I decided to go ahead and do it—write the book and get it in print. Read more
The Little Black Book of Computer Viruses has seen five good years in print. In those five years it has opened a door to seriously ask the question whether it is better to make technical information about computer viruses known or not. When I wrote it, it was largely an experiment. I had no idea what would happen. Would people take the viruses it contained and rewrite them to make all kinds of horrificly destructive viruses? Or would they by and large be used responsibly? At the time I wrote, no anti-virus people would even talk to me, and what I could find in print on the subject was largely unimpressive from a factual standpoint—lots of hype and fear-mongering, but very little solid research that would shed some light on what might happen if I released this book. Being a freedom loving and knowledge seeking American, I decided to go ahead and do it—write the book and get it in print. Read more
-
TOEFL
 Test of English as a Foreign Language, or TOEFL, is a test which measures people’s English language skills to see if they are good enough to take a course at university or graduate school in English-speaking countries. It is for people whose native language is not English. It measures how well a person uses listening, reading, speaking and writing skills to perform academic tasks. This test is accepted by more than 7,500 colleges, universities, and agencies in more than 130 countries; which means it is the most widely recognized English test in the world. Read more
Test of English as a Foreign Language, or TOEFL, is a test which measures people’s English language skills to see if they are good enough to take a course at university or graduate school in English-speaking countries. It is for people whose native language is not English. It measures how well a person uses listening, reading, speaking and writing skills to perform academic tasks. This test is accepted by more than 7,500 colleges, universities, and agencies in more than 130 countries; which means it is the most widely recognized English test in the world. Read more
-
Town planning
 The purpose of this book is to investigate ‘social planning’ with reference chiefly to the ‘social aspects of planning’ agenda within British town planning. This, inevitably, leads into a consideration of issues such as urban governance, social policy, inequality, sustainability and planning theory. This book develops further the theme of investigating the social construction of urban realities and thus of social town planning which was introduced in earlier work by the editor (Greed, 1994) and which has long intrigued the various contributors (for example, R.H. Williams, 1975, inter alia). Nowadays it may be argued that there is not one ‘town planning’ but many new ‘plannings’, each with its own agenda, devotees, and priorities, including, for example, environmental planning; urban design planning, Europlanning; and market-led urban renewal planning (cf. Greed, 1996a; Greed and Roberts, 1998). One of the most dynamic, changing and controversial of the ‘plannings’ is what may be broadly termed ‘social town planning’. There has been a proliferation of demands and policy proposals to meet the needs of minority interests and community groups, which the present scope and nature of statutory town planning appears unable, and ill-equipped, to meet. Read more
The purpose of this book is to investigate ‘social planning’ with reference chiefly to the ‘social aspects of planning’ agenda within British town planning. This, inevitably, leads into a consideration of issues such as urban governance, social policy, inequality, sustainability and planning theory. This book develops further the theme of investigating the social construction of urban realities and thus of social town planning which was introduced in earlier work by the editor (Greed, 1994) and which has long intrigued the various contributors (for example, R.H. Williams, 1975, inter alia). Nowadays it may be argued that there is not one ‘town planning’ but many new ‘plannings’, each with its own agenda, devotees, and priorities, including, for example, environmental planning; urban design planning, Europlanning; and market-led urban renewal planning (cf. Greed, 1996a; Greed and Roberts, 1998). One of the most dynamic, changing and controversial of the ‘plannings’ is what may be broadly termed ‘social town planning’. There has been a proliferation of demands and policy proposals to meet the needs of minority interests and community groups, which the present scope and nature of statutory town planning appears unable, and ill-equipped, to meet. Read more
-
Trigonometry
 Trigonometry (from Greek trig?non, "triangle" and metron, "measure"[1]) is a branch of mathematics that studies relationships involving lengths and angles of triangles. The field emerged in the Hellenistic world during the 3rd century BC from applications of geometry to astronomical studies.[2]
The 3rd-century astronomers first noted that the lengths of the sides of a right-angle triangle and the angles between those sides have fixed relationships: that is, if at least the length of one side and the value of one angle is known, then all other angles and lengths can be determined algorithmically. These calculations soon came to be defined as the trigonometric functions and today are pervasive in both pure and applied mathematics: fundamental methods of analysis such as the Fourier transform, for example, or the wave equation, use trigonometric functions to understand cyclical phenomena across many applications in fields as diverse as physics, mechanical and electrical engineering, music and acoustics, astronomy, ecology, and biology. Trigonometry is also the foundation of surveying. Read more
Trigonometry (from Greek trig?non, "triangle" and metron, "measure"[1]) is a branch of mathematics that studies relationships involving lengths and angles of triangles. The field emerged in the Hellenistic world during the 3rd century BC from applications of geometry to astronomical studies.[2]
The 3rd-century astronomers first noted that the lengths of the sides of a right-angle triangle and the angles between those sides have fixed relationships: that is, if at least the length of one side and the value of one angle is known, then all other angles and lengths can be determined algorithmically. These calculations soon came to be defined as the trigonometric functions and today are pervasive in both pure and applied mathematics: fundamental methods of analysis such as the Fourier transform, for example, or the wave equation, use trigonometric functions to understand cyclical phenomena across many applications in fields as diverse as physics, mechanical and electrical engineering, music and acoustics, astronomy, ecology, and biology. Trigonometry is also the foundation of surveying. Read more
-
Ubuntu for non-Greeks
 This newbie's guide to Ubuntu - now updated for Ubuntu 7.04 (Feisty Fawn), the latest Ubuntu release, which puts the spotlight on multimedia enablement and desktop effects - lets readers learn by doing. Using immersion-learning techniques favored by language courses, step-by-step projects build upon earlier tutorial concepts, stimulating the brain and increasing the reader's understanding. Read more
This newbie's guide to Ubuntu - now updated for Ubuntu 7.04 (Feisty Fawn), the latest Ubuntu release, which puts the spotlight on multimedia enablement and desktop effects - lets readers learn by doing. Using immersion-learning techniques favored by language courses, step-by-step projects build upon earlier tutorial concepts, stimulating the brain and increasing the reader's understanding. Read more
-
Ubuntu Linux Secrets
 Welcome to Ubuntu Linux Secrets. Like all books in the Secrets series, you can expect to find both hands-on tutorials and real-world practical application information, as well as reference and background information that provides a context for what you are learning. This book is a fairly comprehensive resource on the Ubuntu Linux distribution. By the time you have completed Ubuntu Linux Secrets you will be well-prepared to utilize your Ubuntu workstation or server to its fullest.
Read more
Welcome to Ubuntu Linux Secrets. Like all books in the Secrets series, you can expect to find both hands-on tutorials and real-world practical application information, as well as reference and background information that provides a context for what you are learning. This book is a fairly comprehensive resource on the Ubuntu Linux distribution. By the time you have completed Ubuntu Linux Secrets you will be well-prepared to utilize your Ubuntu workstation or server to its fullest.
Read more
-
Ubuntu The Complete Reference
 Ubuntu is published by Canonical Ltd, who offer commercial support.[9] It is based on free software and named after the Southern African philosophy of ubuntu(literally, 'human-ness'), which Canonical Ltd. suggests can be loosely translated as "humanity to others" or "I am what I am because of who we all are".[10] Since Ubuntu 11.04 Natty Narwhal Ubuntu has used Unity as its default user interface for the desktop, but following the release of Ubuntu 17.10 it will move to the GNOME 3desktop instead, as work on Unity ends.[11][12] Ubuntu is the most popular operating system running in hosted environments, so–called "clouds",[13] as it is the most popular server Linux distribution. Read more
Ubuntu is published by Canonical Ltd, who offer commercial support.[9] It is based on free software and named after the Southern African philosophy of ubuntu(literally, 'human-ness'), which Canonical Ltd. suggests can be loosely translated as "humanity to others" or "I am what I am because of who we all are".[10] Since Ubuntu 11.04 Natty Narwhal Ubuntu has used Unity as its default user interface for the desktop, but following the release of Ubuntu 17.10 it will move to the GNOME 3desktop instead, as work on Unity ends.[11][12] Ubuntu is the most popular operating system running in hosted environments, so–called "clouds",[13] as it is the most popular server Linux distribution. Read more
-
Ubuntu UNLEASHED
 This book is for anyone searching for guidance on using Ubuntu and primarily focuses on Intel-based PC platforms. Although the contents are aimed at intermediate to advanced users, even new users with a bit of computer savvy will benefit from the advice, tips, tricks, traps, and techniques presented in each chapter. Pointers to more detailed or related information are also provided at the end of each chapter. If you are new to Linux, you might need to learn some new computer skills, such as how to research your computer’s hardware, how to partition a hard drive, and (occasionally) how to use a command line. This book helps you learn these skills and shows you how to learn more about your computer, Linux, and the software included with Ubuntu. System administrators with experience using other operating systems can use the information in this book to install, set up, and run common Linux software services, such as the Network File System (NFS), a File Transfer Protocol (FTP) server, and a web server (using Apache, among others). Read more
This book is for anyone searching for guidance on using Ubuntu and primarily focuses on Intel-based PC platforms. Although the contents are aimed at intermediate to advanced users, even new users with a bit of computer savvy will benefit from the advice, tips, tricks, traps, and techniques presented in each chapter. Pointers to more detailed or related information are also provided at the end of each chapter. If you are new to Linux, you might need to learn some new computer skills, such as how to research your computer’s hardware, how to partition a hard drive, and (occasionally) how to use a command line. This book helps you learn these skills and shows you how to learn more about your computer, Linux, and the software included with Ubuntu. System administrators with experience using other operating systems can use the information in this book to install, set up, and run common Linux software services, such as the Network File System (NFS), a File Transfer Protocol (FTP) server, and a web server (using Apache, among others). Read more
-
Understanding the Linux Kernel
 This book would not have been written without the precious help of the many students of the school of engineering at the University of Rome "Tor Vergata" who took our course and tried to decipher the lecture notes about the Linux kernel. Their strenuous efforts to grasp the meaning of the source code led us to improve our presentation and to correct many mistakes.
Andy Oram, our wonderful editor at O'Reilly & Associates, deserves a lot of credit. He was the first at O'Reilly to believe in this project, and he spent a lot of time and energy deciphering our preliminary drafts. He also suggested many ways to make the book more readable, and he wrote several excellent introductory paragraphs. Read more
This book would not have been written without the precious help of the many students of the school of engineering at the University of Rome "Tor Vergata" who took our course and tried to decipher the lecture notes about the Linux kernel. Their strenuous efforts to grasp the meaning of the source code led us to improve our presentation and to correct many mistakes.
Andy Oram, our wonderful editor at O'Reilly & Associates, deserves a lot of credit. He was the first at O'Reilly to believe in this project, and he spent a lot of time and energy deciphering our preliminary drafts. He also suggested many ways to make the book more readable, and he wrote several excellent introductory paragraphs. Read more
-
Web Development with JavaServer Pages
 Welcome to Web Development with JavaServer Pages. This book has been written to address the needs of a wide audience of web developers. You may have only recently heard about this exciting new technology for developing dynamic web content, or perhaps you have already begun to use JavaServer Pages in your own projects. You may be a HyperText Markup Language (HTML) designer with little or no background in programming, or a seasoned Java architect. In any case, this book will show you how to use JavaServer Pages to improve the look and maintainability of dynamic web sites and web-based applications, and ease the design and development process. So, without further ado, let's begin our look at JavaServer Pages. Read more
Welcome to Web Development with JavaServer Pages. This book has been written to address the needs of a wide audience of web developers. You may have only recently heard about this exciting new technology for developing dynamic web content, or perhaps you have already begun to use JavaServer Pages in your own projects. You may be a HyperText Markup Language (HTML) designer with little or no background in programming, or a seasoned Java architect. In any case, this book will show you how to use JavaServer Pages to improve the look and maintainability of dynamic web sites and web-based applications, and ease the design and development process. So, without further ado, let's begin our look at JavaServer Pages. Read more
-
Wireless Hacking
 Welcome to the world of “wireless magic.”802.11 (Wi-Fi) wireless LANs have exploded onto the scene with an excitement not seen since the introduction of the Internet itself.Getting rid of the wires means getting rid of the hassle.With Wi-Fi,you can roam through your favorite coffee shop, boardroom or living room,all the while maintaining the convenience of high-speed connectivity. With Wi-Fi,life is good! Once you’ve gone through the experience of setting up a local Wi-Fi network,your ?rst instinct is likely to think that “bigger is better.”Expanding the coverage and increasing the network cloud enables you to share Internet resources with others as a community service.As long as you’re not breaking the law (or violating your ISP’s terms of service),you should listen to that creative instinct and start getting together with your neighbors (or others in your community) and begin planning a community wireless network! This book is all about the challenges,thrills,and adventures of such an effort,started in San Diego,and known as “SoCalFreeNet.”By offering this roadmap to you,the reader,we hope to inspire more such efforts in neighborhoods all around the world. In this chapter,we will cover some of the Wi-Fi basics you’ll need to understand in order to complete the wireless hacks found throughout this book.We start with the history and basics of 802.11, including a review of the differences between a,b and g.Next,we cover wireless architectures and FCC rules.Finally,we include some discussion on the social bene?ts of community wireless networking Read more
Welcome to the world of “wireless magic.”802.11 (Wi-Fi) wireless LANs have exploded onto the scene with an excitement not seen since the introduction of the Internet itself.Getting rid of the wires means getting rid of the hassle.With Wi-Fi,you can roam through your favorite coffee shop, boardroom or living room,all the while maintaining the convenience of high-speed connectivity. With Wi-Fi,life is good! Once you’ve gone through the experience of setting up a local Wi-Fi network,your ?rst instinct is likely to think that “bigger is better.”Expanding the coverage and increasing the network cloud enables you to share Internet resources with others as a community service.As long as you’re not breaking the law (or violating your ISP’s terms of service),you should listen to that creative instinct and start getting together with your neighbors (or others in your community) and begin planning a community wireless network! This book is all about the challenges,thrills,and adventures of such an effort,started in San Diego,and known as “SoCalFreeNet.”By offering this roadmap to you,the reader,we hope to inspire more such efforts in neighborhoods all around the world. In this chapter,we will cover some of the Wi-Fi basics you’ll need to understand in order to complete the wireless hacks found throughout this book.We start with the history and basics of 802.11, including a review of the differences between a,b and g.Next,we cover wireless architectures and FCC rules.Finally,we include some discussion on the social bene?ts of community wireless networking Read more
-
Zoology
 The history of zoology traces the study of the animal kingdom from ancient to modern times. Although the concept of zoology as a single coherent field arose much later, the zoological sciences emerged from natural history reaching back to the works of Aristotle and Galen in the ancient Greco-Roman world. This ancient work was further developed in the Middle Ages by Muslim physicians and scholars such as Albertus Magnus.[2][3][4] During the Renaissance and early modern period, zoological thought was revolutionized in Europe by a renewed interest in empiricism and the discovery of many novel organisms. Prominent in this movement were Vesalius and William Harvey, who used experimentation and careful observation in physiology, and naturalists such as Carl Linnaeus and Buffon who began to classify the diversity of life and the fossil record, as well as the development and behavior of organisms. Microscopy revealed the previously unknown world of microorganisms, laying the groundwork for cell theory.[5] The growing importance of natural theology, partly a response to the rise of mechanical philosophy, encouraged the growth of natural history (although it entrenched the argument from design). Read more
The history of zoology traces the study of the animal kingdom from ancient to modern times. Although the concept of zoology as a single coherent field arose much later, the zoological sciences emerged from natural history reaching back to the works of Aristotle and Galen in the ancient Greco-Roman world. This ancient work was further developed in the Middle Ages by Muslim physicians and scholars such as Albertus Magnus.[2][3][4] During the Renaissance and early modern period, zoological thought was revolutionized in Europe by a renewed interest in empiricism and the discovery of many novel organisms. Prominent in this movement were Vesalius and William Harvey, who used experimentation and careful observation in physiology, and naturalists such as Carl Linnaeus and Buffon who began to classify the diversity of life and the fossil record, as well as the development and behavior of organisms. Microscopy revealed the previously unknown world of microorganisms, laying the groundwork for cell theory.[5] The growing importance of natural theology, partly a response to the rise of mechanical philosophy, encouraged the growth of natural history (although it entrenched the argument from design). Read more
- Internships/ Job Assistance
- Assistance in Visa Documentation and Mock Visa interviews.
- Assistance in securing Educational loans.
- Assistance in Documentation for Admission
- Identification of Universities and Colleges
- Accommodation and Airport Pickup
- Scholarship
- Application processing and follow up.
- Selection of appropriate course as well as country.
Top Programs in Abroad!
- Work and Study program in USA
- Co-Op Program in Canada with Paid Internship
- Free Education in Germany
- Paid Internship in France
- SVP Visa process in Australia
- Study in New Zealand With Paid Internship
- Study Abroad Program
- Study in Ireland with Internship
- Study in Europe at Indian Cost
- Unique Programs Available
- Study in UK- Worlds Best Education System
- Study-Work-Settle in Ireland
- Study in Malaysia at Indian Cost
- Study and Work Singapore






































1_thumb.jpg)


1_thumb.jpg)











